Kali Linux – Information Gathering Tools
Last Updated :
07 Sep, 2021
Information Gathering means gathering different kinds of information about the target. It is basically, the first step or the beginning stage of Ethical Hacking, where the penetration testers or hackers (both black hat or white hat) tries to gather all the information about the target, in order to use it for Hacking. To obtain more relevant results, we have to gather more information about the target to increase the probability of a successful attack. 0
Information gathering is an art that every penetration-tester (pen-tester) and hacker should master for a better experience in penetration testing. It is a method used by analysts to determine the needs of customers and users. Techniques that provide safety, utility, usability, learnability, etc. for collaborators result in their collaboration, commitment, and honesty. Various tools and techniques are available, including public sources such as Whois, nslookup which can help hackers to gather user information. This step is very important because while performing attacks on any target information (such as his pet name, best friend’s name, age, or phone number to perform password guessing attacks(brute force) or other kinds of attacks) are required.
Information gathering can be classified into the following categories:
- Footprinting
- Scanning
- Enumeration
- Reconnaissance
Nmap is an open-source network scanner that is used to recon/scan networks. It is used to discover hosts, ports, and services along with their versions over a network. It sends packets to the host and then analyzes the responses in order to produce the desired results. It could even be used for host discovery, operating system detection, or scanning for open ports. It is one of the most popular reconnaissance tools.
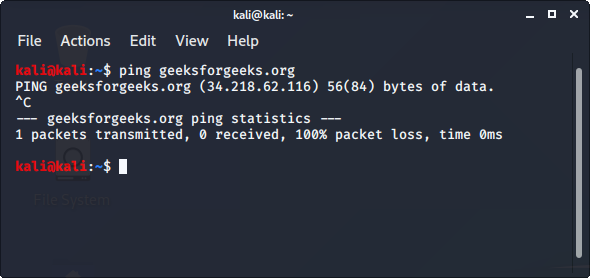
To use nmap:
- Ping the host with the ping command to get the IP address
ping hostname
- Open the terminal and enter the following command there.
nmap -sV ipaddress
Replace the IP address with the IP address of the host you want to scan.
- It will display all the captured details of the host.
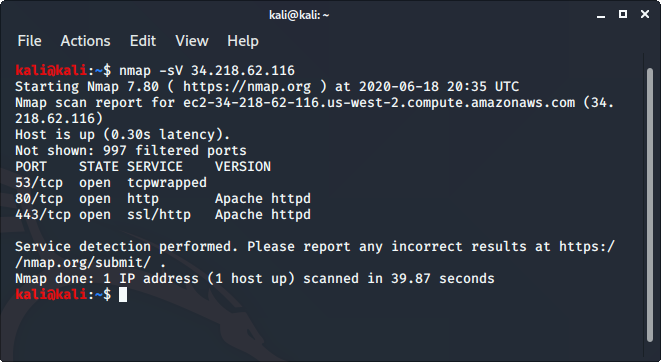
Read more about nmap.
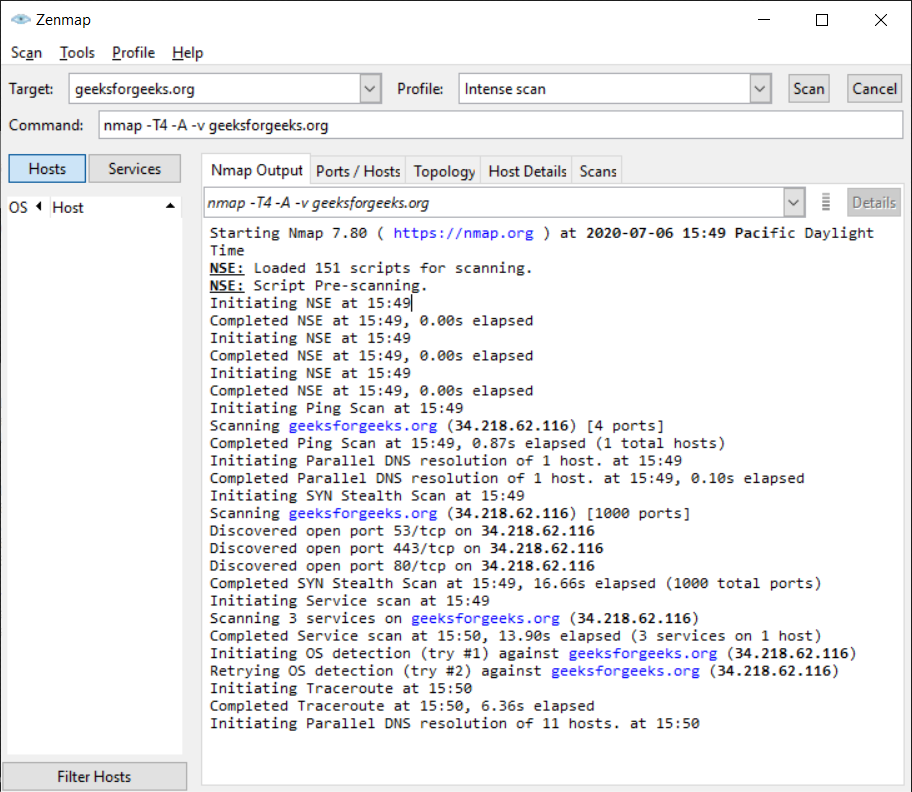
2. ZenMAP
It is another useful tool for the scanning phase of Ethical Hacking in Kali Linux. It uses the Graphical User Interface. It is a great tool for network discovery and security auditing. It does the same functions as that of the Nmap tool or in other words, it is the graphical Interface version of the Nmap tool. It uses command line Interface. It is a free utility tool for network discovery and security auditing. Tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime are considered really useful by systems and network administrators.
To use Zenmap, enter the target URL in the target field to scan the target.
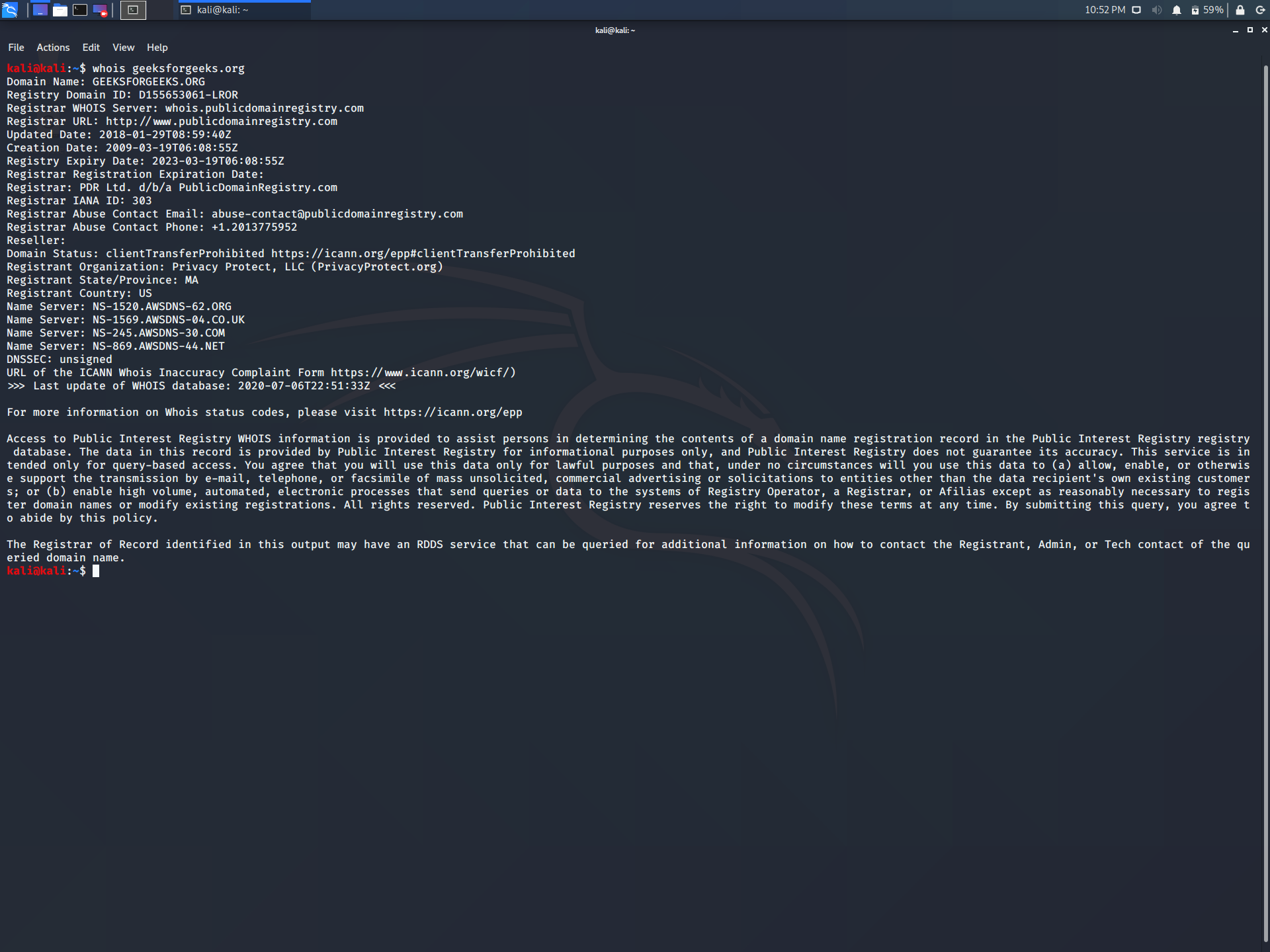
3. whois lookup
whois is a database record of all the registered domains over the internet. It is used for many purposes, a few of them are listed below.
- It is used by Network Administrators in order to identify and fix DNS or domain-related issues.
- It is used to check the availability of domain names.
- It is used to identify trademark infringement.
- It could even be used to track down the registrants of the Fraud domain.
To use whois lookup, enter the following command in the terminal
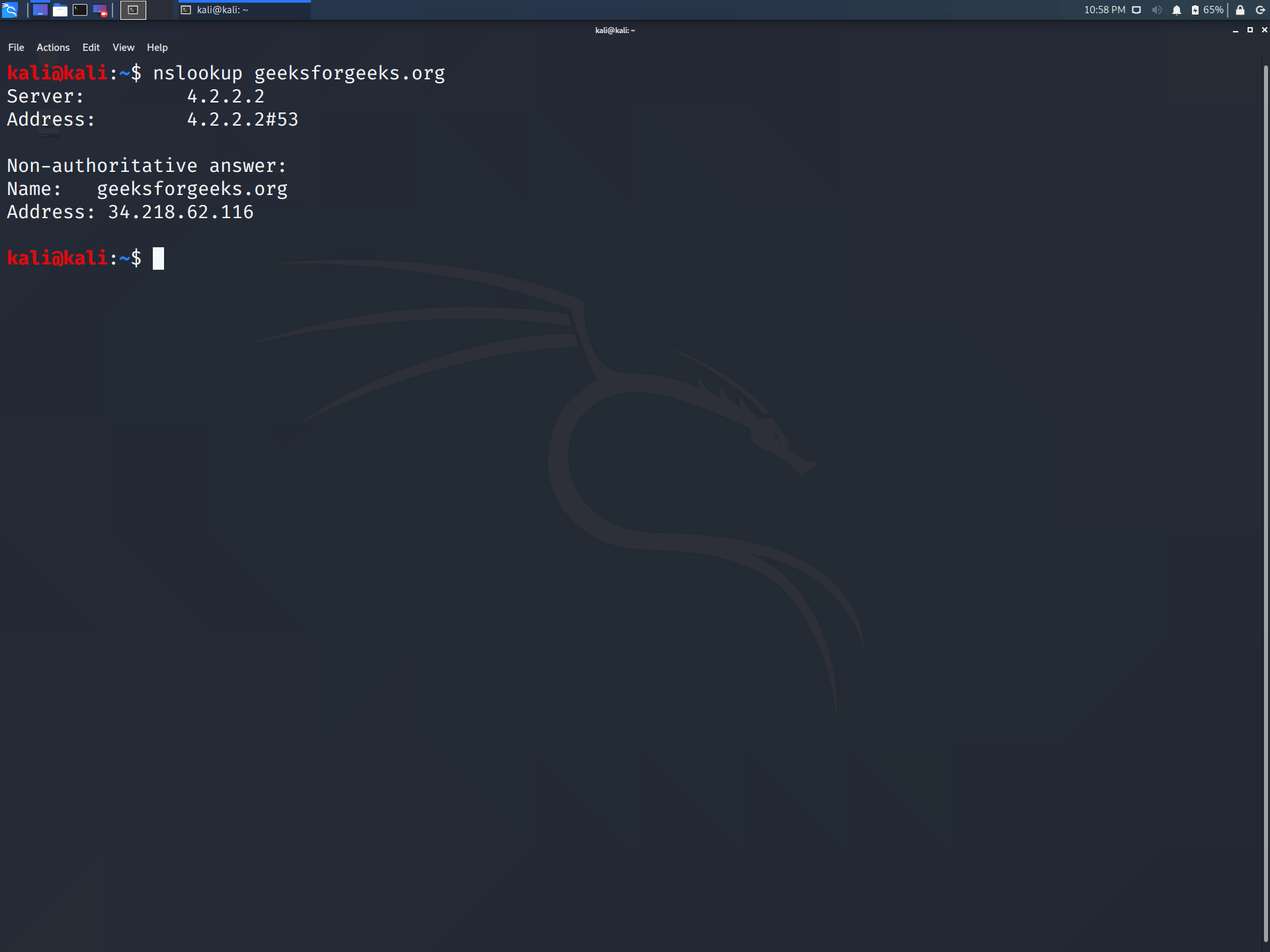
whois geeksforgeeks.org
Replace geeksforgeeks.org with the name of the website you want to lookup.
4. SPARTA
SPARTA is a python based Graphical User Interface tool which is used in the scanning and enumeration phase of information gathering. It is a toolkit having a collection of some useful tools for information gathering. It is used for many purposes, a few of them are listed below.
- It is used to export Nmap output to an XML file.
- It is used to automate the process of Nikto tool to every HTTP service or any other service.
- It is used to save the scan of the hosts you have scanned earlier in order to save time.
- It is used to reuse the password which is already found and is not present in the wordlist.
To use SPARTA, enter the IP address of the host you want to scan in the host section to start scanning.
nslookup stands for nameserver lookup, which is a command used to get the information from the DNS server. It queries DNS to obtain a domain name, IP address mapping, or any other DNS record. It even helps in troubleshooting DNS-related problems. It is used for many purposes, a few of them are listed below.
- To get the IP address of a domain.
- For reverse DNS lookup
- For lookup for any record
- Lookup for an SOA record
- Lookup for an ns record
- Lookup for an MX record
- Lookup for a txt record
6. Osintgram
Osintgram is an OSINT tool to run on reconnaissance Instagram to collect and analyze. It offers an interactive shell to perform analysis on account of any users by its nickname. One can get:
- – addrs : It gets all registered addressed by target photos.
- – captions : It gets the user’s photos captions.
- – comments : It gets total comments of the target’s posts.
- – followers : It gets target followers.
- – followings : It gets users followed by the target.
- – fwersemail : It gets emails of target followers.
- – fwingsemail : It gets an email of users followed by the target.
- – fwersnumber : It gets the phone number of target followers.
- – fwingsnumber : It gets the phone number of users followed by the target.
- – hashtags : It gets hashtags used by the target.

Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...