Introduction of Botnet in Computer Networks
Last Updated :
22 Jun, 2023
A Network of compromised computers is called a botnet. Compromised computers are also called Zombies or Bots. This software is mostly written in C++ & C. The main motive of botnet is that it starts with the dark side of the internet which introduced a new kind of Crime called Cybercrime.
Among the malware (malicious software) botnet is the most widespread and severe threat. Several large institutions, government organizations, and almost every social networking website Facebook, Twitter, Instagram, etc, e-commerce website Amazon, and Flipkart, etc, in short, every firm associated with the internet became the victim of this malware. This kind of malicious software is freely available in the market for lease. It can be used in DDoS attacks (Smurf Attacks), Phishing, Extortion, etc.
-768.png)
Botnets
Botnet Communication
At first, those who want to be botmaster finds the target system (here target system means finding the vulnerable system), then use popular social engineering techniques like phishing, click fraud, etc to install a small (Kbs) executable file into it. A small patch has been included in the code, making it not visible even with the running background process. A naive user won’t even come to know that his/her system became part of a bot army. After infection, the bot looks for the channel through which it can communicate with its master. Mostly Channel (command and Control channel) uses the existing protocol to request the command and receive updates from the master, so if anyone tries to look at the traffic behavior then it will be quite difficult to figure it out. Botmaster is used to write scripts to run an executable file on different OS.
For Windows: Batch Program
For Linux: BASH Program
The following are the major things that can be performed on bots:
- Web-Injection: Botmaster can inject snippets of code to any secured website that which bot used to visit.
- Web filters: Here on use a special symbol like:”!” for bypassing a specific domain, and “@” for the screenshot used.
- Web-fakes: Redirection of the webpage can be done here.
- DnsMAP: Assign any IP to any domain which the master wants to route to the bot family.
Types of Botnet
Here are the types of botnets mentioned below based on the Channel.
Internet Relay Chat (IRC) Botnet
Internet Relay Chat (IRC) acts as the C&C Channel. Bots receive commands from a centralized IRC server. A command is in the form of a normal chat message. The limitation of the Internet Relay Chat(IRC) Botnet is that the Entire botnet can be collapsed by simply shutting down the IRC Server.
Peer-to-Peer (P2P) Botnet
It is formed using the P2P protocols and a decentralized network of nodes. Very difficult to shut down due to its decentralized structure. Each P2P bot can act both as the client and the server. The bots frequently communicate with each other and send “keep alive” messages. The limitation of Peer-to-Peer Botnets is that it has a higher latency for data transmission.
Hyper Text Transfer Protocol (HTTP) Botnet
Centralized structure, using HTTP protocol to hide their activities. Bots use specific URLs or IP addresses to connect to the C&C Server, at regular intervals. Unlike IRC bots, HTTP bots periodically visit the C&C server to get updates or new commands.
How Does it Work?
The working of the Botnet can be defined as either you writing code to build software or using it from the available (Leaked) botnet like ZEUS Botnet(king of all botnet), Mirai botnet, BASHLITE, etc. then finding the vulnerable system where you can install this software through some means like social engineering (e.g Phishing) soon that system becomes a part of a bot army. Those who control it are called the botmaster which communicates its bot army using a command and control channel.

How a Botnet work
Types of Botnet Attacks
Below mentioned are the attacks performed by the Botnets.
- Phishing: Botnets help in distributing malware and suspicious activities via Phishing emails. These include a multiple number of bots and the whole process is automated and it is difficult to shut down.
- Distributed Denial-of-Service(DDoS) Attack: DDoS Attack is a type of attack performed by the Botnets in which multiple requests are sent that leads to the crash of a particular application or server. DDoS Attacks by Network Layer use SYN Floods, UDP Floods, etc to grasp the target’s bandwidth and let them protect from being attacked.
- Spambots: Spambots are a type of Botnet Attack, where they take emails from websites, guestbooks, or anywhere an email id is required to log in. This section covers more than 80 percent of spam.
- Targeted Intrusion: This is one of the most dangerous attacks as they attack the most valuable thing or data, valuable property, etc.
How to Protect Against Botnets?
- The most important way to protect from Botnets is to give training to users about identifying suspicious links.
- Keep the system software always updated to become safe from the Botnets.
- Using two-factor authentication is a way to be safe from the Botnet.
- There are several antiviruses present in the market which keeps you protected from Botnets.
- Try to change passwords on a regular basis for better protection from Botnets.
Botnet Lifecycle
Botnet Lifecycle can be understood with the help of the following diagrams. Here we have illustrated the lifecycle of Botnet in 4 stages as shown in the figure.
Stage-1:
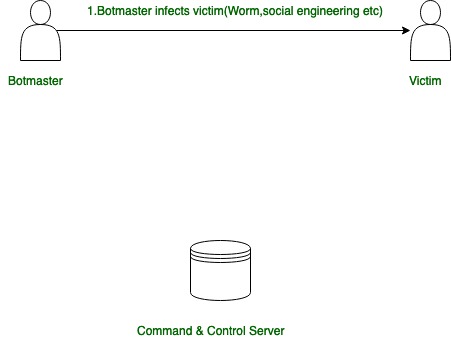
Stage 1
Stage-2:
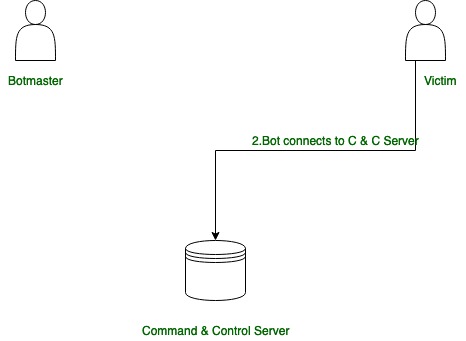
Stage 2
Stage-3:
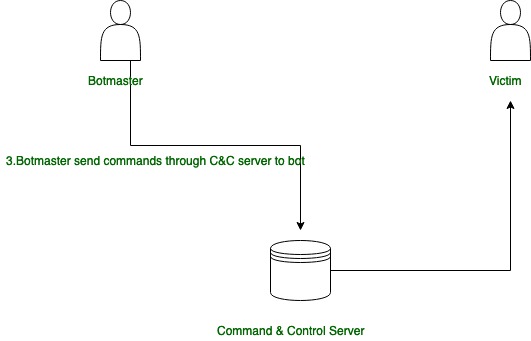
Stage 3
Stage-4:
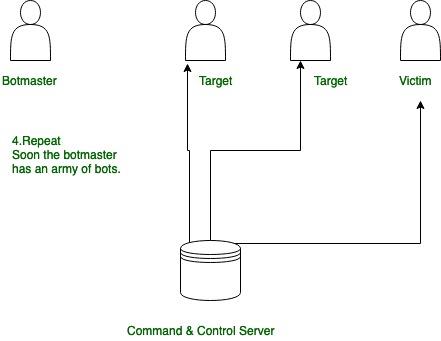
Stage 4
FAQs on Botnets
1. Give an example of a Botnet?
Answer:
One of the example of Botnet is Fraud Online Review, where some fake reviews are generally posted on the device of the user.
2. Where Botnet is used?
Answer:
Botnets are used in:
- Sending Email Spams
- Fraud Campaigning
- DDoS Attacks
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...