JitterBug – Tool to Search Basic Info, Open Ports and Potential CVE’s
Last Updated :
23 Sep, 2021
Many peoples think that hacking the target is quite an easy and simple process, but actually, it’s not like so. The methodology and the techniques are to be learned for performing the attack on the target domain. Tester has to perform the initial phases of the Hacking to Gather the information, Scan the target and prepare the plan of attack. Identification of Vulnerability is the main step that helps the attacker to actually hack the target. JitterBug is an automated tool developed in the Shell which can scan system vulnerabilities with the external this-party databases without actually interacting with the target. This makes the attacker hide his identity or log on to the target. JitterBug tool is available on GitHub, it’s free and open-source to use.
Installation of JitterBug Tool on Kali Linux OS
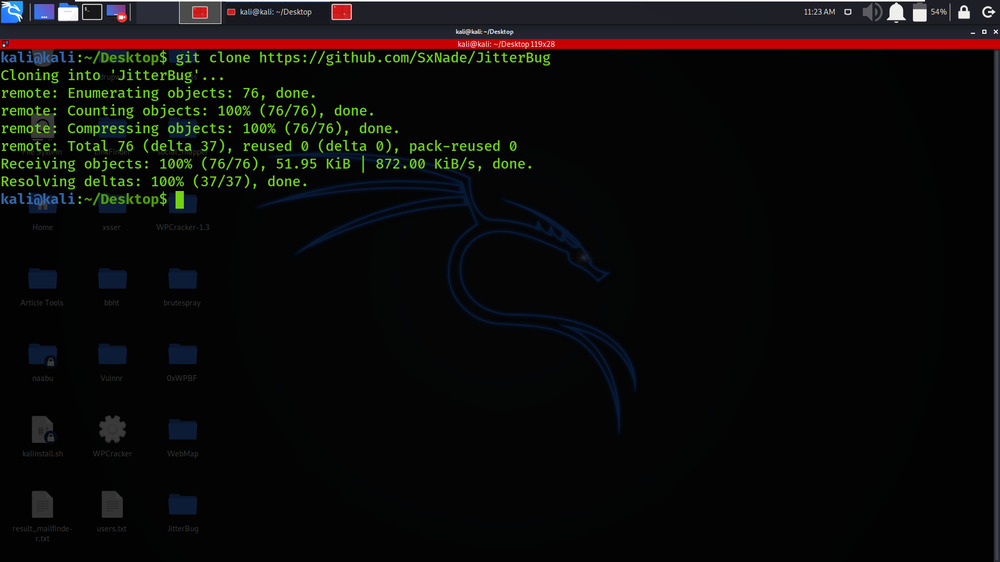
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/SxNade/JitterBug
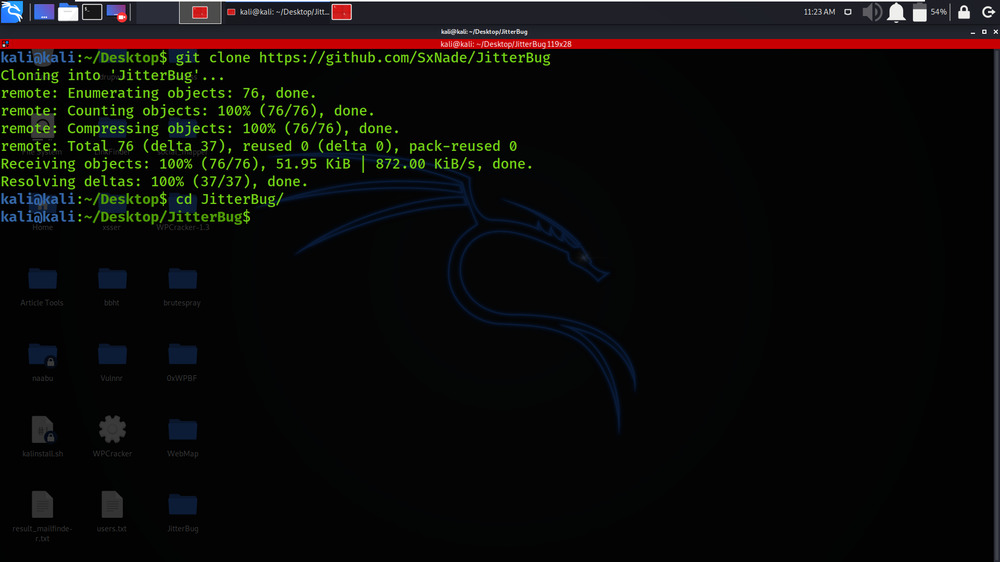
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd JitterBug
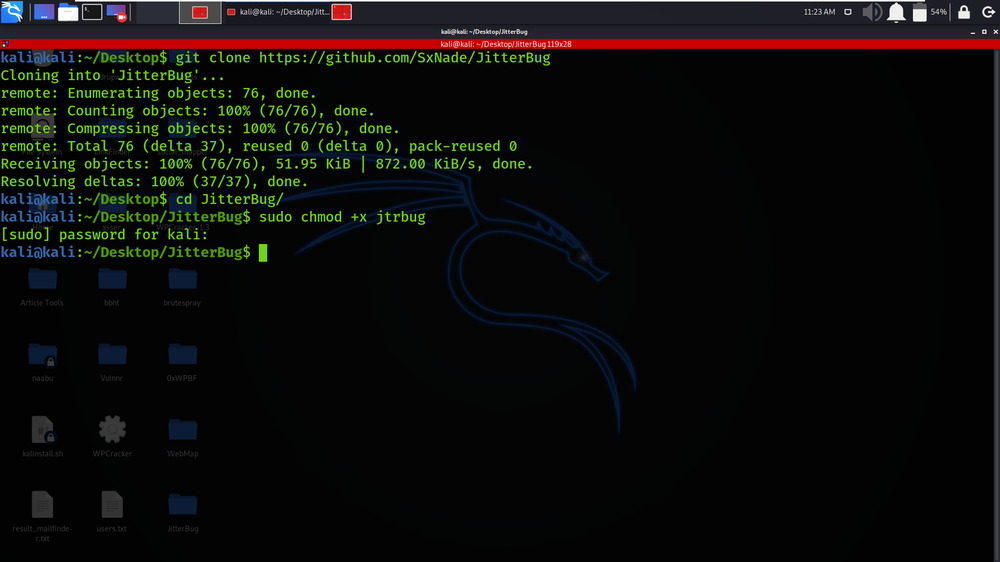
Step 3: Change the permissions of the jitterbug file by using the following command.
sudo chmod +x jtrbug
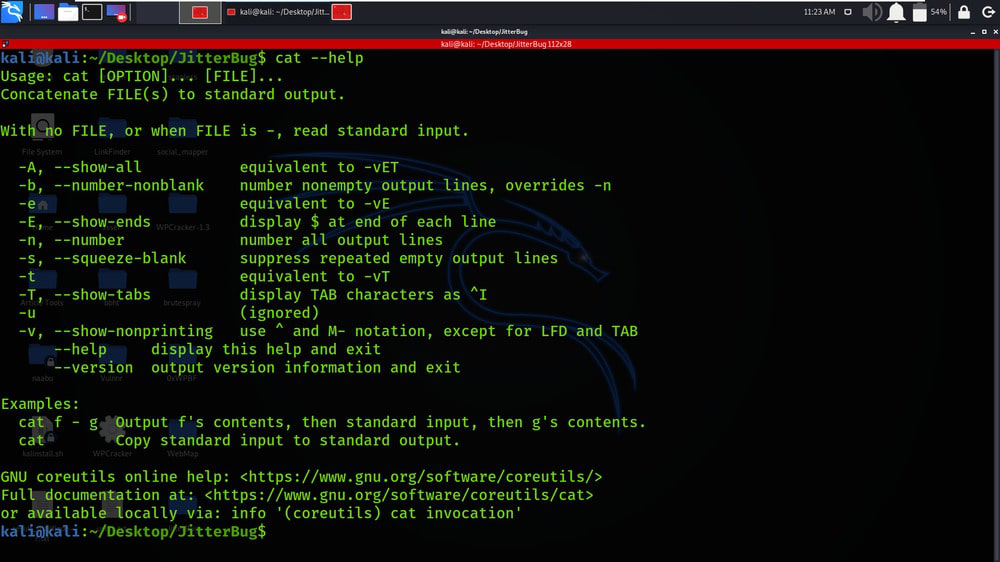
Step 4: Run the below command to verify the installation.
cat --help
Working with JitterBug Tool on Kali Linux OS
Example: Scanning the target IP Address
./jtrbug 208.82.183.220
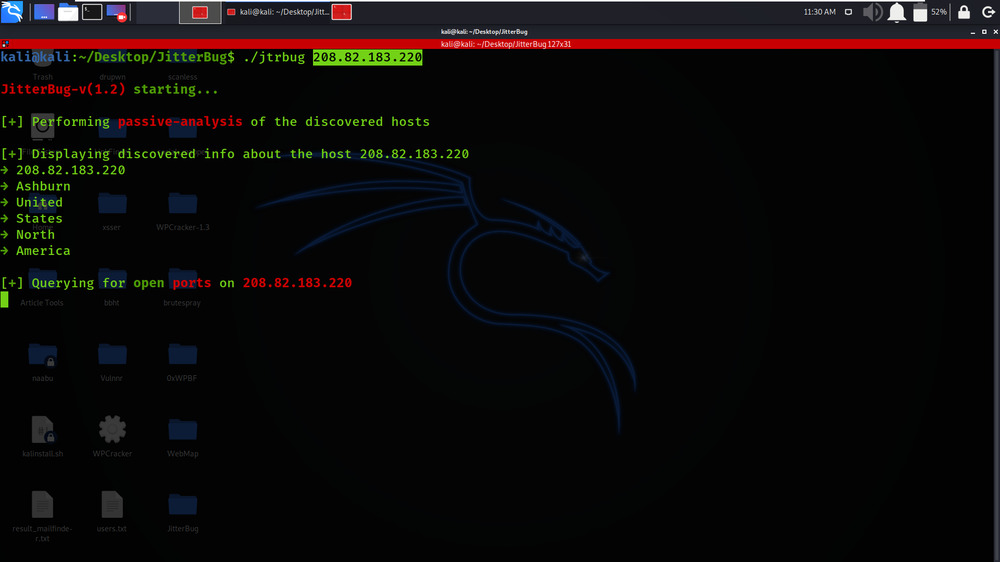
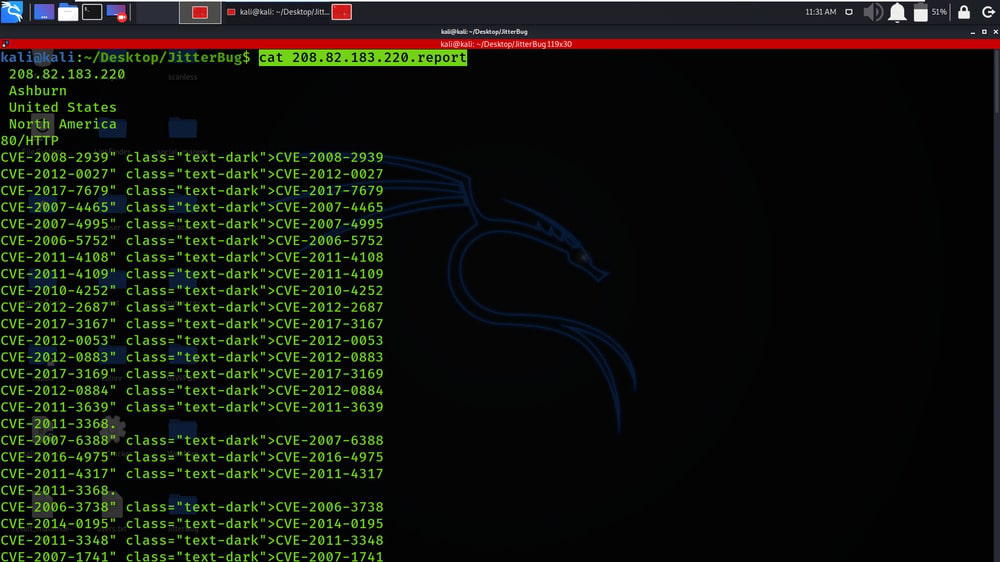
We have got the discovered info about the host 208.82.183.220
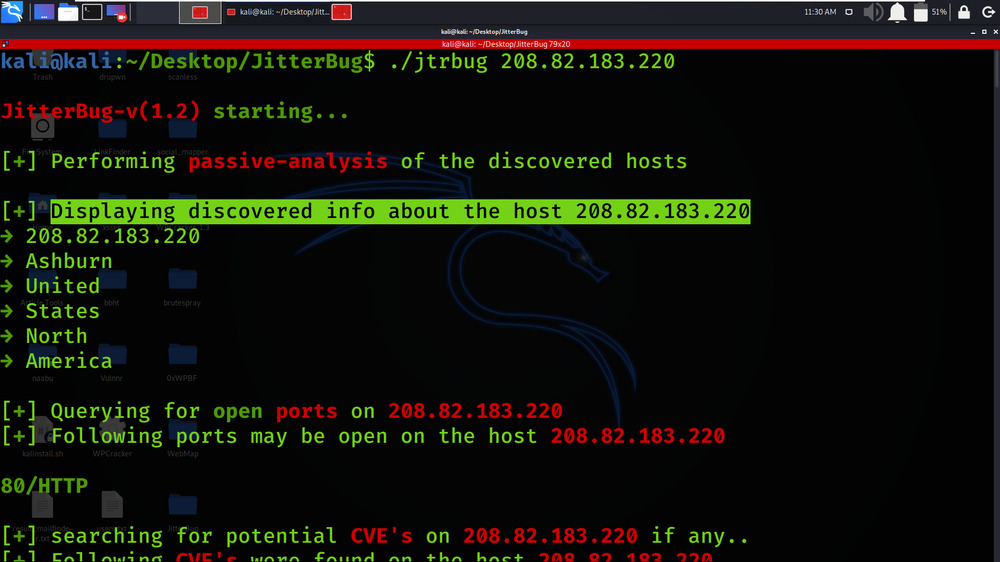
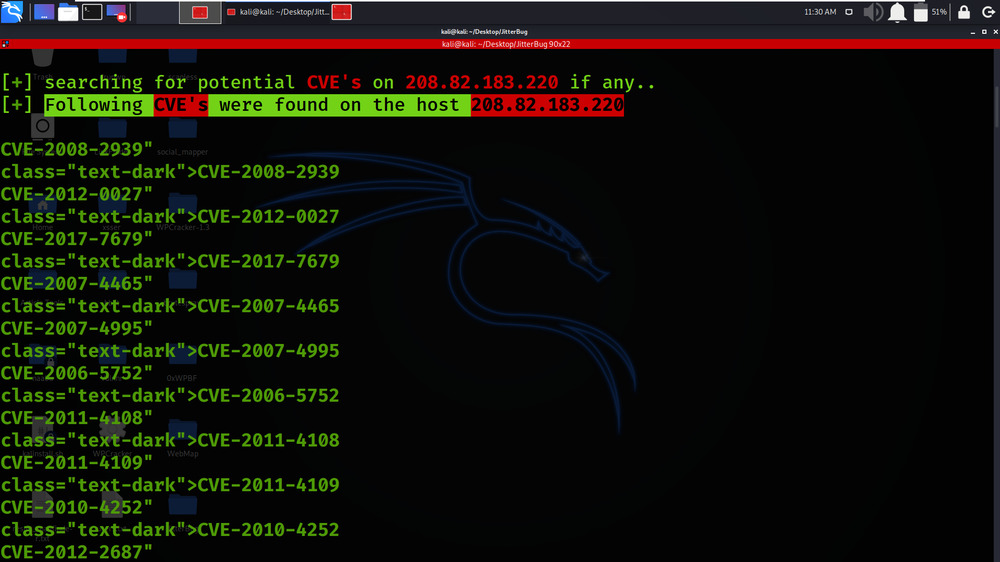
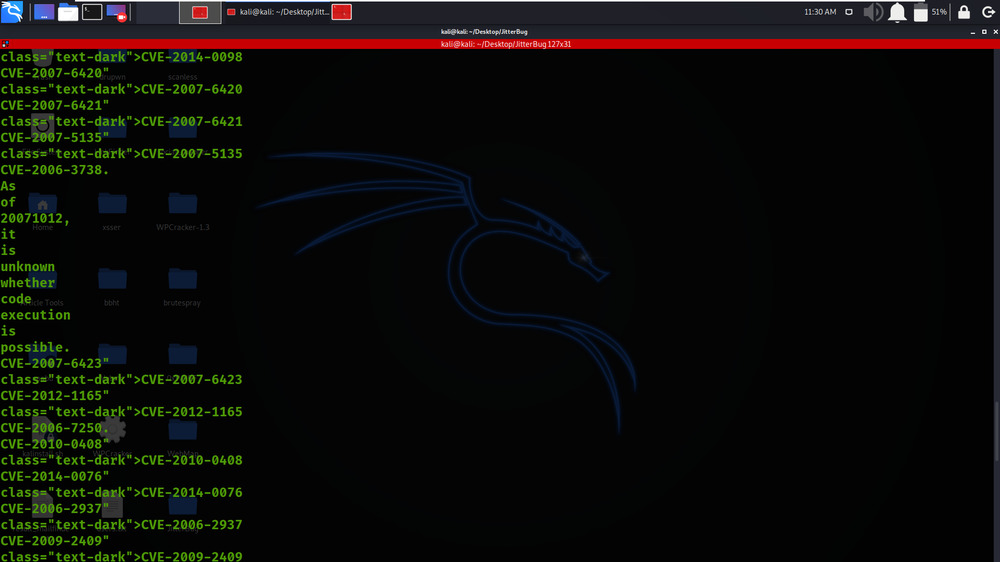
We got the list of CVE’s found on the target.
For Displaying the results, use the following command.
cat 208.82.183.220.report
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...