Hash Functions in System Security
Last Updated :
21 Mar, 2023
Hash Function is a function that has a huge role in making a System Secure as it converts normal data given to it as an irregular value of fixed length. We can imagine it to be a Shaker in our homes.
When we put data into this function it outputs an irregular value. The Irregular value it outputs is known as “Hash Value”.Hash Values are simply numbers but are often written in Hexadecimal. Computers manage values as Binary. The hash value is also data and is often managed in Binary.

A hash function is basically performing some calculations in the computer. Data values that are its output are of fixed length. Length always varies according to the hash function. Value doesn’t vary even if there is a large or small value.
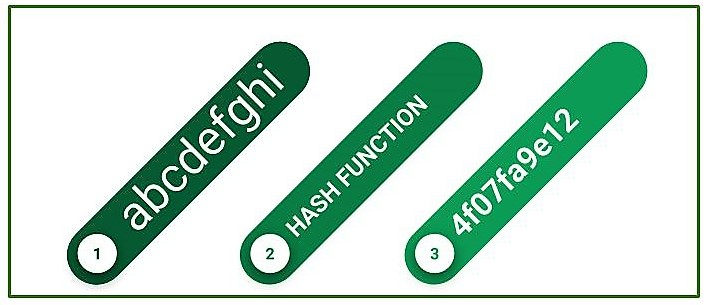
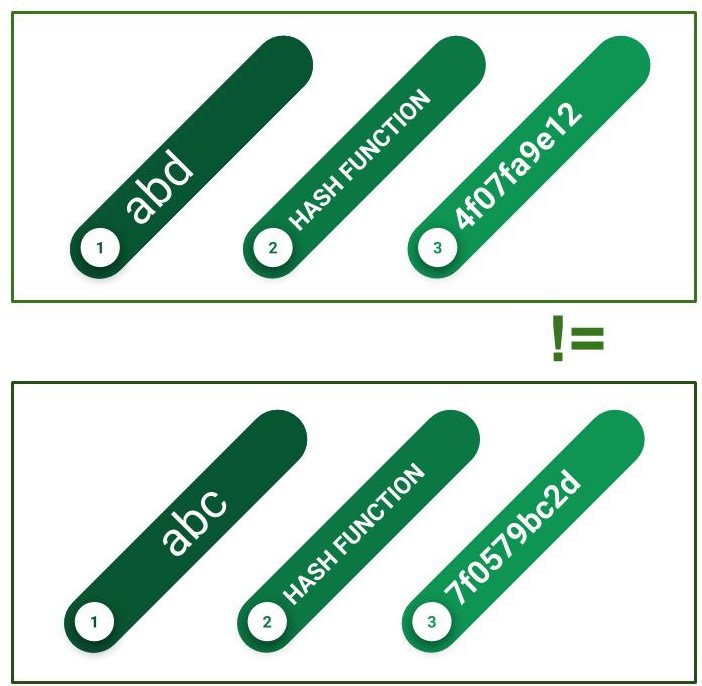
If given the same input, two hash functions will invariably produce the same output. Even if input data entered differs by a single bit, huge change in their output values. Even if input data entered differs huge, there is a very minimal chance that the hash values produced will be identical. If they are equal it is known as “Hash Collision”.
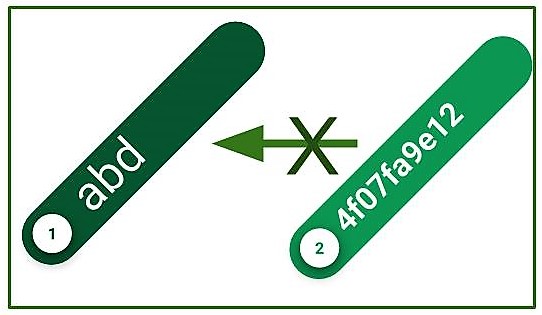
Converting Hash Codes to their original value is an impossible task to perform. This is the main difference between Encryption as Hash Function.
Features of hash functions in system security:
One-way function: Hash functions are designed to be one-way functions, meaning that it is easy to compute the hash value for a given input, but difficult to compute the input for a given hash value. This property makes hash functions useful for verifying the integrity of data, as any changes to the data will result in a different hash value.
Deterministic: Hash functions are deterministic, meaning that given the same input, the output will always be the same. This makes hash functions useful for verifying the authenticity of data, as any changes to the data will result in a different hash value.
Fixed-size output: Hash functions produce a fixed-size output, regardless of the size of the input. This property makes hash functions useful for storing and transmitting data, as the hash value can be stored or transmitted more efficiently than the original data.
Collision resistance: Hash functions should be designed to be collision resistant, meaning that it is difficult to find two different inputs that produce the same hash value. This property ensures that attackers cannot create a false message that has the same hash value as a legitimate message.
Non-reversible: Hash functions are non-reversible, meaning that it is difficult or impossible to reverse the process of generating a hash value to recover the original input. This property makes hash functions useful for storing passwords or other sensitive information, as the original input cannot be recovered from the hash value.
Advantages:
Data integrity: Hash functions are useful for ensuring the integrity of data, as any changes to the data will result in a different hash value. This property makes hash functions a valuable tool for detecting data tampering or corruption.
Message authentication: Hash functions are useful for verifying the authenticity of messages, as any changes to the message will result in a different hash value. This property makes hash functions a valuable tool for verifying the source of a message and detecting message tampering.
Password storage: Hash functions are useful for storing passwords in a secure manner. Hashing the password ensures that the original password cannot be recovered from the hash value, making it more difficult for attackers to access user accounts.
Fast computation: Hash functions are designed to be fast to compute, making them useful for a variety of applications where efficiency is important.
Disadvantages:
Collision attacks: Hash functions are vulnerable to collision attacks, where an attacker tries to find two different inputs that produce the same hash value. This can compromise the security of hash-based protocols, such as digital signatures or message authentication codes.
Rainbow table attacks: Hash functions are vulnerable to rainbow table attacks, where an attacker precomputes a table of hash values and their corresponding inputs, making it easier to crack password hashes.
Hash function weaknesses: Some hash functions have known weaknesses, such as the MD5 hash function, which is vulnerable to collision attacks. It is important to choose a hash function that is secure for the intended application.
Limited input size: Hash functions produce a fixed-size output, regardless of the size of the input. This can lead to collisions if the input size is larger than the hash function output size.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...