Here we will discuss how to use Steghide on Kali Linux to hide and remove hidden data within an image. Various Steganography tools are available, but the part that sets it apart is that it uses a variety of algorithms to encrypt data. In addition, Steghide supports to cover data behind any image (jpg / jpeg / png / gif / BMP), audio (mp3 / wav) etc.
Introduction to Steghide:
Steghide is a steganography program capable of hiding data in a various variety of image and audio files. The color and sample frequencies aren’t changed sequentially, making the embedding resistant against first-order statistical tests.
Steghide can be a steganography tool that allows you to cover confidential records inside a picture or sound record with a passphrase. Bolsters BMP and JPEG picture group, AU and WAV sound group. This device has its advantages and disadvantages. One upside is that it is much better at covering and can extend a lot without any type of document. It does this by using a propelled calculation to shroud it inside a picture (or sound) record without changing the form (or sound) of the document. This is additionally without using Steghide (or if there is not the same scientific method as Steghide) then it is difficult to remove the hidden documents from the picture.
Features:
- Embedded data compression
- Support for JPEG, BMP, WAV, and AU files
- Embedded data encryption
- Decryption via password
- Uses various algorithms for encryption
- Embedding of a checksum to verify the integrity of extracted data
Introduction to Steganography:
Steganography is the art of hiding data within a non-secret medium. This practice dates back to around 440 BCE since ancient times. In Greece (Cyper, Farley, and Lombardo 2005). The Americans and the British used invisible ink to hide messages from each other in the Revolutionary War. The heat will be applied to the paper to reveal the hidden message.
In digital steganography, electronic communications can involve steganographic coding inside a transport layer, such as a document file, picture file, program, or convention. Media records are perfect for steganographic transmission because their detail is predictable. For example, a sender may start with a harmless picture and make some changes to it to hide the data, so that, this change does not go unnoticed by someone who is not specifically looking for it. is.
The reverse of steganography on cryptography alone means that the planned mystery message does not stand up for itself as an object of examination. Clearly explicitly cleared messages — no matter how unbreakable, provoke intrigue, and may themselves be contained in nations where encryption is illegal. In this manner, while cryptography alone is the act of securing the substance of the message, steganography is concerned with disguising the substance of the message in the same way that a mystery message is being sent.
Installation:
Let’s start with the installation of Steghide. In Windows, we can download Steghide from http://steghide.sourceforge.net/download.php. After downloading we just have to unzip the files and use them via cmd.
In Linux, You must first install Steghide. You can run the following command to see if you have Steghide installed.
which steghide
If nothing is returned then you must run the following command to install the Steghide.
sudo apt-get install steghide -y
The Steghide must now be installed. Run the following command to verify.
which steghide
Getting Started with Steghide:
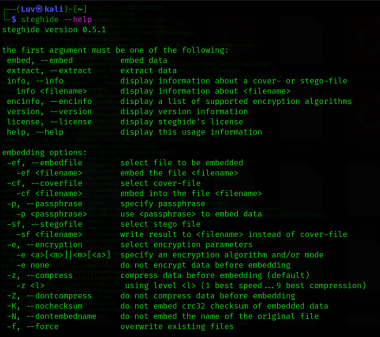
To start Steghide, the most basic option we use is the help command. This command will show us all the options that Steghide offers us.
Run the following command to pull the Steghide help section.
steghide --help
When you are familiar with how the program works, proceed to the next step.
Find a picture:
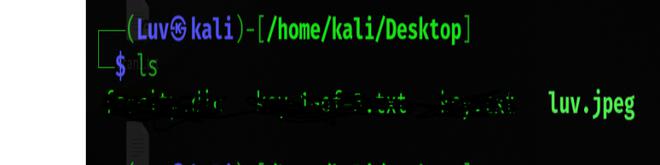
Steghide supports JPEG and BMP image file types. Once you have an image, make sure that it is available on your black machine. In this example, we will use the first JPEG image located in this article. Feel free to grab that image or any other JPEG or BMP file.
In this example, the file name would be “luv.jpeg”.
Your secret text file is ready:
Although we are using text in this example, there is no restriction on the type of format secret data in Steghide. You can embed the image as you wish.
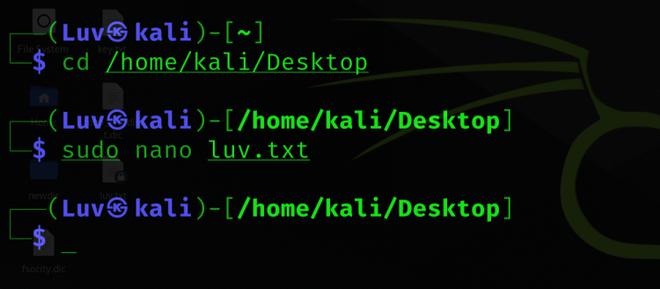
We are going to create a text file called “luv.txt” which we will use to embed in the image. You can use any text editor of your choice or quickly run the following command to create a text file.
cd /home/kali/Desktop
sudo nano luv.txt
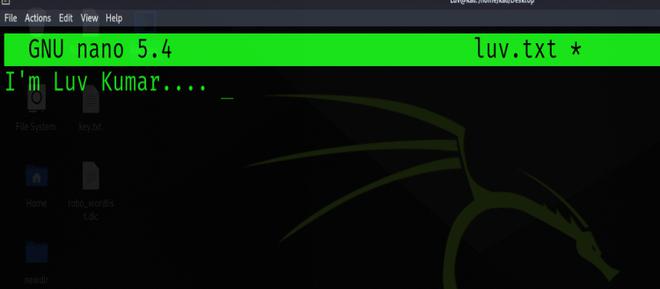
Then, click (ctrl+o), (enter), and then click (ctrl+x).
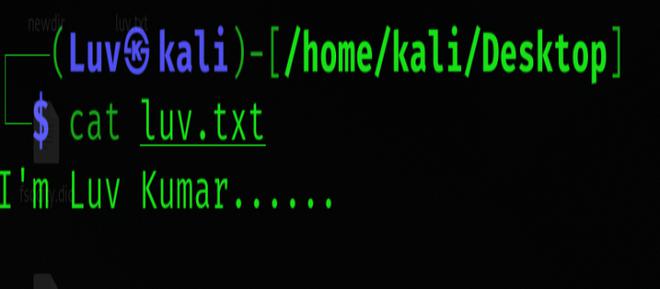
You can check to see if the text file is created and the contents by running the following command.
cat luv.txt
Now that you have your image and text, we are ready to proceed to embed the text in the image.
Embedding data in the image:
We hide the data in the image using the Steghide so that only the person who accepts it can read it. Therefore, we created a text file named “luv.txt”, in which we wrote our confidential data and images. JPEG is the file in which we are embedding our data.
To achieve this, Run the following command to embed “luv.txt” in an image named “luv.jpeg”.
steghide embed -ef luv.txt -cf luv.jpeg
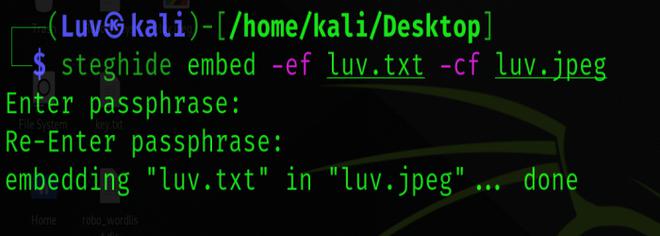
Here, ef and cf are termed as embedded files and cover files, respectively.
Let’s see what this command is doing:
- Steghide – Program Name
- Embed – this is the command
- -cf – This flag is for the cover file (the file used to embed the data)
- filename – this is the name of the cover file
- -ef – This flag is for the embed file (the file that will be embedded)
- Filename – This is the name of the embedded file
You will be prompted to enter a passphrase(luv123). This passphrase will be necessary for anyone trying to extract data from the image. The passphrase is not required. However, anyone trying to extract data will be able to do so.
Extraction of Data From Image Via Steghide:
Using Steghide adds an extra layer of security by allowing us to use a password for it. As long as you know the passphrase, it is quite easy to extract data from the image.
Now, use the following command to remove the hidden data:
steghide extract -sf luv.jpeg
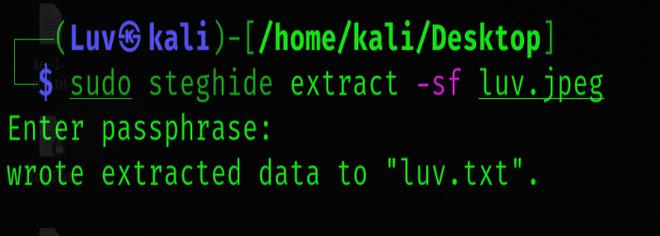
Then enter the passphrase(luv123) to extract the file. Here, sf is a secret file. The embedded text file will be extracted and written to your current directory.
Password Protect Files:
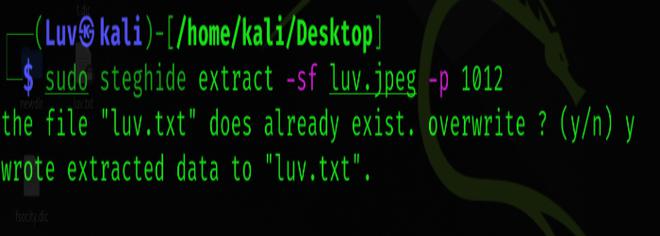
Now, we can also extract files using the following command. This command is different in that it specifies a password in the command itself, therefore, we do not need to specify it separately.
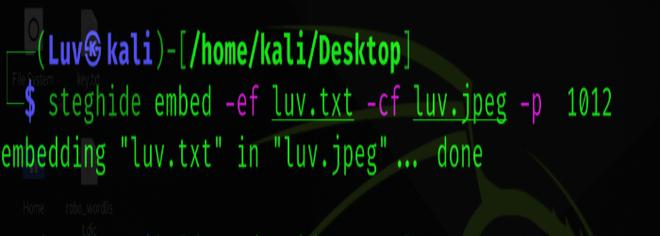
steghide embed -ef luv.txt -cf luv.jpeg -p 1012
sudo steghide extract -sf luv.jgeg -p 1012
Retrieve Information of Embedded File:
If we have an image in which the data is suspected to be hidden and if so, what algorithm is used to encrypt the data in the file? Then we will use the following command:
steghide info luv.jpeg
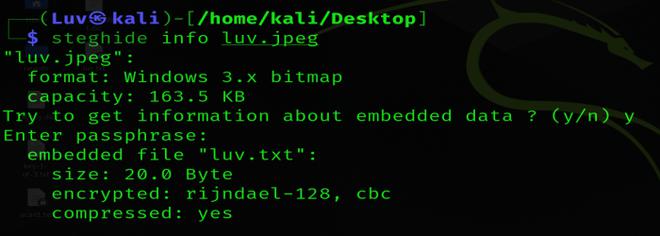
Verbose Mode
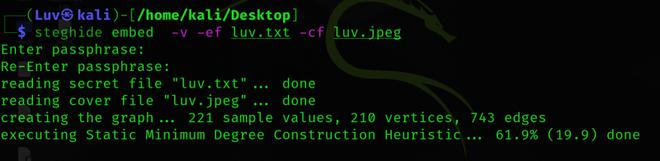
To obtain every information of a file during extraction, we can use verbose mode. The verbose mode gives you detailed information. We can use action mode by executing the following command:
steghide embed -v -ef luv.txt -cf luv.jpeg
Encrypting Algorithms:
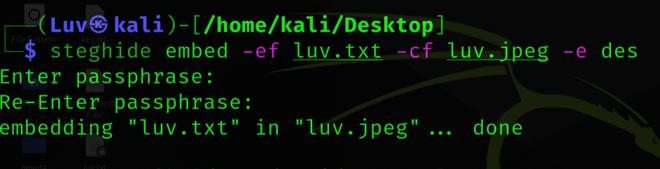
We can encrypt the data we are hiding using encryption techniques. And this can be easily achieved using the following command:
steghide embed -ef luv.txt -cf luv.jpeg -e <algorithm name>
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...