Functionality of Computer Network
Last Updated :
05 Jun, 2023
Prerequisite – Basics of Computer Networking, Network goals, Layers of OSI Model, Transport Layer responsibilities When a client is present on one machine and server is present on another machine, then making a connection between them, is called computer network.Computer networks share common devices, functions, and the features of computer network like clients, server, transmission media, shared data, shared printers and other hardware and software resources, Network Interface Card (NIC), Local Operating System (LOS), and the network operating system.
Functionality of Computer Network:
Computer network has two type of functionality:
- Mandatory function
- Optional function
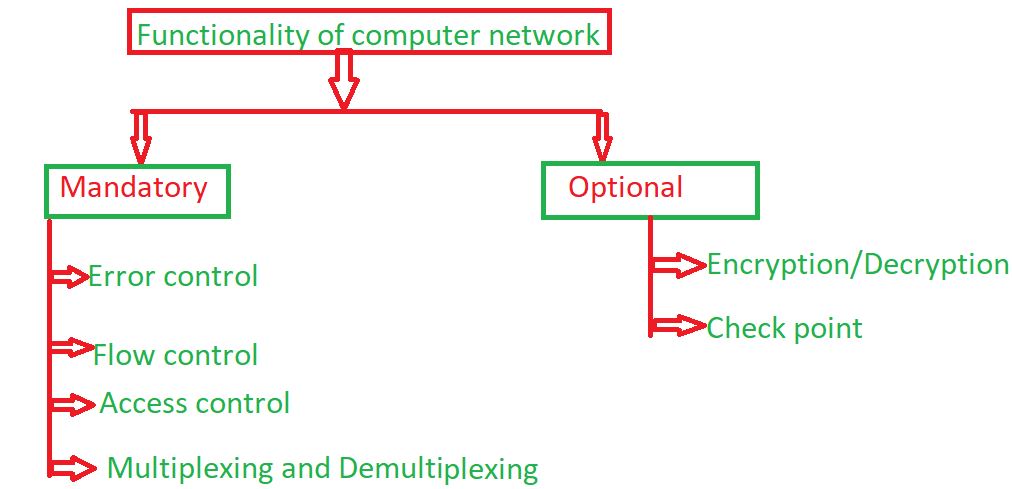
1. Mandatory function: Some function is mandatory in computer network and when mandatory function include in computer network, then perform operation in computer network.Some mandatory functions are given below:
- Error control: The computer network has some responsibility like transmission of data from one device to another device and end to end transfer of data from a transmitting application to a receiving application involves many steps, each subject to error. By using the error control process, we can be confident that the transmitted and received data are identical. Data can be corrupted during transmission. The error must be detected and corrected for reliable communication. Types of error-
- (a). Single bit error: The terms single bit error means that only one bit of the data unit was changed from 1 to 0 and 0 to 1.
- (b). Burst Error: The term burst error means that two or more bits in the data unit were changed. A burst error is also called packet-level error, where errors like packet loss, duplication, reordering.
- Flow control: When a packet (Layer-2 data) is sent from one host to another over a single medium, it is required that the sender and receiver should work at the same speed. That is, the sender sends at a speed on which the receiver can process and accept the data. If the sender is sending too fast the receiver may be overloaded, (swamped) and data may be lost.
- Access control: Network access control is a method of enhancing the security of a private organizational network by restricting the availability of network resources to endpoint devices that comply with the organization’s security policy. The network access control scheme comprises of two major components such as Restricted Access and Network Boundary Protection.
- Multiplexing and Demultiplexing: A multiplexing is a technique by which different analog and digital streams of transmission can be simultaneously processed over a shared link. Multiplexing divides the high capacity medium into low capacity logical medium which is then shared by different streams.
2. Optional function: Some function is optional in computer network and optional function do not need always in computer network.Some optional functions are given below:
- Encryption and decryption: Decryption and Encryption is a security method in which information is encoded in such a way that only authorized user can read it. Some network uses encryption algorithm to generate ciphertext that can only be read if decrypted. Types of encryption-
- (a). Symmetric Key encryption
- (b). Public Key encryption
- Check Points: Let us say you are downloading a file of 500mb and suppose a failure occur and after some time if you re-start that download then it should resume from where failure happend. This is known as check-point creation. You can create multiple check points, after failure it will start from its predecessor check-point. Check-points are optional functionality of computer network. It is not mandatory to follow by all networks. It is usefull in downloading and uploading large files.
There are more than 70 functionalities. All these functionalities divided into seven layers of OSI Model. These are the functionalities which are the background concept of OSI Model.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...