Multitenancy in Cloud computing
Last Updated :
14 Sep, 2022
Multitenancy in Cloud computing: Multitenancy is a type of software architecture where a single software instance can serve multiple distinct user groups. It means that multiple customers of cloud vendor are using the same computing resources. As they are sharing the same computing resources but the data of each Cloud customer is kept totally separate and secure. It is very important concept of Cloud Computing.
In cloud computing Multitenancy also refer as shared host where same resources are divided among different customer’s.
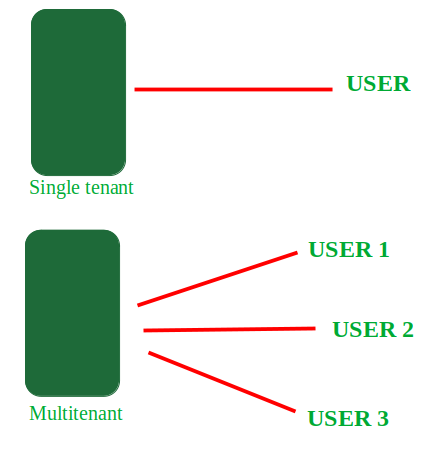
For Example:
The example of multitenancy is the same as working of Bank. Multiple people can store money in the one same bank. But every customer asset is totally different like one customer cannot have access to the other customer’s money and account and different customers are not aware about each other’s account balance and details etc.
Multi-tenancy is an architectural approach enabling a single instance of an application to be shared among multiple organizations or users, and is applied only to SaaS (Software as a service). The core principle here is, it is the single instance of the application which is being shared. Hence, multi-instance architectures aren’t the same as multi-tenant architectures.
Advantages of Multitenancy:
- Use of Available resources is maximized by sharing resources.
- Customer’s Cost of Physical Hardware System is reduces.
- It reduce usage of physical devices and thus power consumption and cooling cost save.
- Save Vendor’s cost as it become difficult for cloud vendor to provide separate Physical Services to each individual.
- Provides isolation to user while maximizing resource utilization.
Disadvantages of Multitenancy:
- As data is stored in third party services , this reduces security of our data and put it into vulnerable condition .
- Unauthorized access will cause damage of data.
- Possibility of competition for system resources.
- It has single point of failure since there is only one instance of resource, clients face loss of service in such cases.
Share your thoughts in the comments
Please Login to comment...