RSA algorithm is an asymmetric cryptography algorithm which means, there should be two keys involve while communicating, i.e., public key and private key. There are simple steps to solve problems on the RSA Algorithm.
Example-1:
- Step-1: Choose two prime number
 and
and  Lets take
Lets take  and
and 
- Step-2: Compute the value of
 and
and  It is given as,
It is given as,
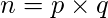 and
and 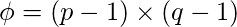
- Here in the example,
 [Tex]\phi = (3-1) \times (11-1) = 2 \times 10 = 20
[/Tex]
[Tex]\phi = (3-1) \times (11-1) = 2 \times 10 = 20
[/Tex] - Step-3: Find the value of
 (public key) Choose
(public key) Choose  , such that
, such that  should be co-prime. Co-prime means it should not multiply by factors of
should be co-prime. Co-prime means it should not multiply by factors of  and also not divide by
and also not divide by  Factors of
Factors of  are,
are,  so
so  should not multiply by
should not multiply by  and
and  and should not divide by 20. So, primes are 3, 7, 11, 17, 19…, as 3 and 11 are taken choose
and should not divide by 20. So, primes are 3, 7, 11, 17, 19…, as 3 and 11 are taken choose  as 7 Therefore,
as 7 Therefore, 
- Step-4: Compute the value of
 (private key) The condition is given as,
(private key) The condition is given as,  where y is the value of
where y is the value of  . To compute the value of
. To compute the value of  ,
,- Form a table with four columns i.e., a, b, d, and k.
- Initialize a = 1, b = 0, d =
 , k = – in first row.
, k = – in first row. - Initialize a = 0, b = 1, d =
 ,
,  in second row.
in second row. - From the next row, apply following formulas to find the value of next a, b, d, and k, which is given as
- Step-5: Do the encryption and decryption Encryption is given as,
 Decryption is given as,
Decryption is given as,  For the given example, suppose
For the given example, suppose  , so Encryption is
, so Encryption is  Decryption is
Decryption is  Therefore in the final,
Therefore in the final,  ,
,  ,
,  ,
,  ,
,  and
and 
Example-2: GATE CS-2017 (Set 1) In an RSA cryptosystem, a particular A uses two prime numbers p = 13 and q =17 to generate her public and private keys. If the public key of A is 35. Then the private key of A is?
 and
and 
- Compute
 and
and 
 (public key)
(public key)- Compute
 (private key)
(private key)
 (private key)
(private key)
Example-3: In RSA algorithm if p = 7, q = 11 and e = 13 then what will be the value of d?
Step:
1) Calculate value of n = p × q, where p and q are prime no.’s
2) calculate Ø(n) = (p-1) × (q-1)
3) consider d as public key such that Ø(n) and d has no common factors.
4) consider e as private key such that (e × d) mod Ø(n) = 1
5) Cipher text c = message i.e. md mod n
6) message = cipher text i.e. ce mod n
Calculation
p =7, q= 11, e = 13
Use step 2 and 4 of RSA algorithm to calculate private key.
Ø(n) = (7– 1) × (11 – 1) = 6 × 10 = 60
Now,
(e × d) mod Ø(n) = 1
(13 × d) mod 60 = 1
d = 37
So, key of A = 37
Example-4: In an RSA cryptosystem, a participant uses two prime numbers p = 3 and q = 11 to generate his public and private keys. If the private key is 7, then how will the text COMPUTER be encrypted using the public key?
Step:
RSA Algorithm:
Step 1: Calculate value of n = p × q, where p and q are prime no.’s
Step 2: calculate Ø(n) = (p-1) × (q-1)
Step 3: consider d as a private key such that Ø(n) and d have no common factors. i.e greatest common divisor (Ø(n) , d ) = 1
Step 4: consider e as a public key such that (e × d) mod Ø(n) = 1.
Step 5: Ciphertext = message i.e. me mod n.
Step 6: message= cipher text i.e. cd mod n.
Calculation:
Given prime numbers, p =3, q = 11
n= 3 x 11 =33
Ø(n) = (3-1) × (11-1) = 2 x 10 =20
greatest common divisor (20, d) =1
d = Private Key = 7
As per question d =7.
(e × d) mod Ø(n) = 1
(e x 7) mod 20 = 1
So, e x 7= 20 x 1+1
e= 217= 3 possible.
,e = public Key=3 =encrypt key
So n = 33 ,e = 3 , d = 7, Ø(n) = 20
Plan text = COMPUTER
Ciphertext = me mod n.
Ciphertext for C = 33 mod 33 = 27
Ciphertext for O = 153 mod 33 = 9
Ciphertext for M = 133 mod 33 = 19
Ciphertext for P = 163 mod 33 = 4
Ciphertext for U = 213 mod 33 = 21
Ciphertext for T = 203 mod 33 = 14
Ciphertext for E = 53 mod 33 = 26
Ciphertext for R = 183 mod 33 = 24.
Example-5: Using ‘RSA’ algorithm, if p = 13, q = 5 and e = 7, the value of d and cipher value of ‘6’ with (e, n) key are
RSA Algorithm:
Step 1: Calculate value of n = p × q, where p and q are prime no.’s
Step 2: calculate Ø(n) = (p-1) × (q-1)
Step 3: consider d as a private key such that Ø(n) and d have no common factors. i.e greatest common divisor (Ø(n) , d ) = 1
Step 4: consider e as a public key such that (e × d) mod Ø(n) = 1.
Step 5: Ciphertext = message i.e. me mod n.
Step 6: message= cipher text i.e. cd mod n.
Calculation:
To find the value of ‘d’ in the RSA algorithm, we need to calculate the modular multiplicative inverse of ‘e’ modulo φ(n), where n is the product of the two prime numbers p and q, and φ(n) is the Euler’s totient function.
Given:
p = 13
q = 5
e = 7
ciphertext = 6
First, calculate n:
n = p × q
n = 13 × 5
n = 65
Next, calculate φ(n):
Ø(n) = (p – 1) × (q – 1)
Ø(n) = (13 – 1) × (5 – 1)
Ø(n)= 12 × 4
Ø(n) = 48
Now, we need to find the modular multiplicative inverse of ‘e’ modulo Ø(n). In other words, we need to find ‘d’ such that (e * d) mod Ø(n) = 1.
Using the extended Euclidean algorithm, we can find ‘d’:
Step 1:
48 = 7 × 6 + 6
7 = 6 × 1 + 1
Step 2:
6 = 1 * 6 + 0
Since the remainder in the last step is 1, we can conclude that the greatest common divisor of 7 and 48 is 1. Therefore, ‘d’ exists, and it is the coefficient of 7 in the equation:
1 = 7 – 6 × 1
So, ‘d’ is equal to 7.
Now, to decrypt the ciphertext using the private key (d, n), we can use the formula:
plaintext = (ciphertextd) mod n
Substituting the values:
plaintext = (67) mod 65
Calculating this:
plaintext = 279936 % 65
plaintext = 46
Therefore, the value of ‘d’ is 7 and the plaintext (decrypted value) of the ciphertext ‘6’ using the private key (d, n) is 46.
Solving RSA algorithm problems usually involves the following steps:
- Choose two prime numbers: Start by selecting two large prime numbers, p and q, and compute their product, n = p * q. This product forms the modulus for the RSA algorithm.
- Compute Euler’s totient function: Compute Euler’s totient function, phi(n) = (p-1) * (q-1). This value is used to generate the public and private keys.
- Choose the public key: Choose a number e that is relatively prime to phi(n). This means that e and phi(n) share no common factors other than 1. The public key consists of the pair (e,n).
- Compute the private key: Compute the modular multiplicative inverse of e modulo phi(n). This can be done using the extended Euclidean algorithm. The private key consists of the pair (d,n).
- Encrypt a message: To encrypt a message, first convert it to a number m. Then compute the ciphertext c = m^e mod n.
- Decrypt a message: To decrypt a message, compute the plaintext m = c^d mod n.
Here are some tips for solving RSA algorithm problems:
- Choose large prime numbers: The strength of the RSA algorithm depends on the size of the prime numbers used. For security purposes, it is recommended to choose prime numbers that are at least 1024 bits long.
- Use a calculator or programming language: Performing the calculations by hand can be difficult and time-consuming. Instead, use a calculator or a programming language that supports large integers.
- Check your calculations: RSA calculations involve many large numbers, so it’s easy to make mistakes. Double-check your calculations to make sure you haven’t made any errors.
- Practice with examples: Practice solving RSA problems with examples to get a better understanding of the algorithm. There are many online resources that provide RSA examples and practice problems.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...