Mitaka – Browser Extension For OSINT Search
Last Updated :
19 Feb, 2024
Identifying malware, determining the credibility of an email address, and finding if a URL is associated with anything sketchy, if these are things one wants to achieve, then simply install a web browser extension known as Mitaka. It was created by Manabu Nieski. After installation, one can select and inspect certain pieces of text and indicators of compromise (IoC) that one thinks may be suspicious, by running them through a variety of different search engines, all with just a few clicks here and there.
Key Features
- It provides auto indicators of compromise (IoC) selection with REFang. For example-example[.]com to example.com, test[at]example.com to test@example.com, etc.
- It supports 65+ services.
Supported Search Engines
In the table given below are some search engines supported by Mitaka.
| Name |
URL |
Supported Types |
| AbuseIPDB |
https://www.abuseipdb.com |
IP |
| AnyRun |
https://app.any.run |
Hash |
| apklab |
https://apklab.io |
Hash (SHA256) |
| archive.org |
https://archive.org |
URL |
| archive.today URL |
http://archive.fo |
URL |
| BGPView |
https://bgpview.io |
IP, ASN |
| BinaryEdge |
https://app.binaryedge.io |
IP, domain |
| BitcoinAbuse |
https://www.bitcoinabuse.com |
BTC |
| BitcoinWhosWhos |
https://bitcoinwhoswho.com |
BTC |
Supported Scan Engines
In the table given below are some scan engines supported by Mitaka.
| Name |
URL |
Supported Types |
| Browserling |
https://www.browserling.com |
URL |
| HybridAnalysis |
https://www.hybrid-analysis.com |
URL |
| Urlscan |
https://urlscan.io |
IP, domain, URL |
| VirusTotal |
https://www.virustotal.com |
URL |
Supported IoCs
In the table given below are some IoCs supported by Mitaka.
| Name |
Description |
Example |
| asn |
ASN |
AS13335 |
| btc |
BTC address |
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa |
| cve |
CVE number |
CVE-2018-11776 |
| domain |
Domain name |
github.com |
| email |
Email address |
test@test.com |
Fig3: Supported IoCs.
Installation
Mitaka is used to perform In-Browser OSINT investigations to identify Malware, Sketchy Sites, Shady Emails and help individuals get aware and secure.
Note: Setting the API keys is needed in the options for enabling HybridAnalysis, urlscan.io, and VirusTotal scan.
Installing Mitaka is like installing any other browser extension.
- Visit Mitaka in either Chrome Web Store or Firefox Add-Ons.
- Click on Add to Chrome or Add to Firefox.
- Select Add to verify.
Suppose there is an email that needs to be investigated, all that is required is to highlight and right-click it, then look through all of the options Mitaka provides in the contextual menu.
How to use Mitaka
Below are the two cases of using Mitaka.
Email Address inspection: Let’s discuss the steps to inspecting an email address.
- Suppose there is an email address that is suspected to be malicious, whether it’s defanged (obfuscated so it can’t be clicked) or clickable, the user can highlight it, right-click it, then choose the browser extension Mitaka. If it’s harmful or infected, Mitaka will rearm it so that any search performed will still work.
- In the menu provided by Mitaka, one can see a variety of tools one can use to inspect and investigate the email address.
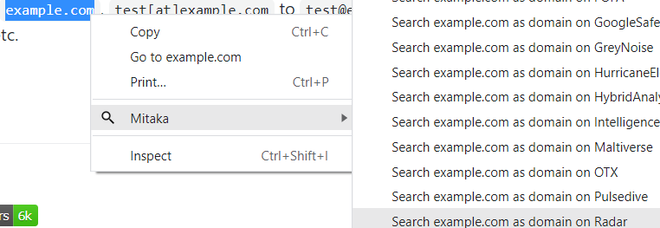
- Users can perform searches on PublicWWW, IntelligenceX, OCCPR, RiskIQ, SecurityTrails, ThreatConnect, ThreatCrowd, and ViewDNS. For example, if a user wants to know when an email address was registered, whether it has a global audience or not, or if it supports IPv6. So, to find out all this, simply highlight the email address and choose Search example.com as a domain on Radar and the user will get the required information about it.
- From the results shown below, one can see that example.com has a global audience. It was registered 25 years ago and supports IPv6.Also, one can see its domain popularity country-wise, showing it is very popular in the USA, followed by Brazil.
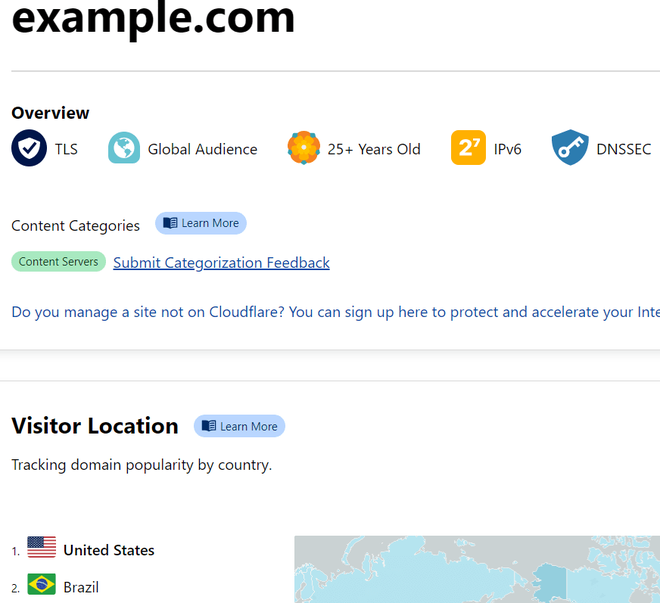
- So, as one can see, Mitaka can prove to be a very useful tool in finding out useful information, like when it is registered, its domain popularity and whether it has a global audience or not, and much more.
Suspicious URL:
- Suppose one of the friends suggested a URL where one can find various projects, source code, repositories, but it is not confirmed whether it is safe to access or not. So what one can do is, right-click it, select Mitaka, then use Pulsedive to check.
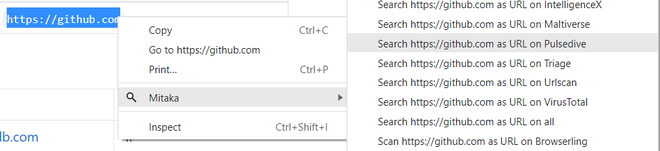
- From the report shown below, one can assume or say that it’s probably a genuine URL and that there is a very low risk of accessing it, it’s also there in the top 100k domains.
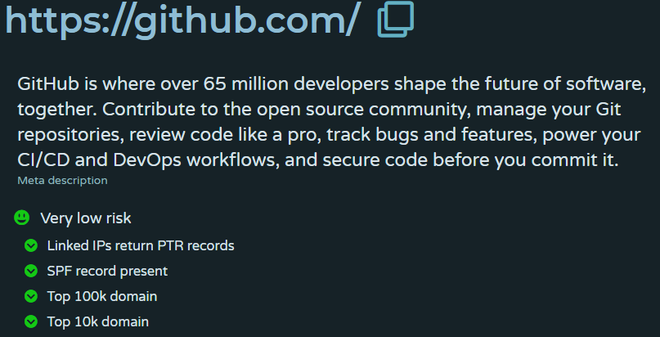
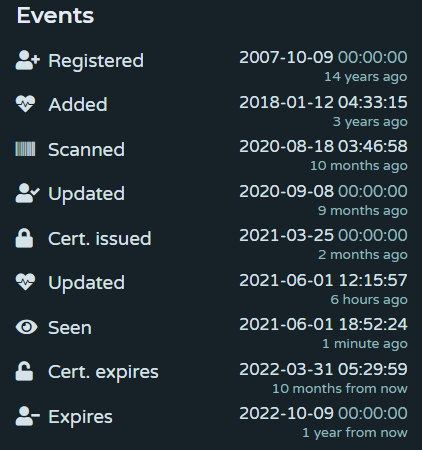
- Here in events, one can see when it was registered, when it was updated, scanned, or when its certificate was issued.
Malware Analysis: Malware analysis is just another exciting weapon Mitaka offers in its arsenal. Now let’s perform malware analysis on files.
- Suppose, on a website, there is a file that one wants to download. There is a tool recommended by friends or colleagues and it also looks reputable, and the web app seems good. Once the file is downloaded, most people compare the hash to the one listed on the site. If the hash matches, then it is assumed that the right file was downloaded, but how to know that the file is really OK?
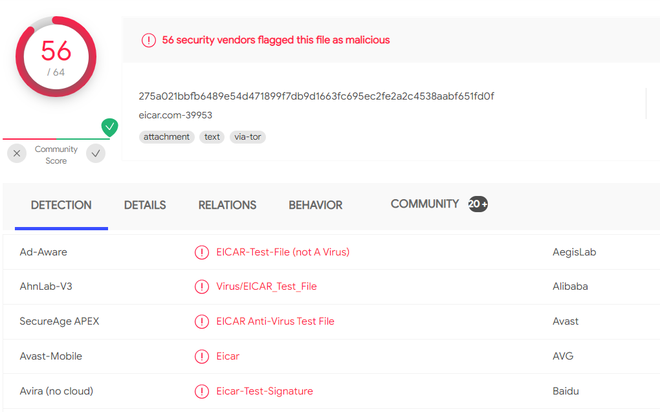
- If a virus scanner doesn’t catch it on the computer, one can always take the hash of the file that’s on the website, right-click it, choose Mitaka, then use something like VirusTotal. This scanner simply identifies potentially suspicious files by looking at the hash and trying to find out whether or not it could harm the computer.
- As a result, one can see that there are multiple detections and 56 vendors flagged this file as malicious. So even if one had to run this on the computer or laptop, even though it’s undetected by Avast and a bunch of other different, pretty reputable malware scanners like AVG and Bitdefender, it still would have gotten through.
- One can also check summary, behavior, details for more information regarding these detections. So, Mitaka is a pretty effective way of checking a file that we encounter anywhere on the web.
Checking If Site Is Sketchy:
- Just hover over any domain That might appear sketchy and after selecting it, right-click and choose Mitaka to find out.
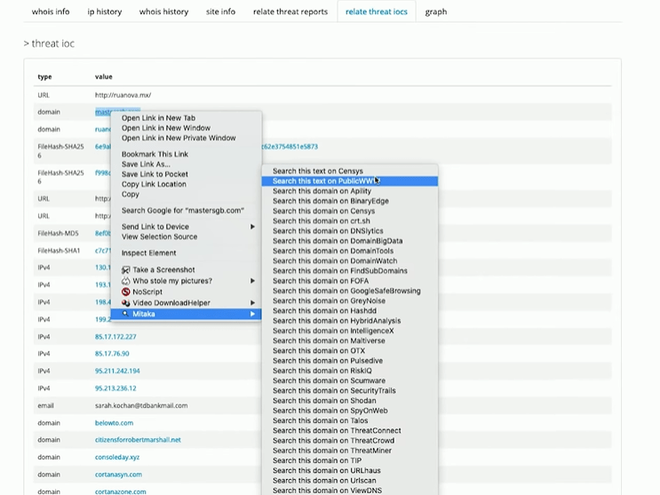
- The domain that was searched for is associated with some sketchy stuff, as one can see that it’s being used for some poor lookups and all sorts of other worrisome activities.

So to conclude, the Mitaka extension is a very useful extension. It can be used for various purposes, such as checking if the site is sketchy, inspecting email addresses, etc. There are tons of different ways in which one can investigate a clue on the net using a simple right-click menu.
Advantages
- Mitaka is easy to use.
- It makes OSINT easy as one can right-click to search for hashes, email addresses, etc.
- It supports more than 60 services.
Disadvantages
- Browser extensions run on the web browser and often require the ability to read or change everything on web pages user visits, which in some cases can lead to horrific accidents of data breaches, capture the passwords, track browsing, insert ads into web pages user visits.
- If an extension requires new permissions and if not given, then a new version of the extension will run with all the same permissions the previous version did, which will lead to problems.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...