How to Prevent Man In the Middle Attack?
Last Updated :
05 Apr, 2024
In a web application, there are two things usually: the client and the server. The third entity that remains unnoticed most of the time is the communication channel. This channel can be a wired connection or a wireless connection. There can be one or more servers in the way forwarding your request to the destination server in the most efficient way possible. These are known as Proxy servers.
What is a Man in the Middle Attack?
When there is an unwanted proxy in the network intercepting and modifying the requests/responses, this proxy is called a Man in the middle or we can say that Man In the Middle Attack poses a serious risk to online communication, resulting in the stealing of private data, financial loss, and harm to reputation. For example, suppose you are connected to a Wi-Fi network and doing a transaction with your bank. An attacker is also connected to the same Wi-Fi. The attacker does the following:
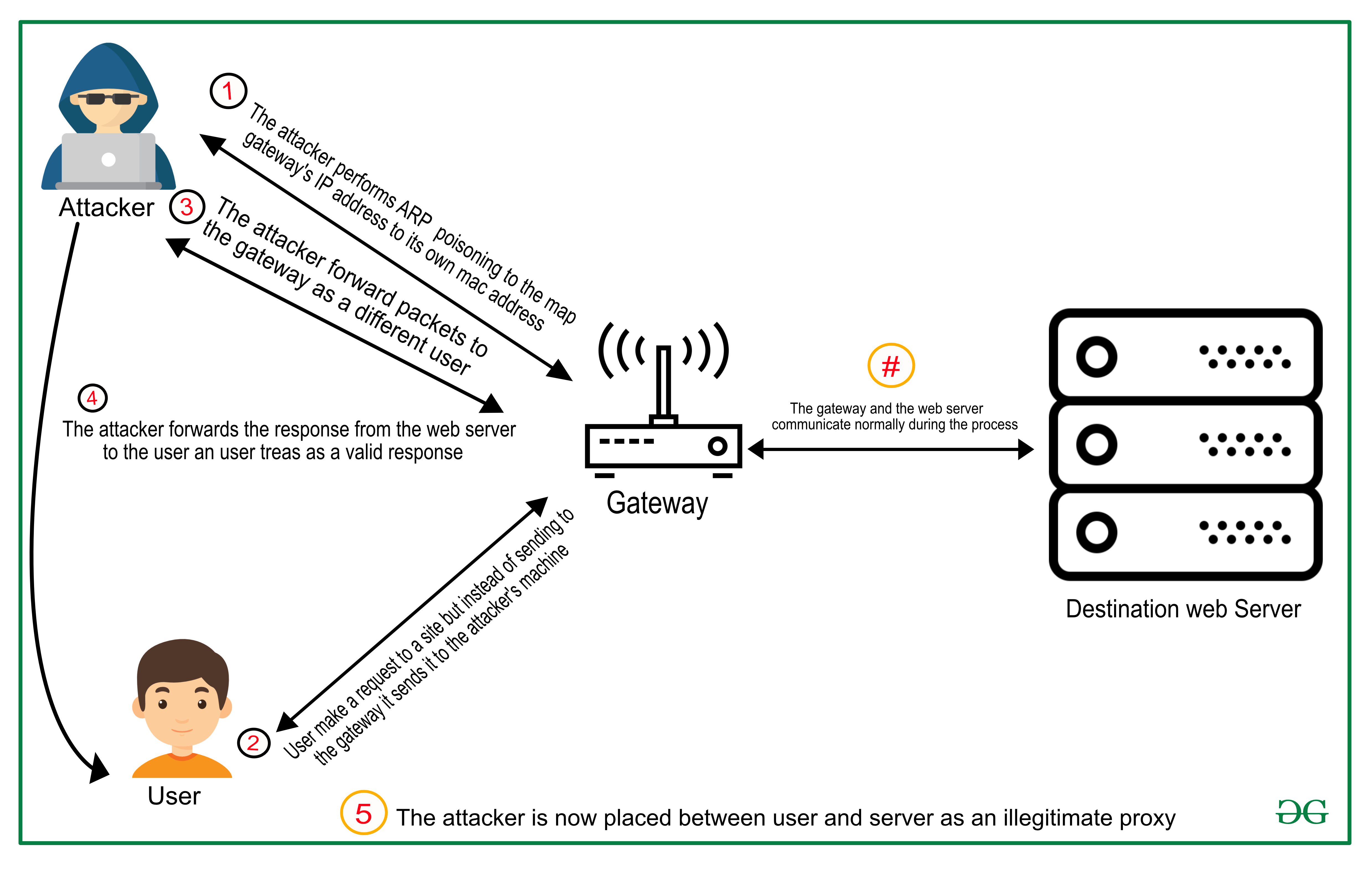
- The attacker sends the rogue ARP packets in the network that map the IP address of the access point to the MAC address of the attacker’s device.
- Each device connected in the network caches the entry contained in the rogue packets.
- Your device uses ARP to send the packets destined for your bank’s web server to the access point (which is the default gateway for the network).
- The packets get sent to the attacker’s machine.
- Attackers can now read and modify the requests contained in the packets before forwarding them.
This way the attacker is suitably situated between you and your bank’s server. Every bit of sensitive data that you send to your server including your login password, is visible to the attacker. ARP cache poisoning is one of the ways to perform an MITM attack; other ways are –
The use of SSL can prevent these attacks from being successful. Since the data is encrypted and only legitimate endpoints have the key to decrypt it, the attacker can do very little from the data even if he gets access to it.
(SSL is only useful if it’s set up properly, there are ways to circumvent this protection mechanism too, but they are very hard to carry out). Still, an attacker can do a lot of damage if the web application with which the user has been interacting does not utilize the use of something called the nonce. The attacker can capture the encrypted request, for the entire session and then carefully resend the requests used for logging in. This way the attacker will get access to your account without knowing your password. Using nonce prevents such “replay attacks”. A nonce is a unique number that is sent by the server to the client before login. It is submitted with the username and password and is invalidated after a single use.
Types of Man-in-the-Middle Attacks
- Rogue Access Point: Devices with wireless cards frequently try to automatically connect to the access point with the strongest signal. Attackers can set up their wireless access points and nearby devices joining their domain.
- ARP Spoofing: ARP stands for Address Resolution Protocol. It converts IP addresses to physical MAC (media access control) addresses in a local area network. When a host needs to communicate with a host with a specific IP address, it uses the ARP cache to convert the IP address to a MAC address. If the address is unknown, a request is sent for the MAC address of the device associated with the IP address.
- DNS Spoofing: DNS resolves domain names to IP addresses in the same way as ARP does on a local area network. In a DNS spoofing attack, the attacker tries to inject faulty DNS cache information into a host to visit another host using their domain name.
- Email phishing: A threatening attacker uses a false email to attempt to get access to sensitive data. Phishing scams sometimes use emails spoofing official sources, such as a corporate executive or a bank representative, to get login credentials, account information, and other information from consumers.
- Router spoofing: One of the most common man-in-the-middle attacks is router spoofing, which occurs when an attacker with malicious intent establishes a fake wifi network that replicates proper networks in the area to mislead people into connecting. Once they do, the attacker gains access to the data streaming from the user’s device.
Man-in-the-Middle Attack Techniques
- Sniffing: Packet sniffing is a man-in-the-middle attack in which an attacker captures and analyses network communication. The attacker can then examine and manipulate the data that is transmitted between two devices.
- Packet Injection: An attacker may also use the device’s monitoring mode to inject malicious packets into data communication streams. The packets might mix in with real data transmission streams, giving the impression that they are part of the conversation but are harmful. Packet injection normally starts with sniffing to establish how and when to create and deliver packets.
- SSL Stripping: SSL stripping is a form of man-in-the-middle attack in which an attacker tries to degrade an encrypted HTTPS connection to HTTP. The attacker can then view and alter the data being transmitted between two devices.
- Eavesdropping: Eavesdropping is a type of man-in-the-middle attack in which an attacker listens to an ongoing communication session between two computers. The attacker can then view and alter the data being transmitted between two devices.
How to Detect a Man-in-the-Middle Attack?
- Fake websites: Hackers use a man-in-the-middle attack to direct you to a web page or site that they control. Because they only have access to your internet connection and the traffic flowing from your device, not the contents of your computer.
- Unusual Network Activity: A significant increase in network traffic may indicate a man-in-the-middle (MIT) attack. unusual connections or requests from unusual sources can indicate that an attacker is trying to steal data packets.
- Suspicious certificates: If your browser displays a certificate warning, it indicates that you are going to visit a website that has been encrypted by a criminal as part of an MITM attack. You should not go to the website.
- Unexpected Credential Requests: If a website or application requests credentials that the user is unfamiliar with, this may indicate a man-in-the-middle attack.
- Unusual Login Errors: If a user encounters login errors after entering the correct credentials, it may indicate that an attacker is attempting to steal data packets.
- Unexpected Pop-Ups: Unexpected pop-up windows or notifications could indicate a man-in-the-middle attack.
How to prevent Man-in-the-Middle attacks?
- Always use trusted networks and devices to log in to sensitive websites.
- Avoid connecting to a Wi-Fi that is open(unencrypted).
- Keeping networks secure from unwanted external access.
- In case you have to use a public computer, check its browser for the presence of any rogue certificate and make sure that there aren’t any. Check the hosts’ file too.
- When connected to a public network or using a public computer, perform a traceroute to the website you want to access and see the route taken by the packets for anything suspicious. For example, packets going to an IP different from the IP whose last octet is 1 (the IP of your gateway).
Key Concepts of Man in the Middle Attack
- The attackers intercept the conversation between the client and the server to steal confidential data.
- The data transfers that take place during this attack remain undetected.
- The attacker tries to perform this attack by using various tricks like sending attachments links or duplicate websites.
Case Study of Man In the Middle Attack
- Case Study-1: The credit score company Equifax removed their apps from Google and apple due to the data leaking. It has been found that the app did not use HTTPS which allowed the attackers to get all those data when the user was accessing their account.
- Case Study-2: There was a registrar company that was breached and enabled the attacker to gain access to many certificates. These certificates allowed the attacker to pose as an authentic website to steal the data from the user, the authentic website in this case was duplicated.
- Case Study-3: There was a bank that was targeted by the attacker. The attacker sends an email to the customer that someone might have attempted to log in to their bank account, and they need the information from them to verify. The email that was sent to the customer was a phishing attack. So the victim will click on the link sent in the email, and they would be taken to a fake website. The fake website will seem to be original. When the victim will enter the details, it will be redirected to the original website. Now the attacker got access to the victim’s account.
Users should be aware of
- Public Wi-Fi Network.
- Don’t access that Wi-Fi where the name of the Wi-Fi does not seem to be right.
Conclusion
Man In the Middle Attack offer a serious risk to online communication, resulting in the stealing of private data, financial loss, and harm to reputation. To avoid MitM attacks, take precautions such as employing encryption, checking SSL/TLS certificates, and staying away from insecure Wi-Fi networks. You may lower your risk of being a victim of a Man In the Middle Attack by remaining attentive and implementing best practices.
Frequently Asked Question on Man in the Middle Attack – FAQs
It is a common attack?
This Man in the Middle Attack is not common for a longer period of time. This type of attack is usually done when the attacker has a specific target. This attack is not a common attack like phishing or any kind of malware or ransomware.
What is the difference between the Man in the Middle Attack and Remote Access Trojans?
Man in the Middle Attack is a type of cyber-attack where the attacker performs its functions by staying between the two parties. The type of function it can do is to alter the communication between the two parties and make both of the parties feel that they are communicating in a secured network.
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gain remote access.
What is the root cause of man-in-the-middle attack?
A Man-in-the-Middle (MitM) attack originates from the weakness of the communication link between two parties.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...