MITM (Man in The Middle) Attack using ARP Poisoning
Last Updated :
15 Apr, 2021
Introduction :
Man In The Middle Attack implies an active attack where the attacker/Hacker creates a connection between the victims and sends messages between them or may capture all the data packets from the victims. In this case, the victims think that they are communicating with each other, but in reality, the malicious attacker/hacker controls the communication i.e. a third person exists to control and monitor the traffic of communication between the two parties i.e. Client and Server.
Types of Man In The Middle Attack :
Here, we will discuss the types of Man In The Middle Attack as follows.
- ARP Spoofing –
ARP Stands for Address Resolution Protocol. This protocol is used for resolving IP addresses to machine MAC addresses. All the devices which want to communicate in the network, broadcast ARP-queries in the system to find out the MAC addresses of other machines. ARP Spoofing is also known as ARP Poisoning. In this, ARP poisoning, ARP packets are forced to send data to the attacker’s machine. ARP Spoofing constructs a huge number of forced ARP requests and replies packets to overload the switch. The intention of the attacker all the network packets and switch set in forwarding mode.
- DNS Spoofing –
Similar to ARP, DNS resolves domain names to IP addresses. DNS spoofing is very dangerous because in this case a hacker will be able to hijack and spoof any DNS request made by the user and can serve the user fake web pages, fake websites, fake login pages, fake updates, and so on.
Man In The Middle Attack Techniques :
Here, we will discuss the Man In The middle attack techniques as follows.
Man in Middle Attack using ARP spoofing :
Here we will discuss the steps for Man in Middle Attack using ARP spoofing as follows.
Step-1:
ARP spoofing -It allows us to redirect the flow of packets in a computer network. Example of a typical Network as follows.

A Typical Computer Network
Step-2 :
But when a hacker becomes Man-In-The-Middle by ARP Spoofing then all the requests and responses start flowing through the hacker’s system as shown below –
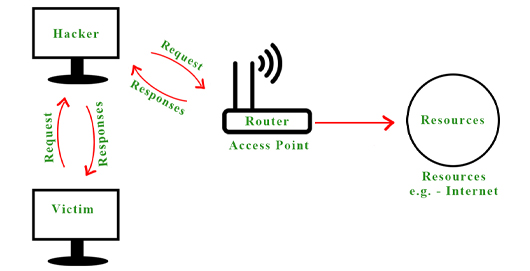
computer network after ARP spoofing
Step-3 :
By doing this a hacker spoof’s the router by pretending to be the victim, and similarly, he spoofs the victim by pretending to be the router.
How to do an ARP Spoof Attack :
We can do an ARP Spoof attack using the built-in tool called ARPSPOOF in Kali Linux, or we can also create an ARP Spoof attack using a python program.
Execution steps :
Here, we will discuss the execution steps as follows.
Step-1:
We can run the built-in “ARPSPOOF’” tool in Kali Linux. In case the ARPSPOOF tool is not present, install the tool by running the following command as follows.
apt install dsniff
Step-2 :
To run this attack we need two things Victim machine’s IP address & the IP of Gateway. In this example, we are using a Windows Machine as our victim and Kali Machine to run the attack. To know the victim machines IP address and gateway IP by running the following command in both the Windows machine and Linux Machine as follows.
arp -a
Output :
This will show us the following Outputs as follows.
Victim Machine (Windows Machine) –

windows machine
Attacker Machine (Kali Linux) –
From these, we can observe that the IP address of the Windows machine is 10.0.2.8 and the IP and MAC addresses of the gateway are 10.0.2.1 and 52:54:00:12:35:00, also the MAC address of our Kali Machine is 08:00:27:a6:1f:86.

Step-3 :
Now, write the following commands to perform the ARP Spoof attack.
arpspoof -i eth0 -t 10.0.2.8 10.0.2.1
Here eth0 is the name of the interface, 10.0.2.8 is the IP of the Windows machine and 10.0.2.1 is the IP of the gateway. This will fool the victim by pretending to be the router. So again we will run the above command one more time by switching its IP addresses as follows.
arpspoof -i eth0 -t 10.0.2.1 10.0.2.8
Output :
Attacker Machine (Kali Linux) –
This shows that our ARP Spoof attack is running, and we have successfully placed our system in the middle of the client and server.

ARP Spoof attack running
We can also check it by running the command as follows.
arp -a
Output :
In the output screen, you can observe that the MAC address of the gateway is changed to the MAC address of Kali Machine. Now all the data packets will flow through our Kali machine. Also, you can see that the internet connection of the victim machine is not working because it’s the security feature of Linux, which does not allow the flow of packets through it. So we need to enable Port Forwarding so that this computer will allow the packets to flow through it just like a router.

Step-4 :
To enable Port Forwarding to run the command as follows.
echo 1 > /proc/sys/net/ipv4/ip_forward
Output :
This command will again establish the Internet connectivity of the victim computer. In this way, we can become the Man-In-The-Middle by using the ARP Spoof attack. So all the requests from the victim’s computer will not directly go to the router it will flow through the attacker’s machine and the attacker can sniff or extract useful information by using various tools like Wire Shark, etc. as shown below as follows.

Wire Shark – used to sniff useful information from the packets.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...