Introduction To Security Defense Models
Last Updated :
22 May, 2020
These models are mainly used for Defense Purpose i.e., securing the data or the asset.
There are 2 main types of Security Defense Models: Lollipop Model, and Onion Model. These are explained as following below.
1. Lollipop Model :
Lollipop Model is Defense Model associated with an analogy of a Lollipop. A lollipop is having a chocolate in the middle and around the chocolate, there is a layer of crust, mainly of sugar flavored syrup. A person licks and licks the lollipop and finally, the chocolate in the middle is exposed.
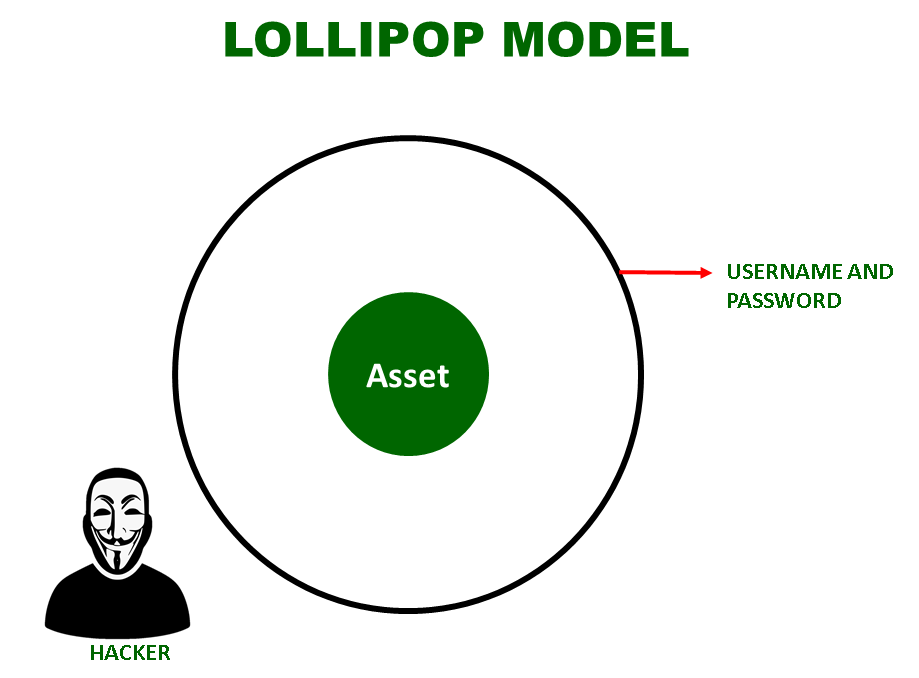
Mapping this analogy of Lollipop to the Model, as shown in the above diagram, the hacker just needs to break that one layer of security to get hands on the asset, in this case, say it is Username and Password. Once it is done, the hacker can access the asset. So Lollipop Model is not a good model for Network Security.
2. Onion Model :
Onion Model is Defense Model associated with an analogy of an Onion. An Onion is a vegetable which is composed of layers. Only by peeling each layer, we can get to the center of the Onion. Also, while peeling, we get tears in our eyes.
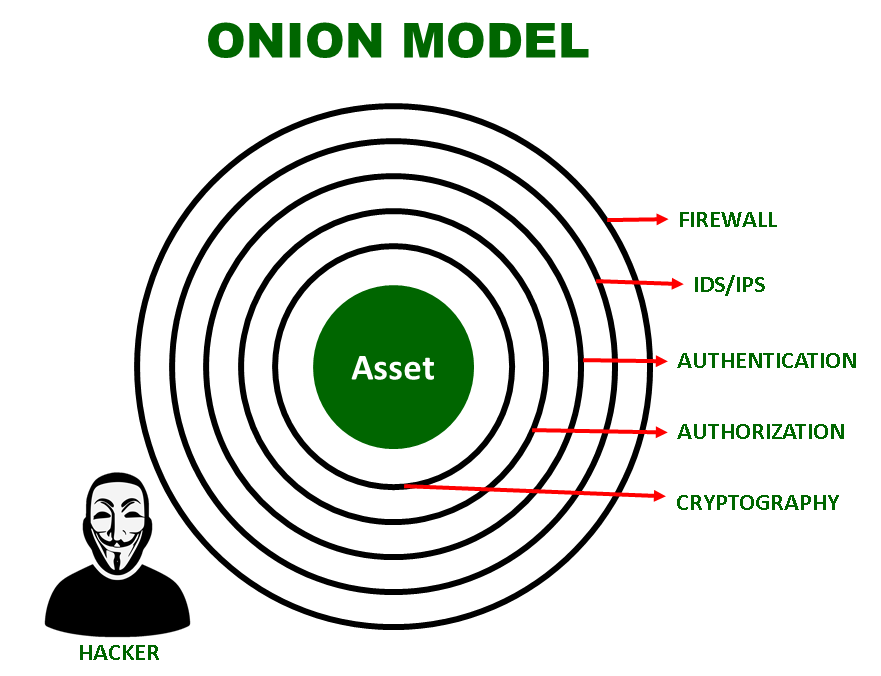
Mapping this analogy of Onion to the Model, as shown in the above diagram, the hacker needs to break all the layers of security to get access to the asset. Breaking each layer i.e., Firewall, IDS/IPS, Authentication, Authorisation, and Cryptography in this case, should bring tears to his eyes. In simple words, breaking each layer should be complex and extremely challenging for the hacker. So Onion Model is considered as a good model for Network Security.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...