FeroxBuster – Recursive Content Discovery Tool in Kali Linux
Last Updated :
14 Sep, 2021
Feroxbuster is a tool designed to perform Compelled Browsing. Compelled browsing is an attack where the aim is to identify and access resources that are not referenced by the web application but are still obtainable by an attacker. Feroxbuster tool uses brute force strategy combined with a word-list to search for unlinked content in target directories. These resources may store delicate information about web applications and operational systems, such as source code, credentials, internal network address, etc. Feroxbuster tool is open-source and free to use. It’s available on GitHub and also added in the apt manager of the Linux OS recently. This attack is also known as Predictable Resource Location, File Enumeration, Directory Enumeration, and Resource Enumeration.
Installation of FeroxBuster Tool on Kali Linux OS
Step 1: Update the System by using the following command.
sudo apt-get update
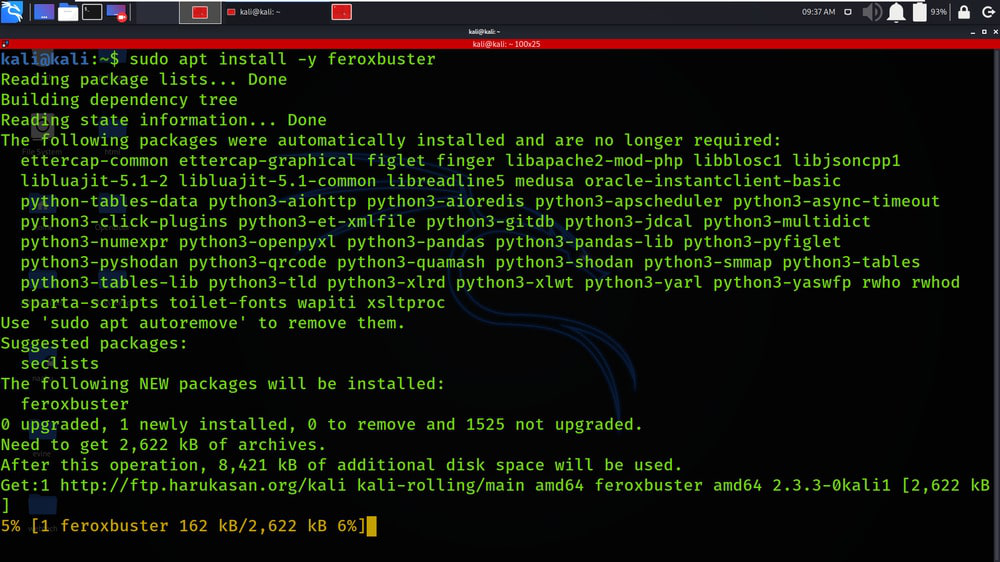
Step 2: Now use the following command to install the FeroxBuster tool from the apt manager.
sudo apt install -y feroxbuster
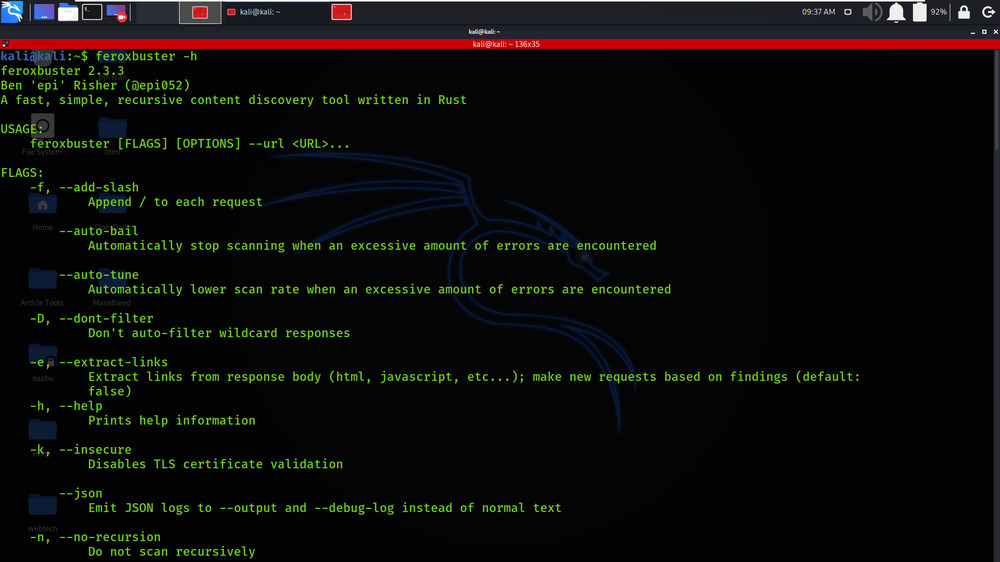
Step 3: Now our tool is successfully installed. Check the help page by using the following command.
feroxbuster -h
Working with FeroxBuster Tool on Kali Linux OS
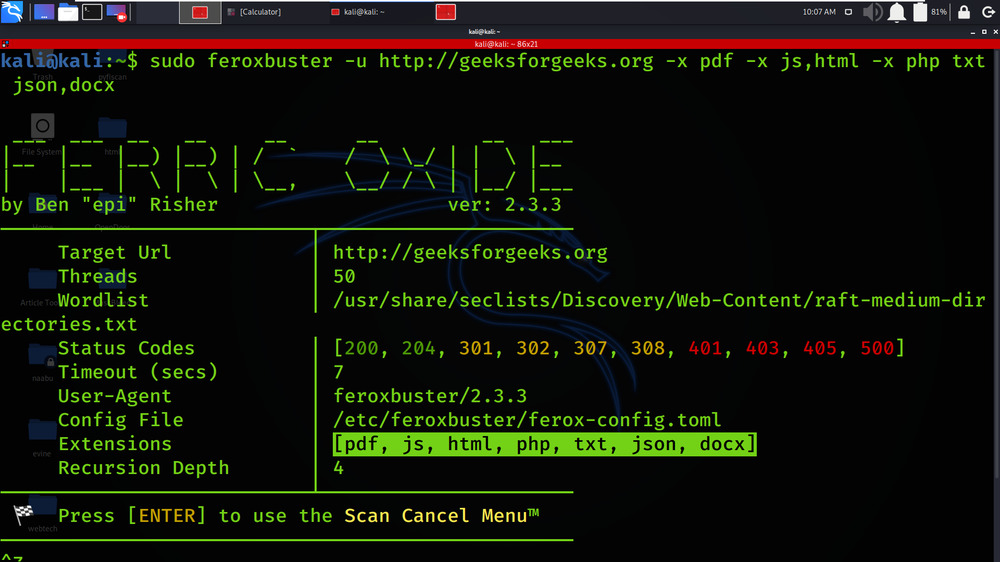
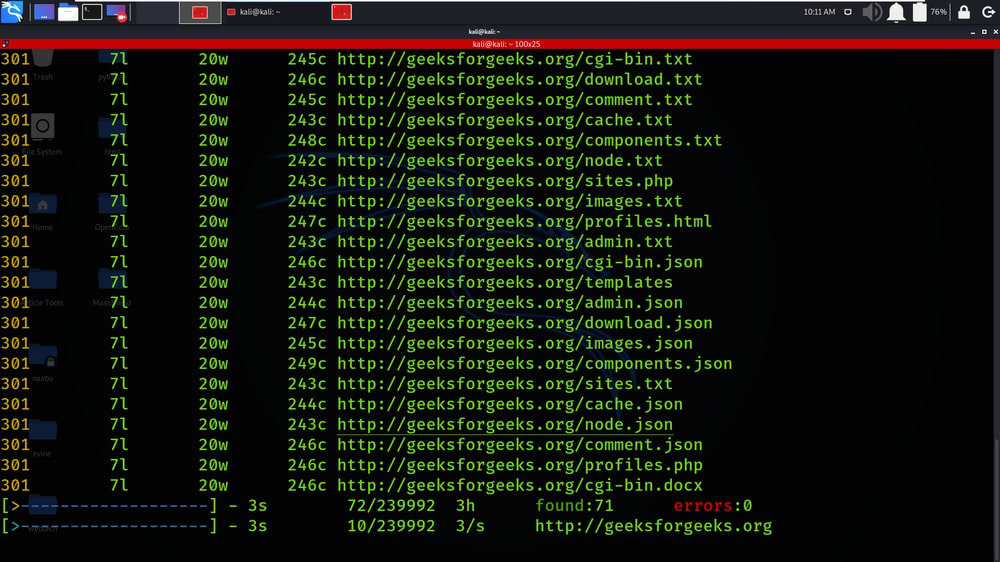
Example 1: Multiple Values
sudo feroxbuster -u http://geeksforgeeks.org -x pdf -x js,html -x php txt json,docx
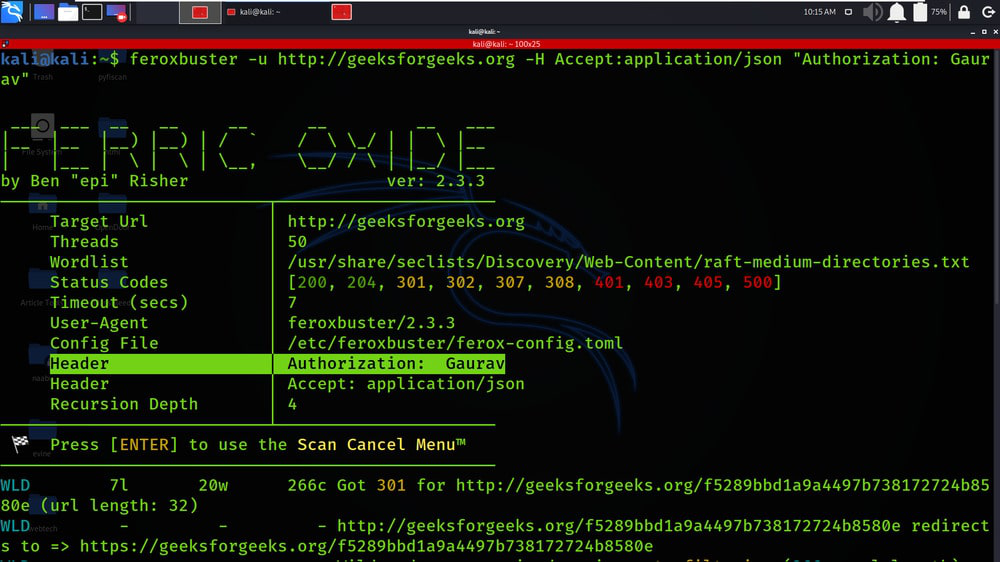
Example 2: Include Headers
feroxbuster -u http://geeksforgeeks.org -H Accept:application/json “Authorization: Gaurav”
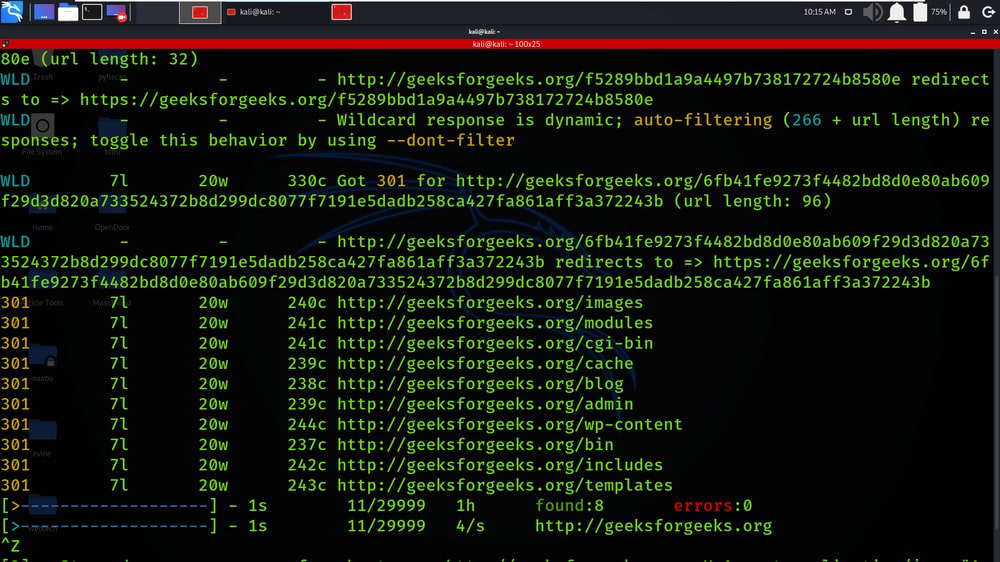
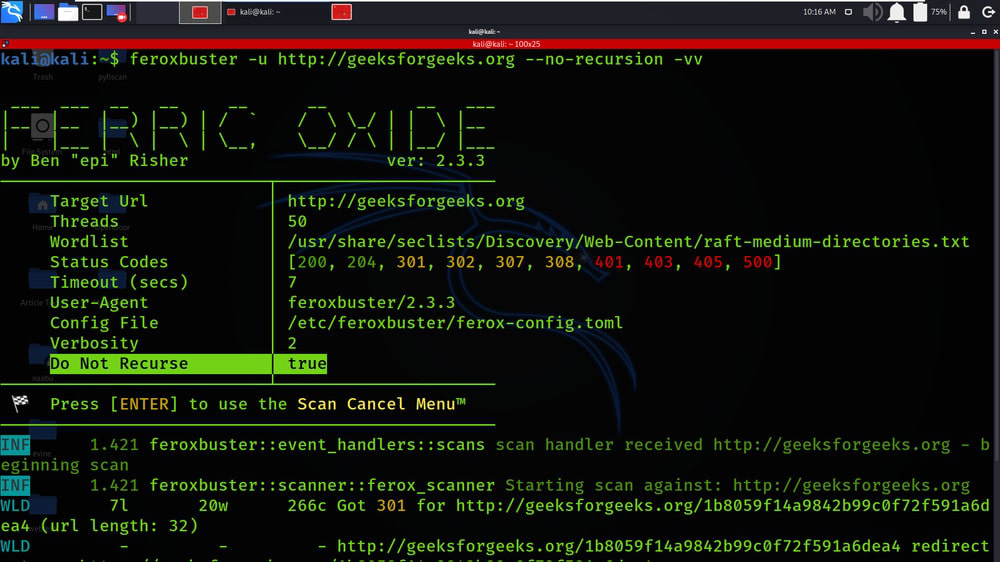
Example 3: IPv6, non-recursive scan with INFO-level logging enabled
feroxbuster -u http://geeksforgeeks.org –no-recursion -vv
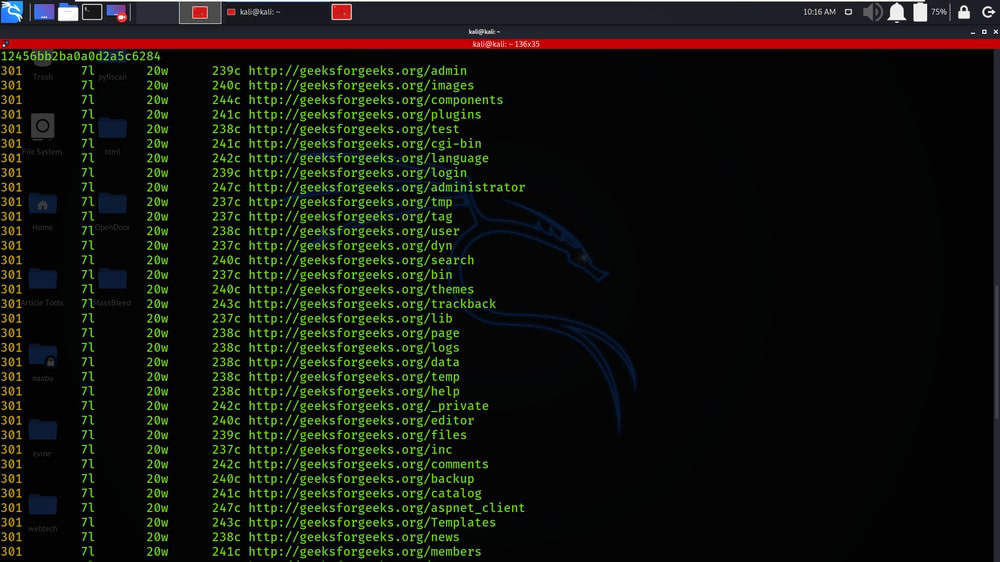
Example 4: Read URLs from STDIN; pipe only resulting URLs out to another tool
cat targets.txt | feroxbuster –stdin –silent -s 200 301 302 –redirects -x js fff -s 200 -o js-files
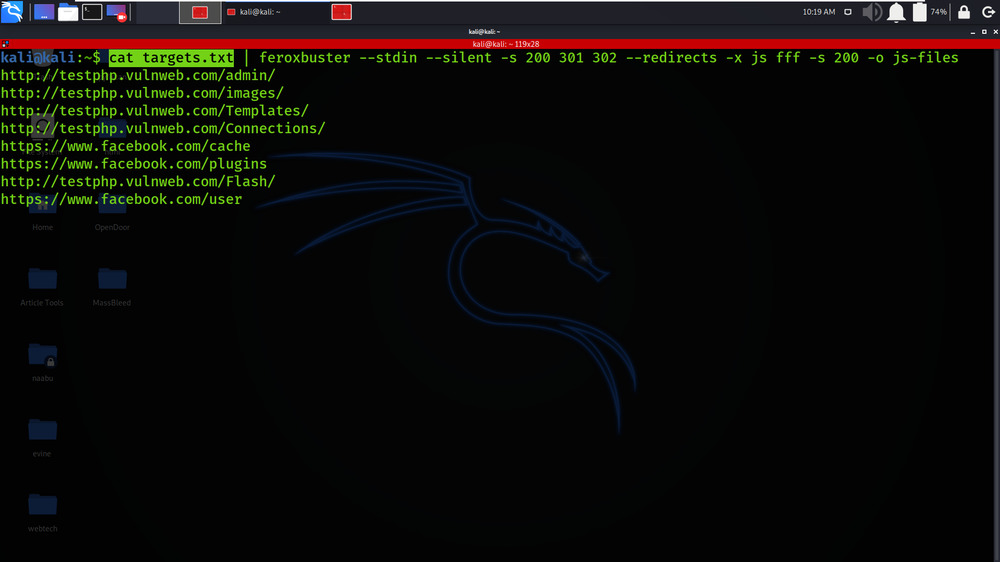
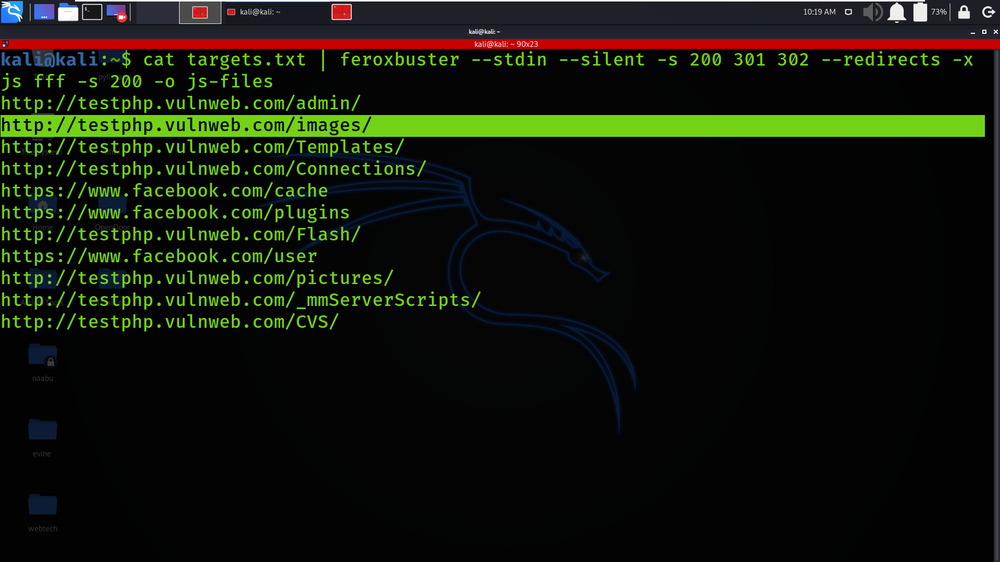
Example 5: Proxy traffic through Burp
feroxbuster -u http://geeksforgeeks.org –insecure –proxy http://127.0.0.1:80
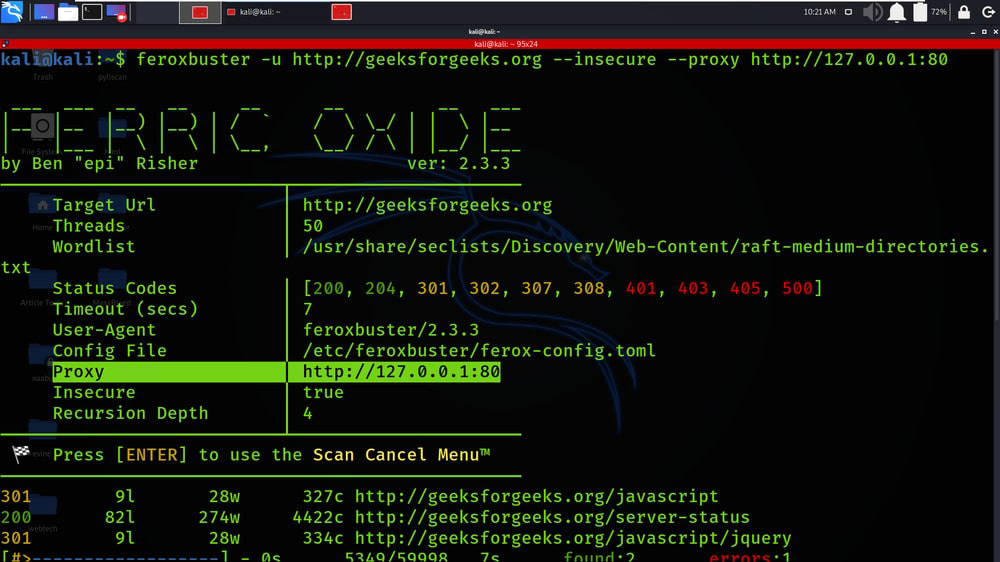
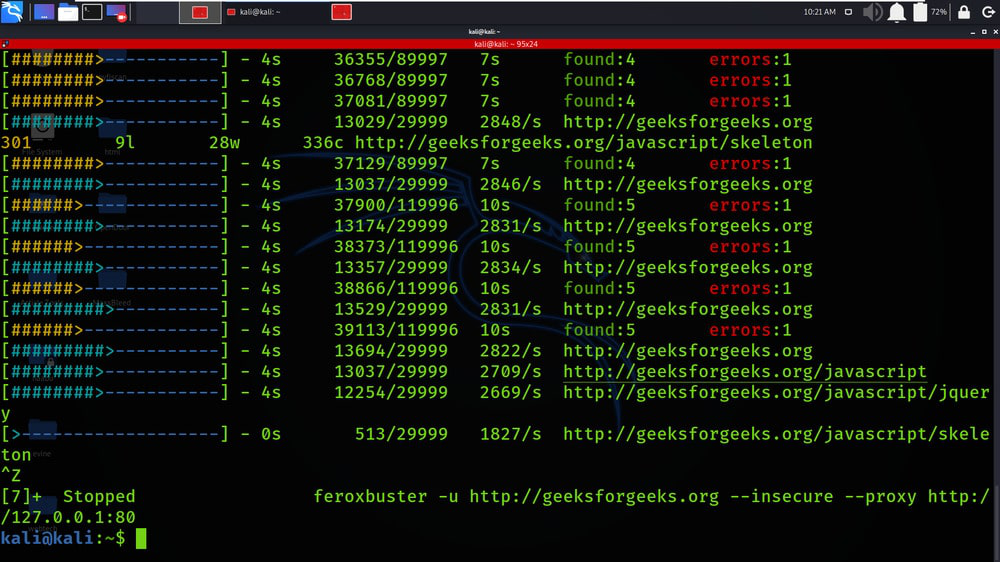
Example 6: Proxy traffic through a SOCKS proxy (including DNS lookups)
feroxbuster -u http://geeksforgeeks.org –proxy socks5h://127.0.0.1:80
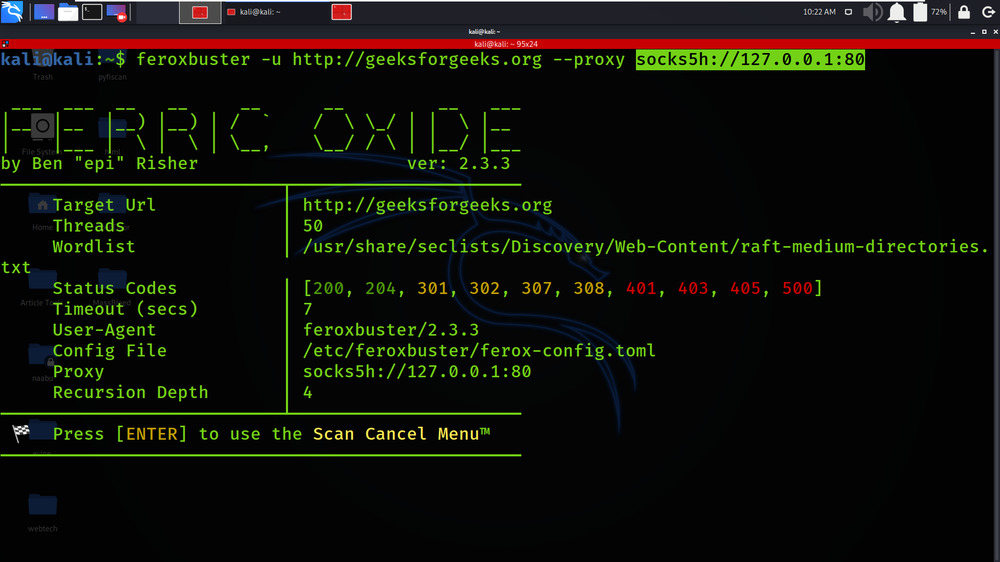
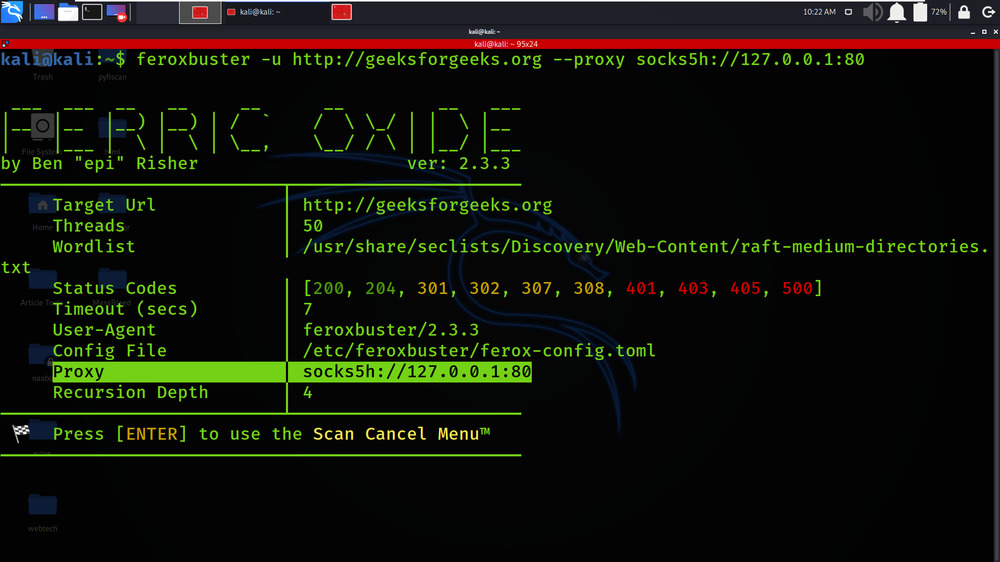
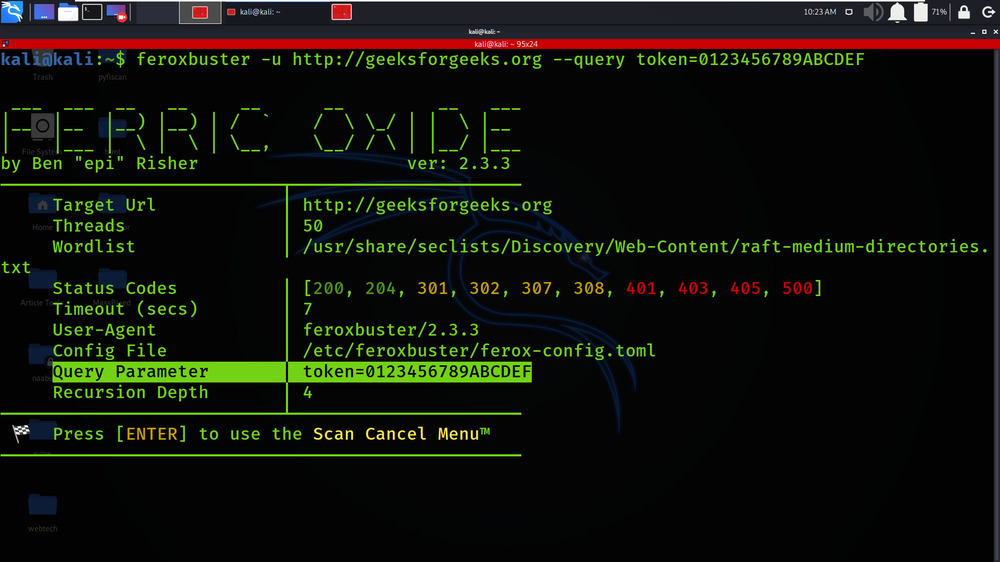
Example 7: Pass auth token via a query parameter
feroxbuster -u http://geeksforgeeks.org –query token=0123456789ABCDEF
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...