J-dorker – Website List grabber from Bing
Last Updated :
28 Nov, 2021
J-dorker tool is an automated tool that is used to fetch the links from Bing Search engine which matches the dork query. These links can be vulnerable if the dork query seems to fetch the vulnerable link. J-dorker tool inputs the multiple dork queries and returns the links or domains and saves them into a database which is provided by the tool itself. J-dorker tool is developed in the Python language and tool is a menu-driven tool. This tool is also available on the GitHub platform for free. It’s also open-source so you can contribute to it.
Note: Make Sure You have Python Installed on your System, as this is a python-based tool. Click to check the Installation process: Python Installation Steps on Linux
Installation of J-dorker Tool on Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/0xc01/J-dorker.git
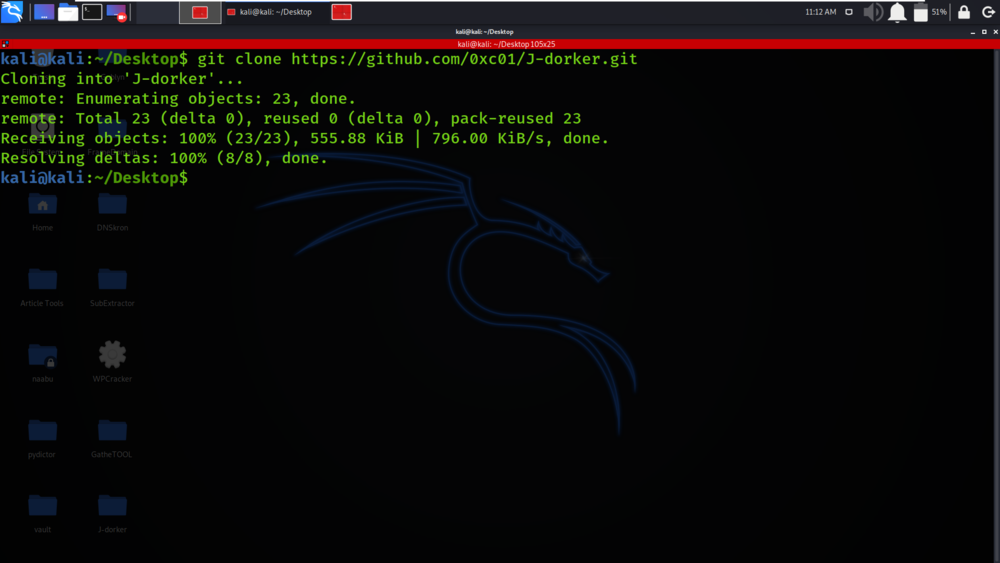
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd J-dorker
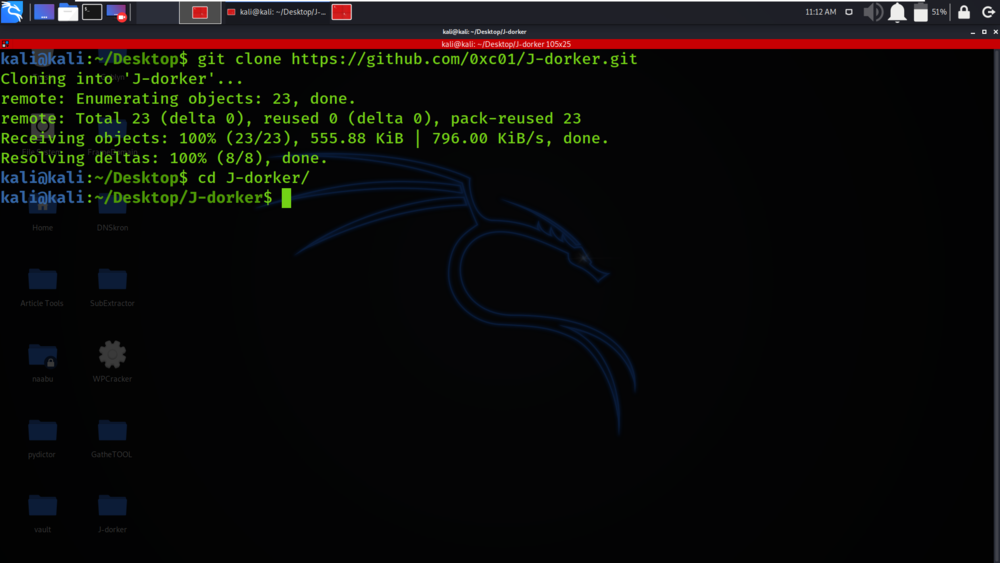
Step 3: Now use the following command to run the tool.
python3 priv8dorker.py
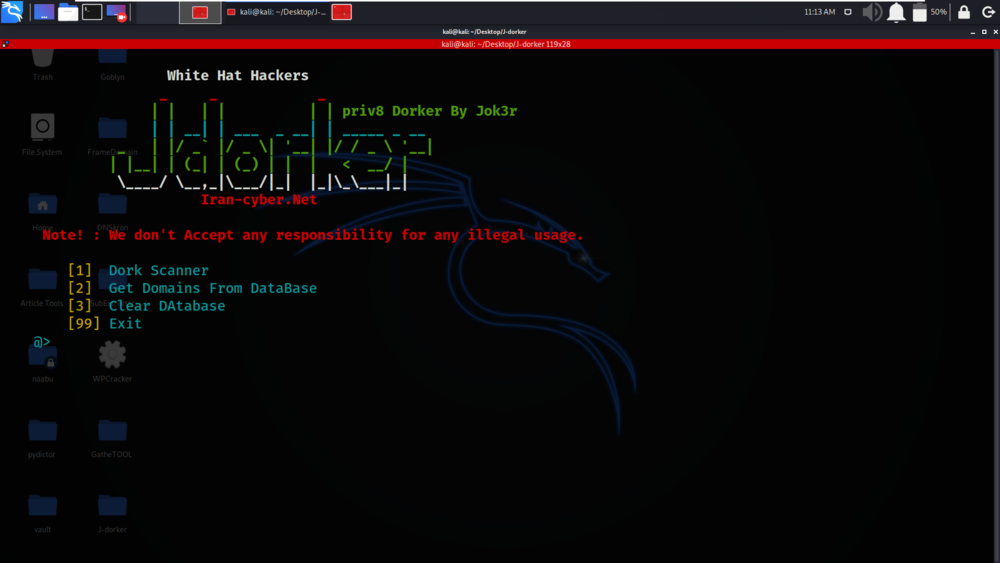
Working with J-dorker Tool on Kali Linux OS
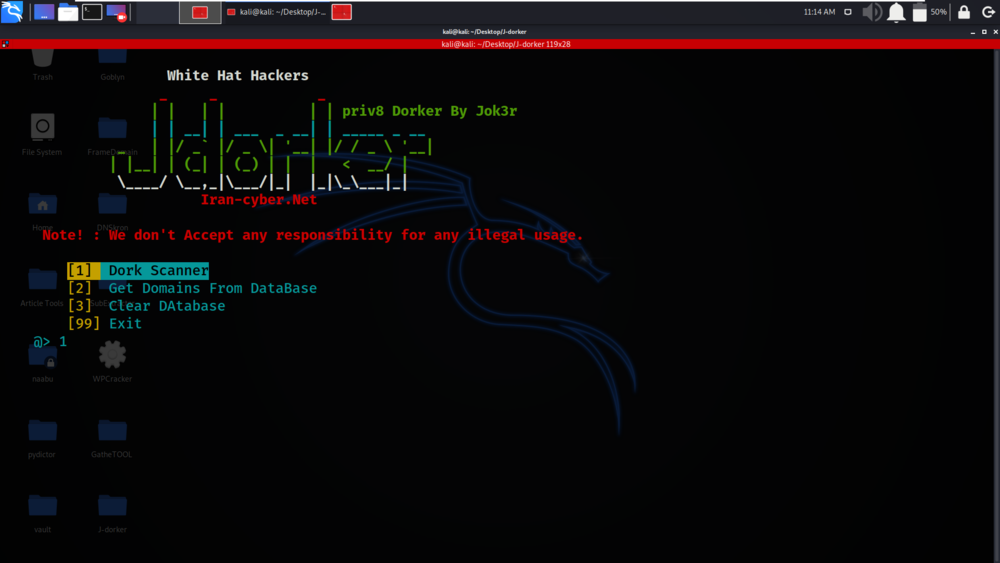
Example 1: Dork Scanner
Select Option 1 for Dork Scanner
We have selected option 2 for Dork Scanner.
In the below screenshot, we have displayed the google dork queries through which domains will be fetched.
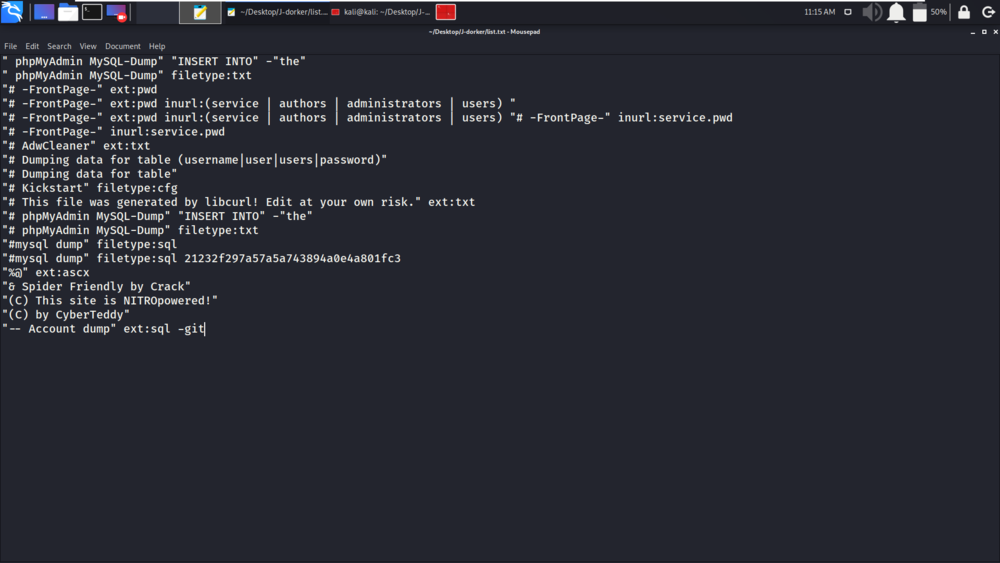
We have given the above list.txt as input to scan.
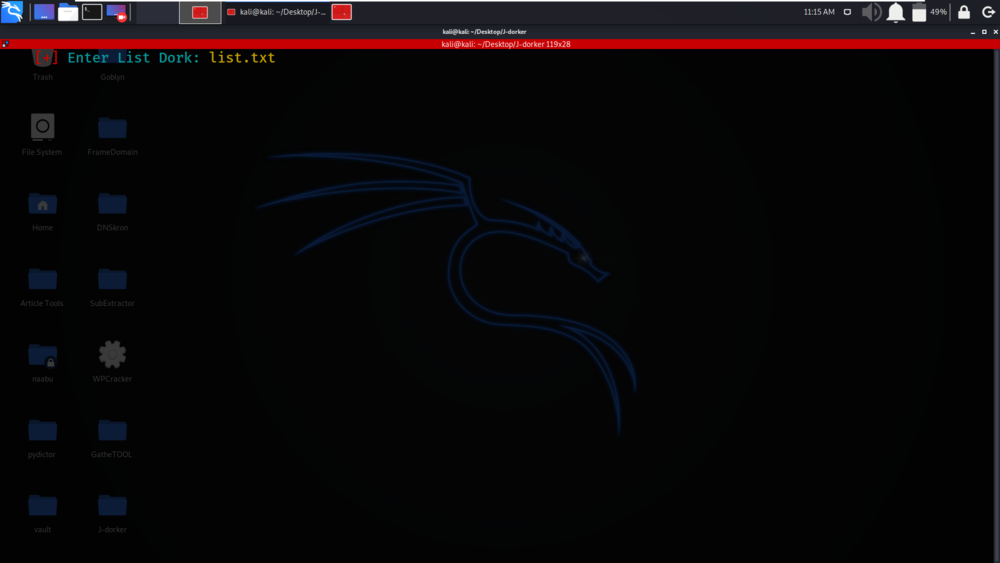
We have got the results of our scan.
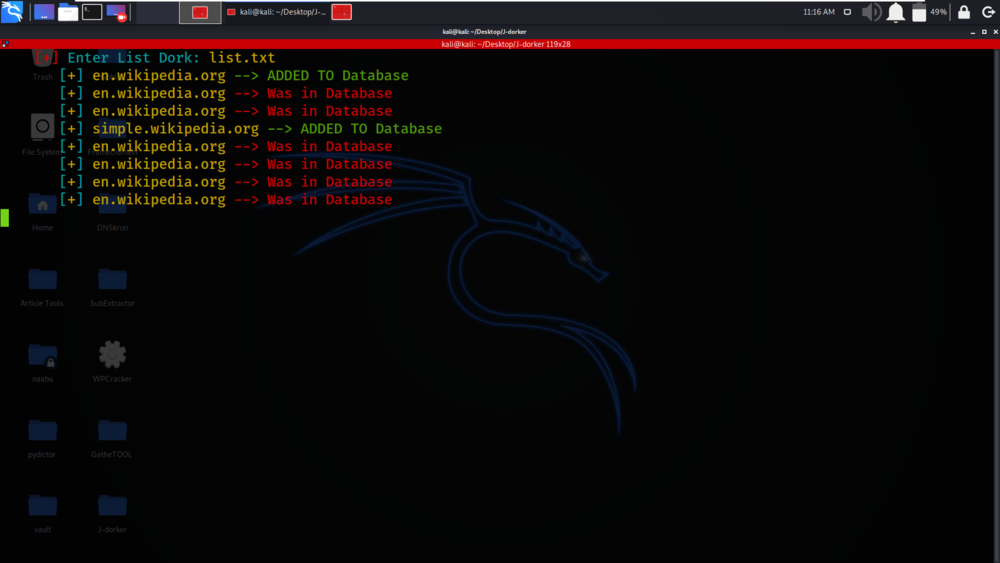
Example 2: Get Domains from Database
Select Option 2 for Get Domains from Database
In this example, we will be displaying the added domains in database.
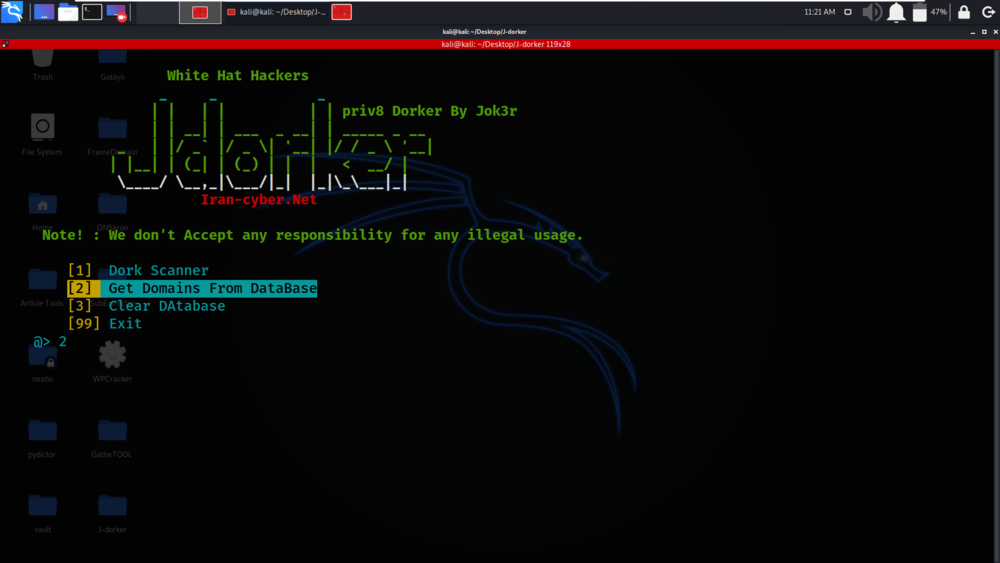
Results are been saved in urls.txt file.
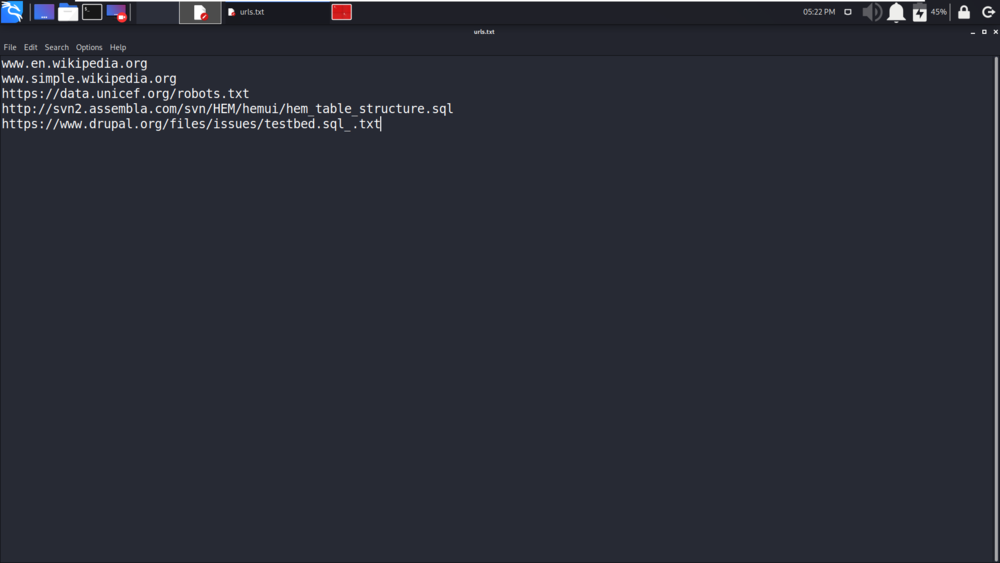
We have displayed the results from urls.txt file.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...