Elements of Cybersecurity
Last Updated :
16 Jun, 2022
Cyber security is the shielding of web associated systems, for example, hardware, software, and information from cyber dangers. The training is utilized by people and ventures to defend against unapproved access to the servers and other electronic systems.
Various elements of cyber security are given below:
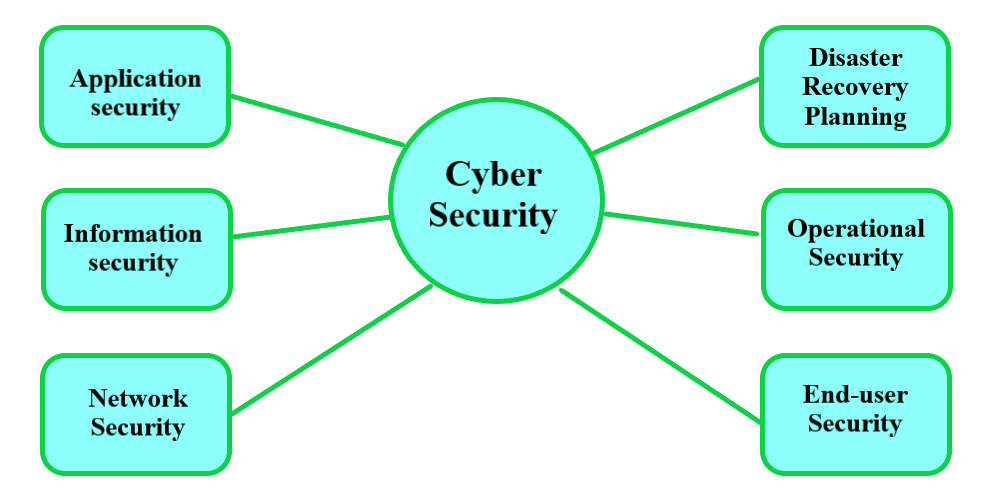
Let’s see an explanation of the elements in detail:
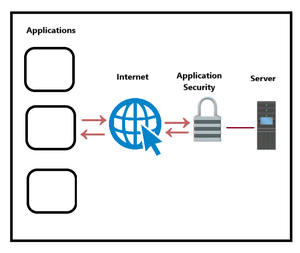
1. Application Security: Application security is the principal key component of cyber security which adds security highlights inside applications during the improvement time frame to defend against cyberattacks. It shields sites and online applications from various sorts of cyber security dangers which exploit weaknesses in source code. Application security is tied in with keeping software applications away from dangers. The general focus of application security is on cloud service-based organizations.
Due to misconfiguration of settings the data of the cloud gets insecure. The fundamental reason for cloud application misconfiguration are:
- Absence of attention to cloud security approaches
- Absence of sufficient controls and oversight
- Utilization of such a large number of connection points to oversee.
Vulnerabilities of Application: Denial-of-service (DoS) and Distributed denial-of-service(DDoS) attacks are used by some isolated attackers to flood a designated server or the framework that upholds it with different sorts of traffic. This traffic in the end keeps real users from getting to the server, making it shut down. A strategy called SQL injection (SQLi) is used by hackers to take advantage of database flaws. These hackers, specifically, can uncover user personalities and passwords and can also create, modify and delete data without taking permission of the user.
Types of Application Security: The types of Application Security are Authentication, Authorization, Encryption, Logging, and Application security testing.
Tools of Application Security: The various tools of application security are firewall, antivirus, encryption techniques, web application firewalls that protect applications from threats.
2. Information Security: Information Security is the component of cyber security that denotes the methods for defending unapproved access, use, revelation, interruption, modification, or deletion of information. The protection of the companies data, code, and information that is collected by the company from their clients and users is protected by Information security. The primary standards and principles of Information security are Confidentiality, Integrity, and Availability. Together it is called as CIA.
- Confidentiality: The protection of information of authorized clients which allows them to access sensitive information is known as Confidentiality. For example, assuming we say X has a password for my Facebook account yet somebody saw while X was doing a login into the Facebook account. All things considered, my password has been compromised and Confidentiality has been penetrated.
- Integrity: The maintaining of consistency, accuracy, and completeness of the information is known as Integrity. Information cannot be modified in an unapproved way. For example, in an information break that compromises the integrity, a programmer might hold onto information and adjust it prior to sending it on to the planned beneficiary. Some security controls intended to keep up with the integrity of information include Encryption, Controls of Client access, Records Control, Reinforcement, recovery methodology, and Detecting the error.
- Availability: The information which can be accessed any time whenever authorized users want. There are primarily two dangers to the accessibility of the system which are as per the following:
- Denial of Service
- Loss of Data Processing Capabilities
3. Network Security: Network security is the security given to a network from unapproved access and dangers. It is the obligation of network heads to embrace preventive measures to safeguard their networks from potential security dangers. Network security is one more element of IT security which is a method of defending and preventing unapproved access into computer networks.
- Network Security Strategies: There are numerous strategies to further develop network security and the most well-known network security parts are as per following: Firewalls, Antivirus, Email Security, Web Security, Wireless Security.
- Network Security Software: There are different types of tools that can shield a computer network like Network firewall, Cloud application firewall, Web application firewall, etc.
4. Disaster Recovery Planning/Business Continuity Planning: The planning that describes the continuity of work in a fast and efficient way after a disaster is known as Disaster Recovery Planning or Business Continuity Planning. A disaster recovery technique should begin at the business level and figure out which applications are generally vital to run the activities of the association. Business continuity planning (BCP) is tied in with being ready for cyber danger by distinguishing dangers to the association on schedule and examining how activities might be impacted and how to conquer that.
The primary objectives of disaster recovery planning include:
- Protect the organization during a disaster
- Giving a conviction of security
- Limiting the risk of postponements
- Ensuring the dependability of backup systems
- Giving a standard to testing the plan.
- Limiting decision-production during a disaster
- Disaster Recovery Planning Categories: The categories of Disaster Recover Planning are
- Data Center disaster recovery
- Cloud applications disaster recovery
- Service-based disaster recovery
- Virtual disaster recovery
- Steps of Disaster Recovery Planning: The steps are:
- Acquire Top Management Commitment
- Planning panel establishment
- Performing risk management
- Establish priorities for handling and tasks
- Decide Recovery Strategies
- Data Collection
- Record a composed plan
- Build testing rules and methods
- Plan testing
- Support the plan
5. Operational Security: The process that encourages the managers to see the activities according to the viewpoint of a hacker to protect sensitive data from various threats is known as Operational Security (OPSEC)n or Procedural security. Operations security (OPSEC) is utilized to defend the functions of an association. It tracks basic data and resources to distinguish weaknesses that exist in the useful technique.
- Steps of Operational Security: There are five stages to deal with the operational security program, which are as per the following:
- Characterize the association’s delicate data
- Distinguish the types of dangers
- Investigate security openings and weaknesses
- Evaluation of Risks
- Execution of accurate countermeasures
- Practices of Operational Security: The best practices of Operational Securities are:
- Implement exact change management processes
- Limit access to network devices
- Minimum access to the employees
- Carry out double control
- Task automation
- Reaction and disaster recovery planning
6. End User Education: End-user training is most the significant element of computer security. End users are turning into the biggest security threat in any association since it can happen whenever. One of the primary errors that lead to information breaks is human mistakes. An association should prepare its workers about cybersecurity. Each representative should know about phishing attacks through messages and interfaces and can possibly manage cyber dangers.
Threats of End-User: There are many reasons, that danger can be made. The end-user dangers can be made in the following ways:
- Utilizing of Social Media
- Text Messaging
- Utilization of Email
- Applications Download
- Creation and irregular uses of passwords
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...