Introduction to SSH(Secure Shell) Keys
Last Updated :
11 Feb, 2024
The SSH(Secure Shell) is an access credential that is used in the SSH Protocol. In other words, it is a cryptographic network protocol that is used for transferring encrypted data over the network. The port number of SSH is 22(Twenty-Two). It allows you to connect to a server, or multiple servers, without having to remember or enter your password for each system that is to log remotely from one system to another. It always comes in key pairs:
- Public key – Everyone can see it, no need to protect it. (for encryption function).
- Private key – Stays in computer, must be protected. (for decryption function).
Key pairs can be of the following types:
- User Key – If the public key and private key remain with the user.
- Host Key – If public key and private key are on a remote system.
- Session key – Used when a large amount of data is to be transmitted.
Features of SSH
- Encryption: Encrypted data is exchanged between the server and client, which ensures confidentiality and prevents unauthorized attacks on the system.
- Authentication: For authentication, SSH uses public and private key pairs which provide more security than traditional password authentication.
- Data Integrity: SSH provides Data Integrity of the message exchanged during the communication.
- Tunneling: Through SSH we can create secure tunnels for forwarding network connections over encrypted channels.
SSH Functions
There are multiple functions performed by SSH Function, here below are some functions:
- SSH provides high security as it encrypts all messages of communication between client and server.
- SSH provides confidentiality
- SSH allows remote login, hence is a better alternative to TELNET
- SSH provides a secure File Transfer Protocol, which means we can transfer files over the Internet securely
- SSH supports tunneling which provides more secure connection communication
SSH Protocol
To provide security between a client and a server the SSH protocol uses encryption. All user authentication and file transfers are encrypted to protect the network against attacks.

SSH Protocol
Techniques Used in SSH
There are majorly three major techniques used in SSH, which are
- Symmetric Cryptography: In Symmetric key cryptography the same key used for encrypting and decrypting the message, a unique single shared key is kept between the sender and reciever. For ex: DES (Data Encryption Standard) and AES (Advanced Encryption Standard).
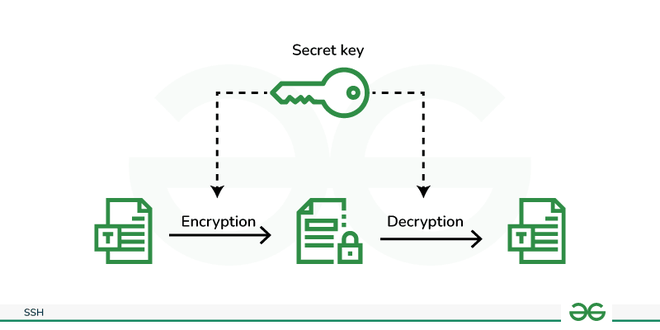
Symmetric Cryptography
- Asymmetric Cryptography: In Asymmetric key cryptography the key used for encrypting is different from the key used for decrypting the message. For ex: RSA (Rivest–Shamir–Adleman) and Digital Signature Algorithm.

Asymmetric Cryptography
- Hashing: Hashing is a procedure used in cryptography which convert variable length string to a fixed length string, this fixed length value is called hash value which is generated by hash function.
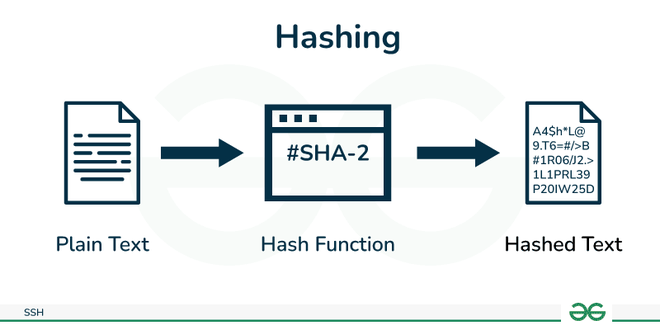
Hashing
Commands in SSH
There are multiple commands supported by SSH protocol, you can tap on the link if you want to know commands in SSH
How does generally WorkThe general asymmetric?
For performing encryption and decryption it uses asymmetric cipher. There are many encryption methods:
rsa, dsa, ed25519 etc.
The general procedure is:
- Public keys from the local computers (system) are passed to the server which is to be accessed.
- The server then identifies if the public key is registered.
- If so, the server then creates a new secret key and encrypts it with the public key which was sent to it via local computer.
- This encrypted code is sent to the local computer.
- This data is unlocked by the private key of the system and is sent to the server.
- The server after receiving this data verifies the local computer.
- SSH creates a route and all the encrypted data are transferred through it with no security issues.
SSH is key-based authentication that is not prone to brute-force attack. It is more convenient and secure than login IDs and passwords (which can be stolen in the middle). There is no exposure of valid credentials, if a server has been compromised.
Generating an SSH key pair
Open your command prompt
type : ssh-keygen
Press enter
It will ask you for a location. Press Enter for default location.
If its already there, press 'y' to overwrite.
You may enter passphrase as you like, press enter.
An example of generating an SSH Key pair in the latest version of Windows 10 is given below:
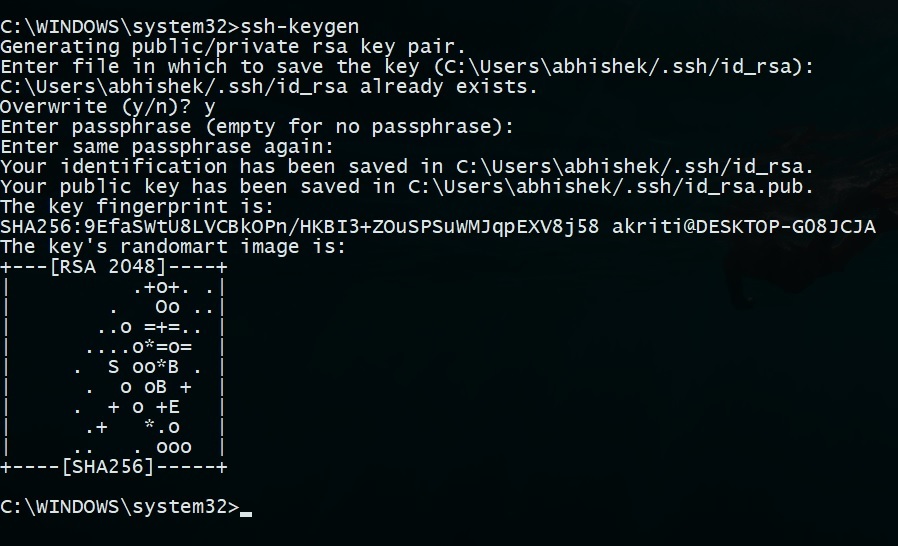
Generating SSH keys on Windows, Linux, generallywhich and Mac:
OMAC OsX and Linux : terminal (build in)
OWindows :- PuTTY
Frequently Asked Question on SSH – FAQs
What is SSH?
SSH(Secure Shell) is an access credential that is used in the SSH Protocol. In other words, it is a cryptographic network protocol that is used for transferring encrypted data over the network.
How does SSH provide security?
It disintegrates the data that travels over the network via encryption. All that a receiving party would discover is something like to static, meaningless random data that requires decryption.
What is the default port number of SSH?
The default port number of SSH is 22.
Distinguish between SSH1 and SSH2?
SSH2 solely employs host keys for system authentication, SSH1 encrypts distinct portions of the packets and uses both server and host keys. SSH2 uses a different networking technology than SSH1, and it is a total redesign of the protocol. SSH2 is also more secure.
What is port forwarding in SSH?
The method of sending data over an encrypted secure shell connection between a local and remote server is called SSH port forwarding, or SSH tunnelling.
Share your thoughts in the comments
Please Login to comment...