Nettacker – Automated Penetration Testing Framework
Last Updated :
23 Sep, 2021
Vulnerability Scanning is the process of detection of security flaws in the Web-based Application. We can perform automated Scanning using various tools. OWaASP has a project named Nettacker which is built to automate the various phases like Information Gathering, Enumeration, Scanning, Vulnerability Scanning, etc. Along with this Nettacker tool eventually generates a report for networks, including services, bugs, vulnerabilities, misconfigurations, and other information. Nettacker tool is developed in the Python Language and available on the GitHub platform. Nettacker tool is open-source and free to use the tool. Nettacker tool supports bypassing of Firewall/IDS/IPS devices on the target server.
Note: Make Sure You have Python Installed on your System, as this is a python-based tool. Click to check the Installation process – Python Installation Steps on Linux
Installation of Nettacker Tool on Kali Linux OS
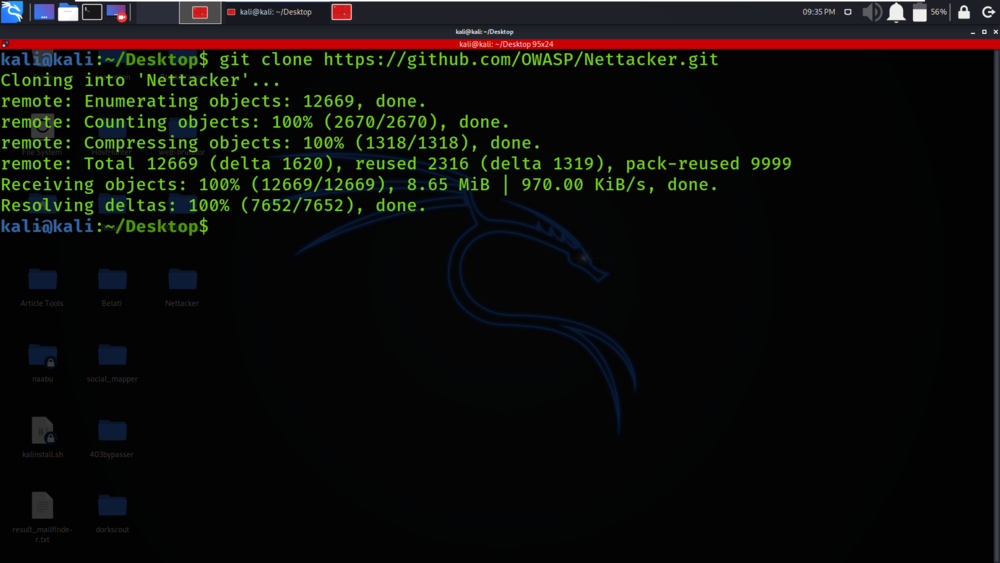
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/OWASP/Nettacker.git
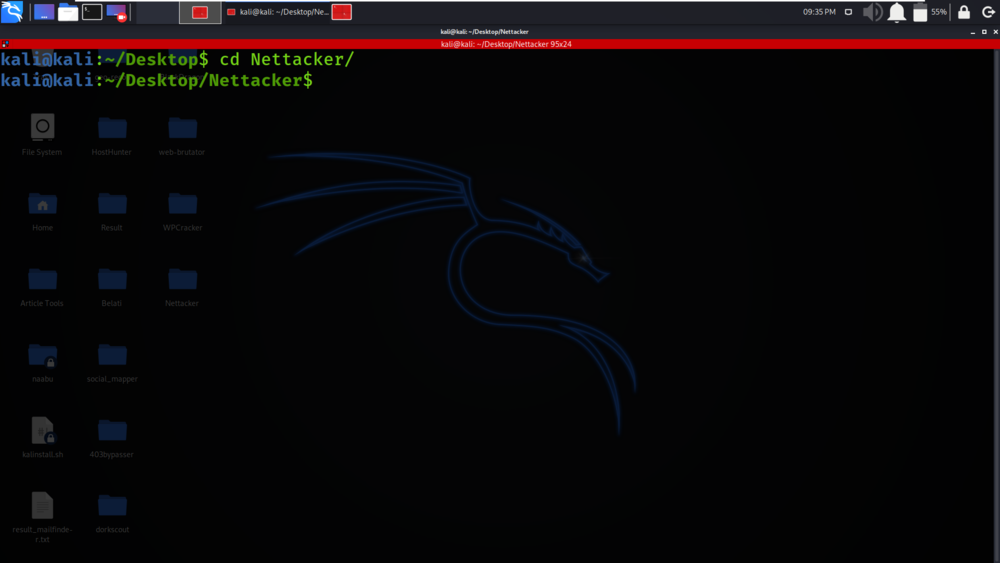
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd Nettacker
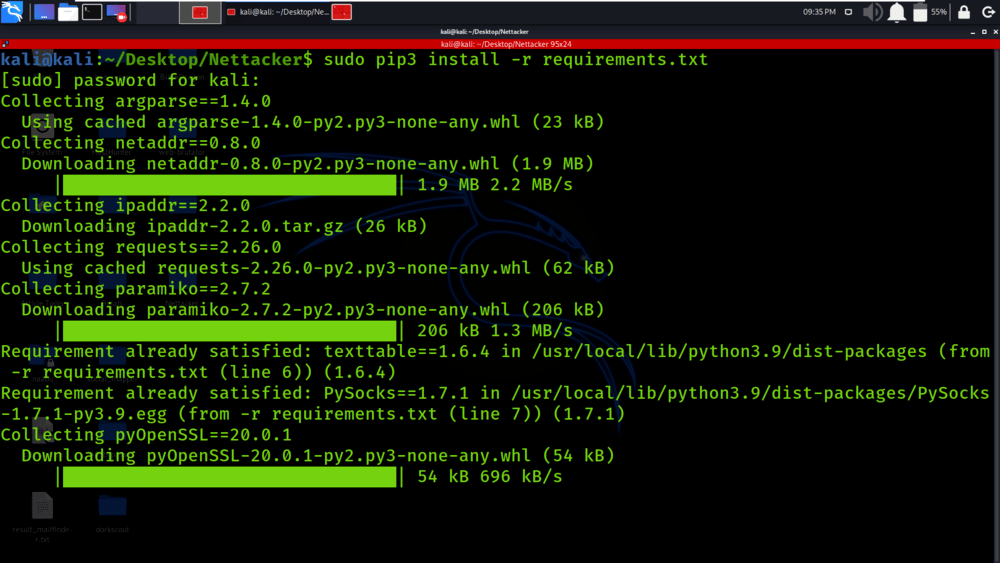
Step 3: You are in the directory of the Nettacker. Now you have to install a dependency of the Nettacker using the following command.
sudo pip3 install -r requirements.txt
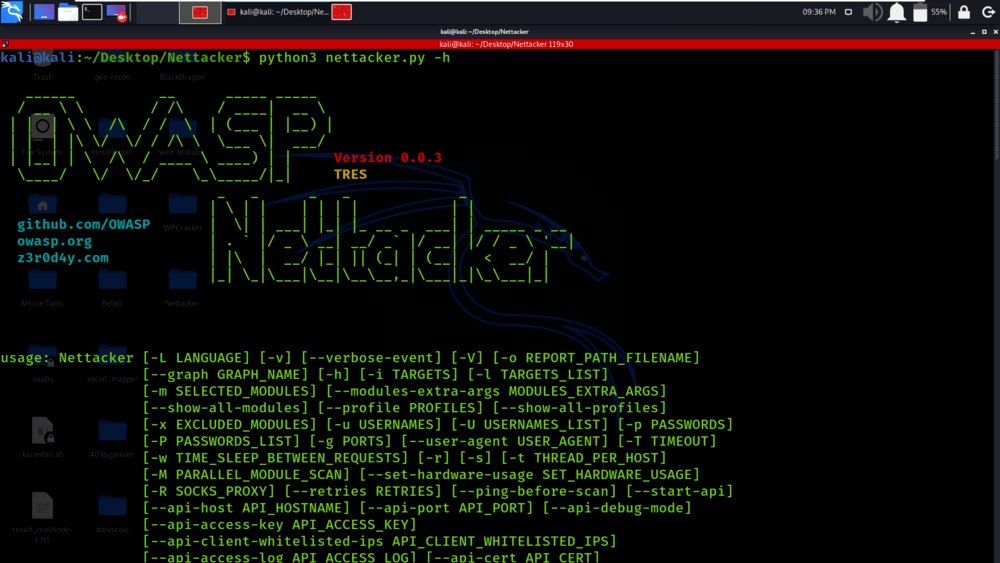
Step 4: All the dependencies have been installed in your Kali Linux operating system. Now use the following command to run the tool and check the help section.
python3 nettacker.py -h
Working with Nettacker Tool on Kali Linux OS
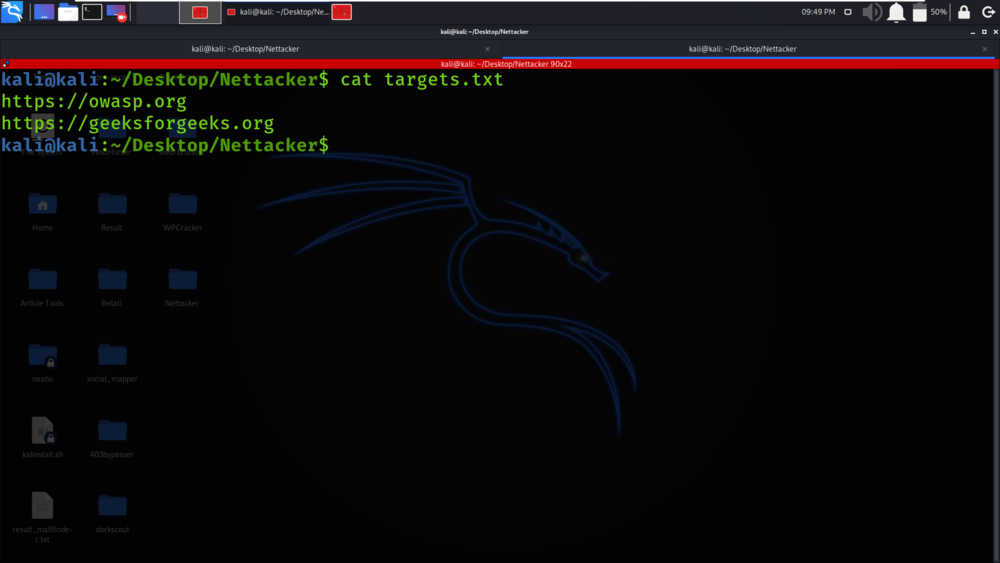
Example 1: Read targets from a list
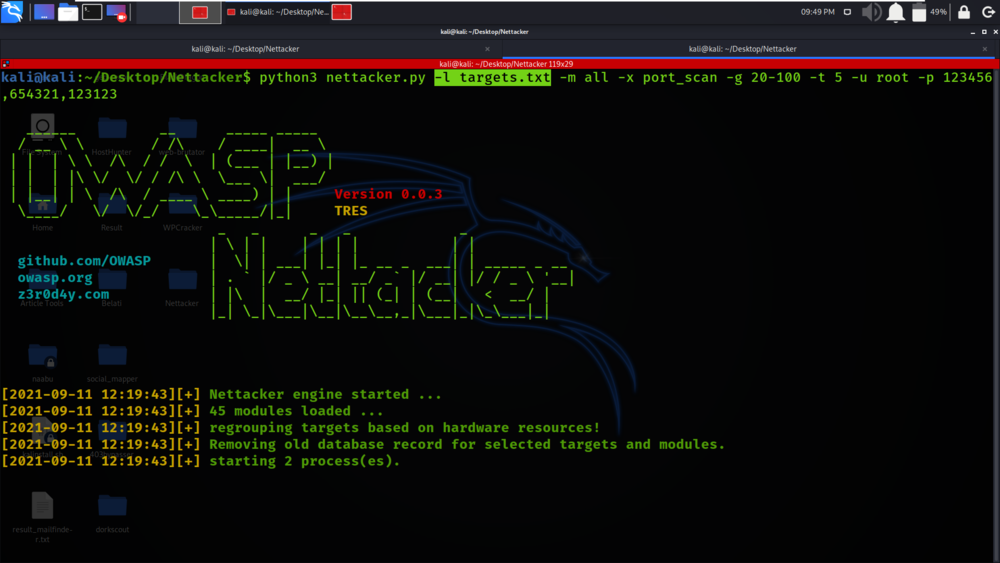
python3 nettacker.py -l targets.txt -m all -x port_scan -g 20-100 -t 5 -u root -p 123456,654321,123123
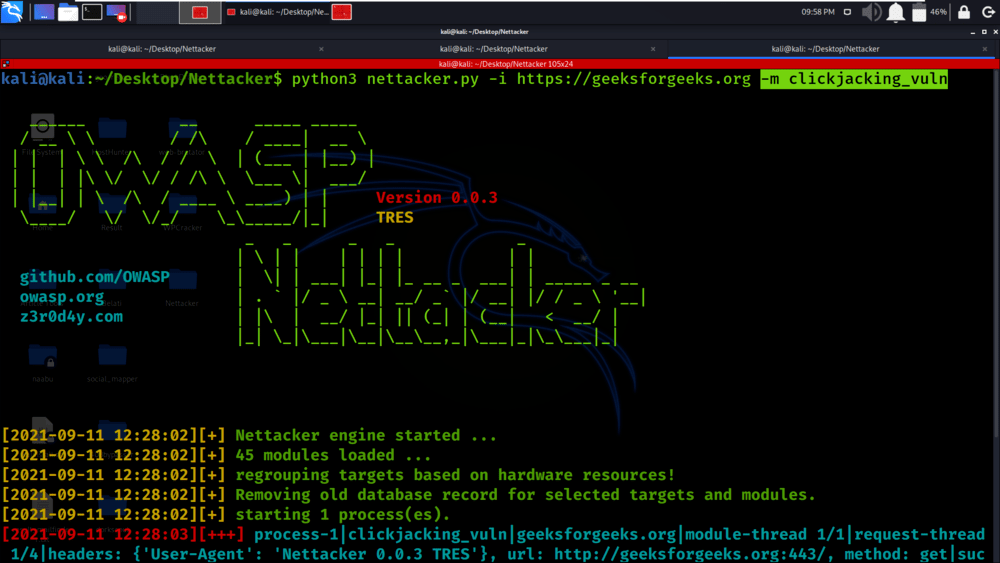
Example 2: Finding clickjacking_vuln
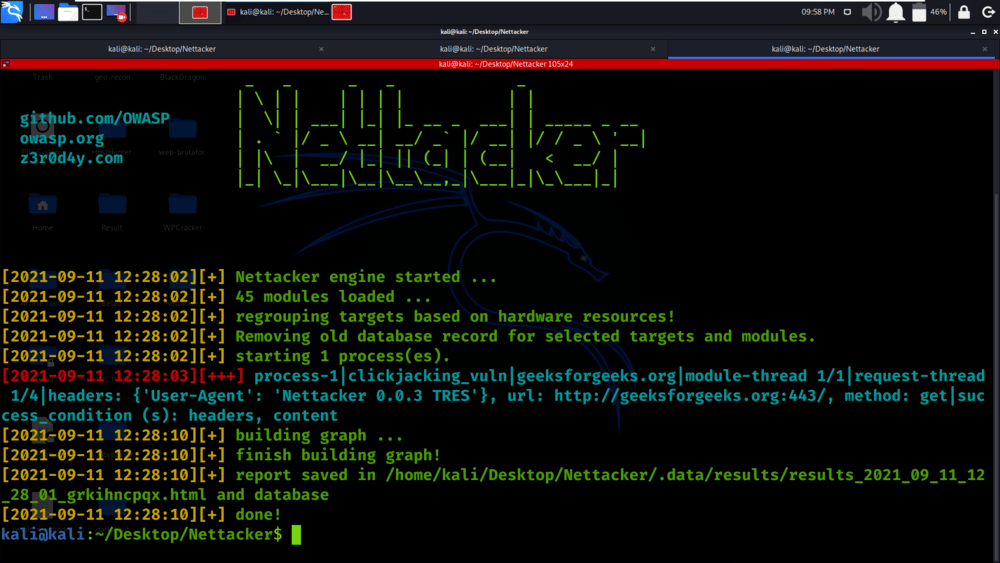
python3 nettacker.py -i https://geeksforgeeks.org -m clickjacking_vuln
Example 3: Scan subdomains
python3 nettacker.py -i geeksforgeeks.org -s -m port_scan -t 10 -M 35 -g 20-100 –graph d3_tree_v2_graph
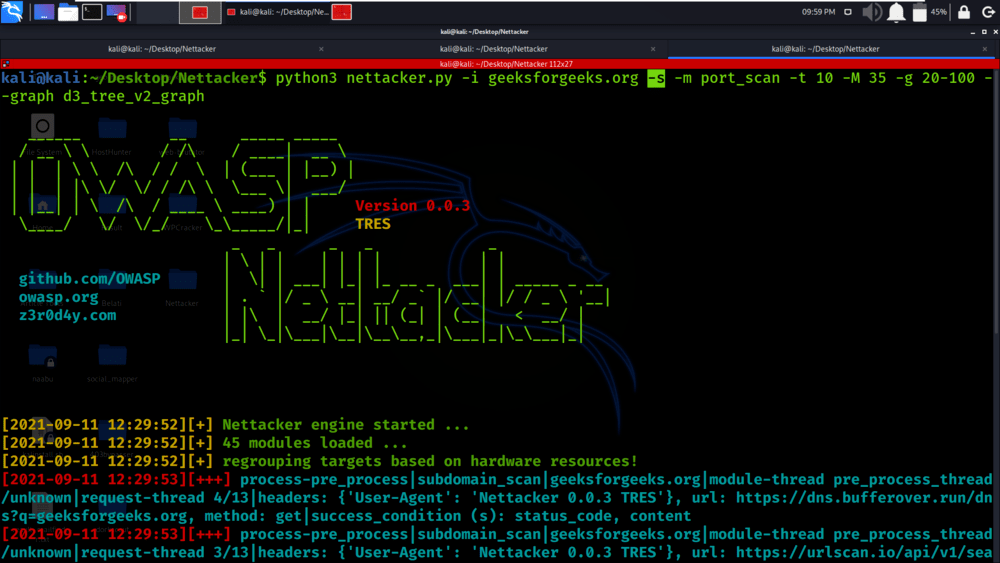
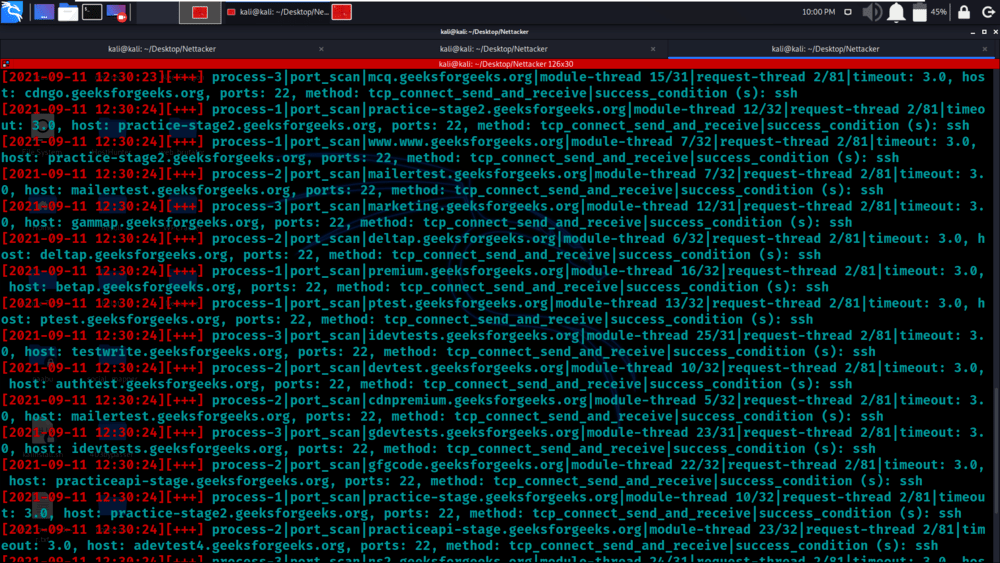
Example 4: Scan the IP range automatically by getting the range from the RIPE database online
python3 nettacker.py -i owasp.org -s -r -m port_scan -t 10 -M 35 -g 20-100 –graph d3_tree_v2_graph
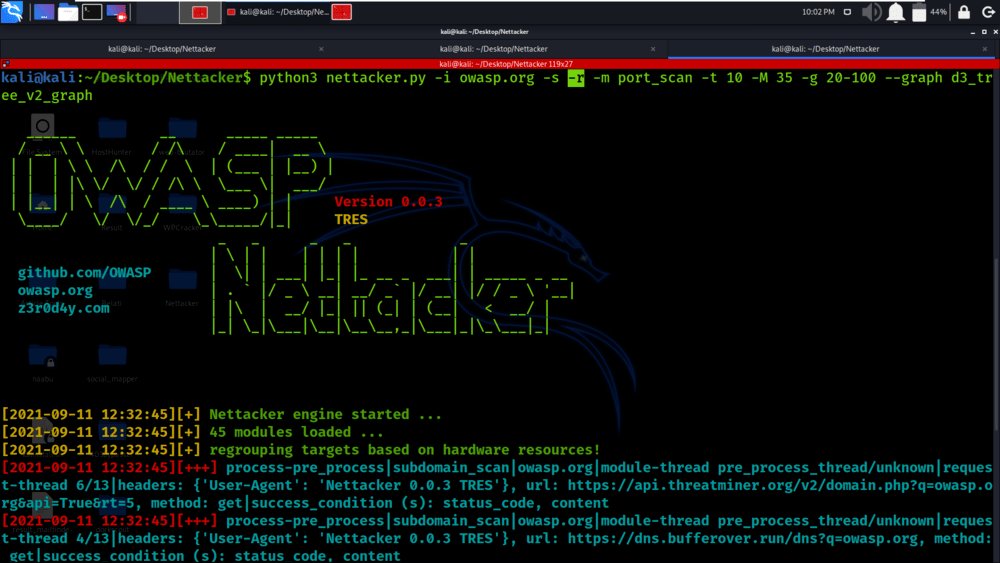
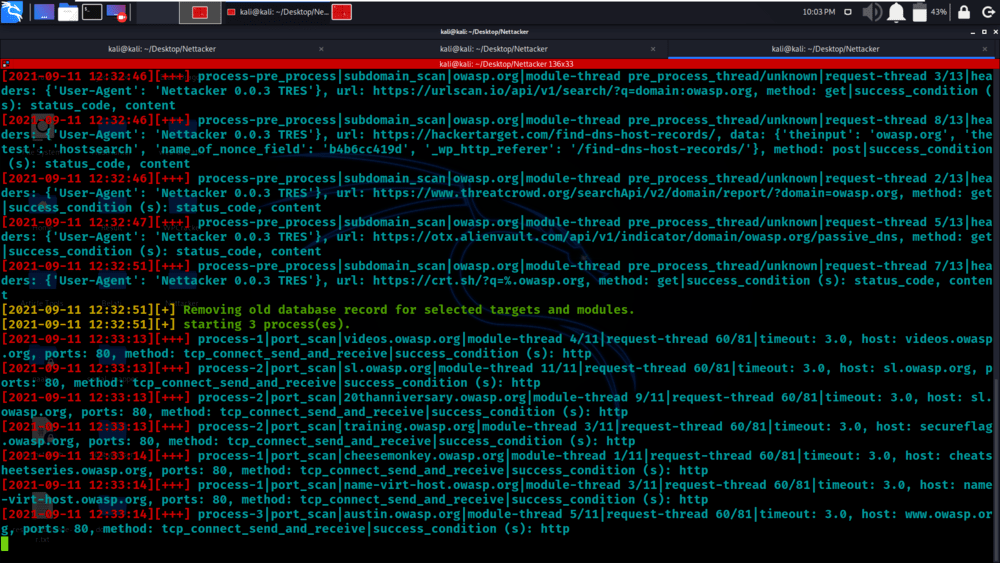
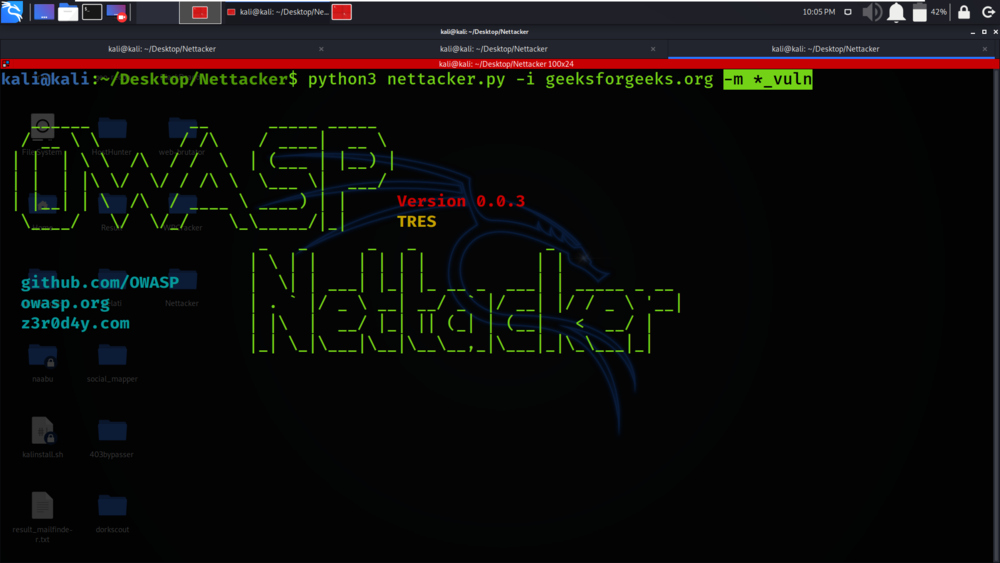
Example 5: Use * pattern for selecting modules
python3 nettacker.py -i geeksforgeeks.org -m *_vuln
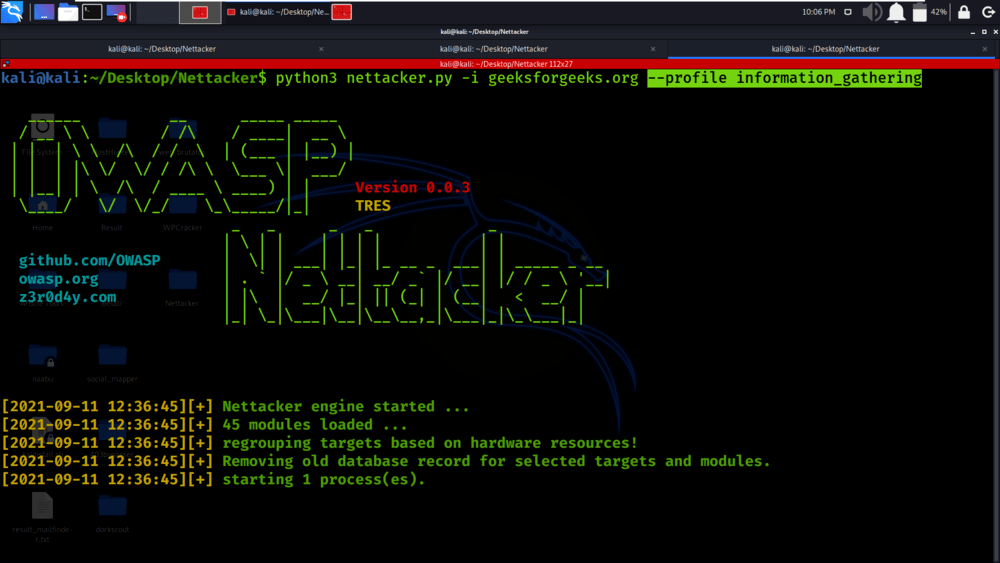
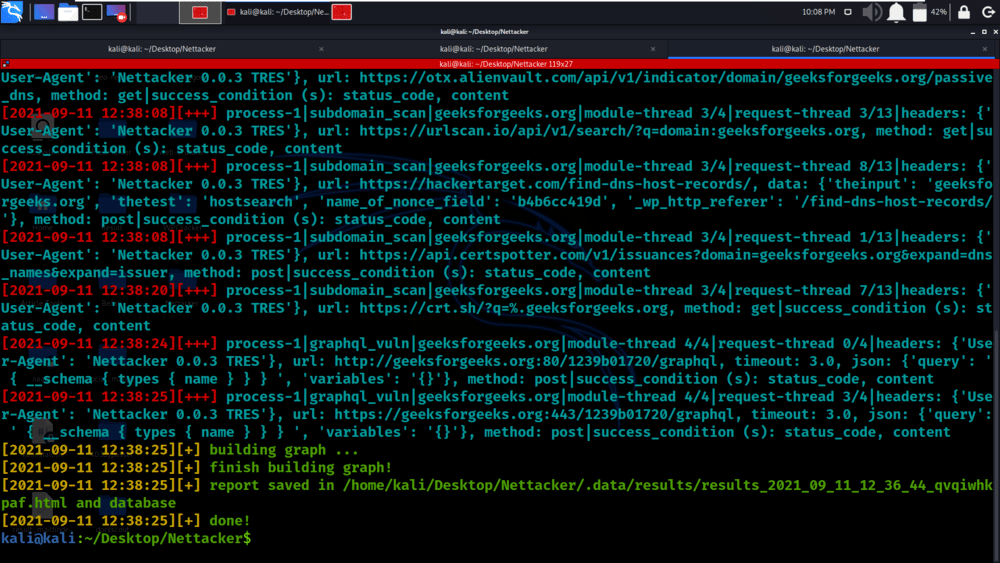
Example 6: Use profiles for using all modules inside a given profile
python3 nettacker.py -i geeksforgeeks.org –profile information_gathering
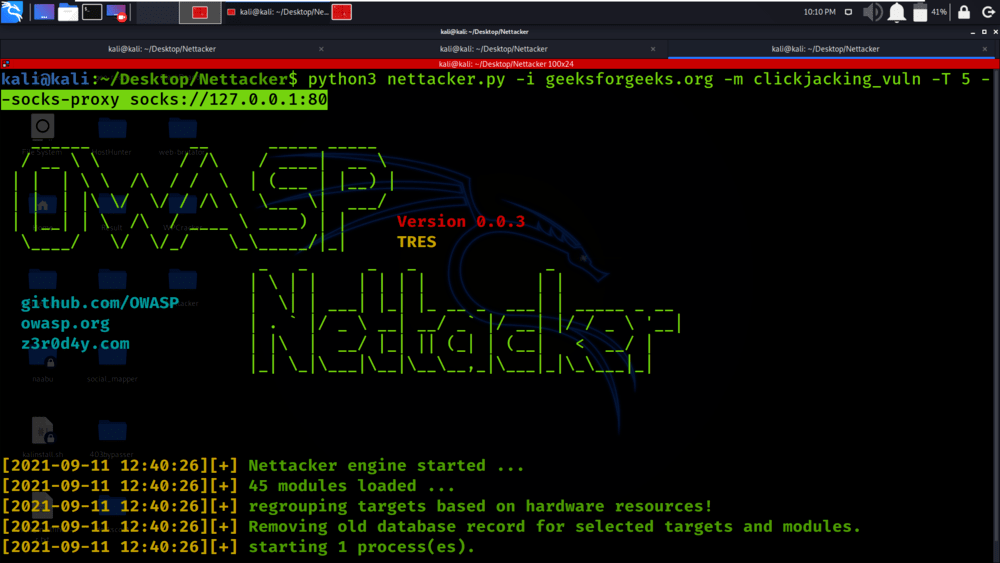
Example 7: Use socks proxy for outgoing connections
python3 nettacker.py -i geeksforgeeks.org -m clickjacking_vuln -T 5 –socks-proxy socks://127.0.0.1:80
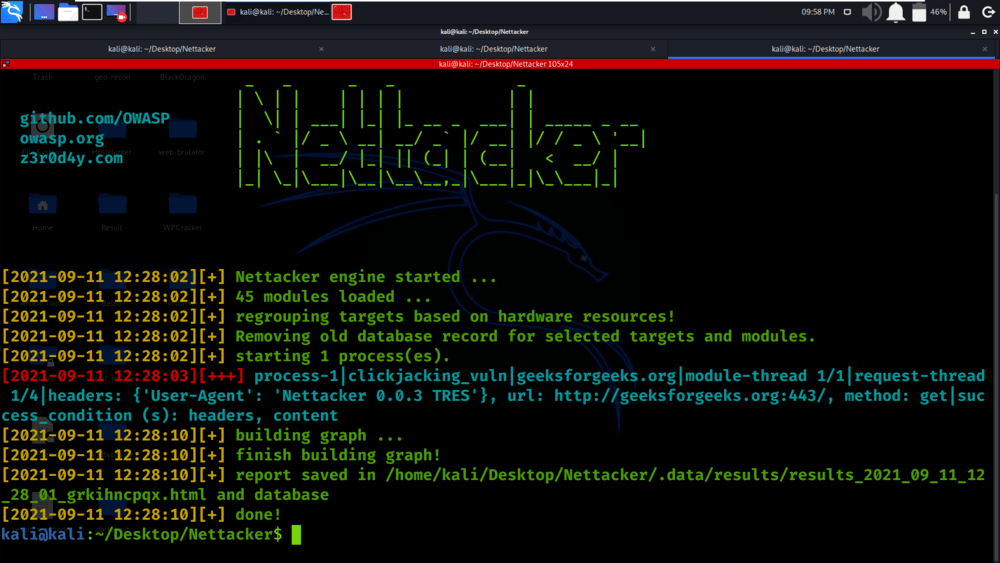
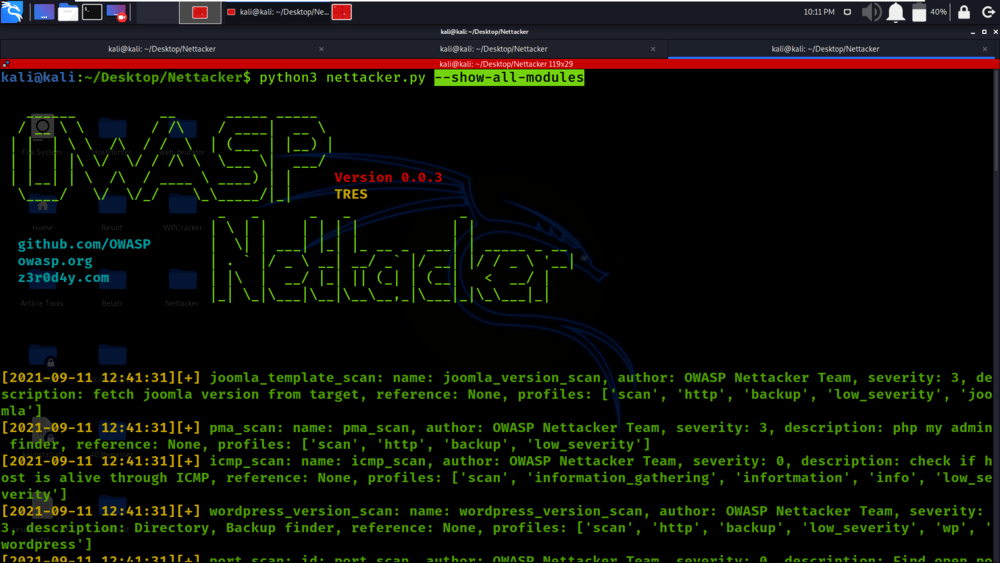
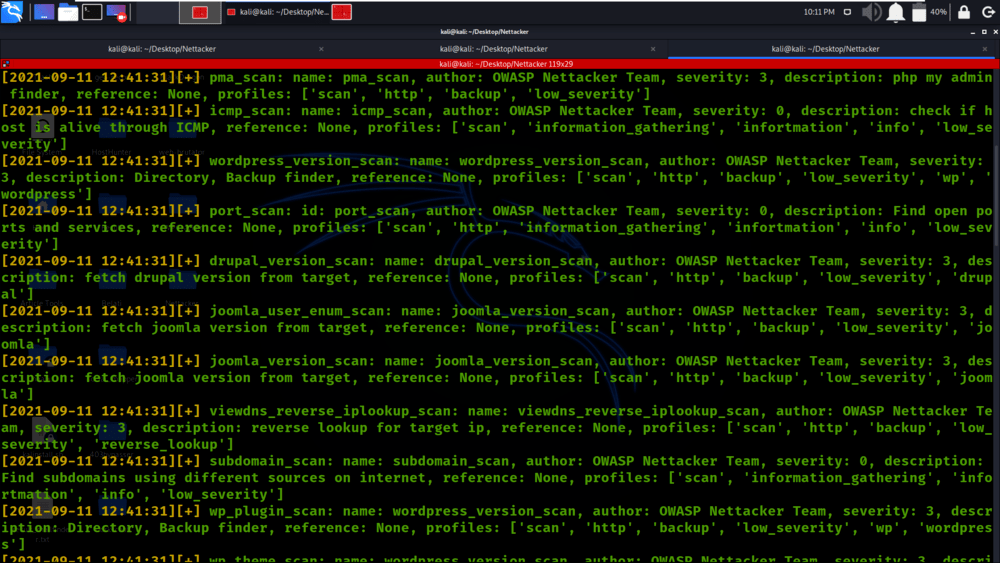
Example 8: Get the list of all modules with details
python3 nettacker.py --show-all-modules
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...