How to Create a Forensic Image with FTK Imager?
Last Updated :
05 Sep, 2022
A Forensic Image is most often needed to verify the integrity of the image after an acquisition of a Hard Drive has occurred. This is usually performed by law enforcement for court because, after a forensic image has been created, its integrity can be checked to verify that it has not been tampered with. Forensic Imaging is defined as the processes and tools used in copying an electronic media such as a hard-disk drive for conducting investigations and gathering evidence that will be presentable in the law of court. This copy not only includes files that are visible to the operating system but every bit of data, every sector, partition, files, folders, master boot records, deleted files, and unallocated spaces. The image is an identical copy of all the drive structures and contents.
Further, a forensic image can be backed up and/or tested on without damaging the original copy or evidence.
Also, you can create a forensic image from a running or dead machine. It is a literal snapshot in time that has integrity checking.
Need for a Forensic Image
- In today’s world of crime, many cases have been solved by using this technique, as evidence apart from what is available through an operating system, has been found using this technique, as incriminating data might have deleted to prevent discovery during the investigation. Unless that data is overwritten and deleted securely, it can be recovered.
- One of the advantages includes the prevention of the loss of critical files.
- When you suspect a custodian of deleting or altering files. A complete forensic image will, to a certain extent, allow you to recover deleted files. It can also potentially be used to identify files that have been renamed or hidden.
- When you expect that the scope of your investigation could increase at a later date. If you aren’t sure about the scope of your project, ALWAYS OVER COLLECT. It’s better to have too much data than not enough, and you can’t get much more data than a forensic image.
- When you expect that you or someone in your organization may need to certify or testify to the forensic soundness of the collection. In most cases, this need will never arise, but will almost certainly come into play in any criminal or potential criminal proceedings.
- The Imaging of random access memory (RAM) can be enabled by using Live imaging. Live imaging can bypass most encryption.
What Is FTK Imager?
FTK Imager is a tool for creating disk images and is absolutely free to use. It was developed by The Access Data Group. It is a tool that helps to preview data and for imaging.
With FTK Imager, you can:
- Create forensic images or perfect copies of local hard drives, floppy and Zip disks, DVDs, folders, individual files, etc. without making changes to the original evidence.
- Preview files and folders on local hard drives, network drives, floppy diskettes, Zip disks, CDs, and DVDs.
- You can also preview the contents of the forensic images that might be stored on a local machine or drive.
- You can also mount an image for a read-only view that will also allow you to view the contents of the forensic image exactly as the user saw it on the original drive.
- Export files and folders from forensic images.
- View and recover files that have been deleted from the Recycle Bin, but have not yet been overwritten on the drive.
There are many ways to create a forensic image. However, one of which is explained below.
Approach:
To create a forensic image with FTK imager, we will need the following:
- FTK Imager from Access Data, which can be downloaded using the following link: FTK Imager from Access Data
- A Hard Drive that you would like to create an image of.
Method :
Step 1: Download and install the FTK imager on your machine.
Step 2: Click and open the FTK Imager, once it is installed. You should be greeted with the FTK Imager dashboard.
Step 3: In the menu navigation bar, you need to click on the File tab which will give you a drop-down, like given in the image below, just click on the first one that says, Add Evidence Item.

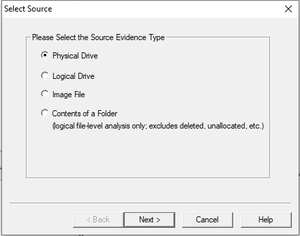
Step 4: After that, there will be a pop-up window that will ask you to Select the Source of the Evidence. If you have connected a physical hard drive to the laptop/computer you are using to make the forensic image, then you will select the Physical Drive here. Click on Next. Now, Select the Physical Drive that you would like to use. Please make sure that you are selecting the right drive, or you will waste your time exporting a forensic image of your own OS drive.
Step 5: Now, we will export the forensic images.
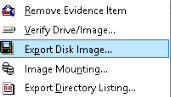
- Right-click on the Physical Drive that you would like to export in the FTK Imager window. Select Export Disk Image here.
- Click the Add button for the Image Destination.
- Select the Type of Forensic Image you would like to export. Select .E01 and Click Next.
- After that, you will have to enter information regarding the case now. You can either leave them blank or keep it general, this part is totally upon you.
- Next, you will need to Choose the Destination that you would like to export the forensic image and Name the Image.
Lastly, you will need to wait for the Forensic Image to be created and then verified. The speed of creating the forensic image will vary based on your hardware. Once both have occurred, you have your forensic images ready.
Pros Of FTK Imager
- It has a simple user interface and advanced searching capabilities.
- FTK supports EFS decryption.
- It produces a case log file.
- It has significant bookmarking and salient reporting features.
- FTK Imager is free.
Cons Of FTK Imager
- FTK does not support scripting features.
- It does not have multitasking capabilities.
- There is no progress bar to estimate the time remaining.
- FTK does not have a timeline view.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...