Edge Chasing Algorithms
Last Updated :
24 Jun, 2020
Deadlock might be a virtual disadvantage that may get up at some point of a community of cooperating or competitive procedures. A deadlock is that state of affairs where a group of methods are blocked as a result of every technique requiring a fixed process, sources needed for its headaches and anticipating release of ultimate assets held by using others in equal organization for that reason making it impossible for any of methods to proceed.
Deadlock involves following elements :
1. Resource :
Operating gadget and useful resource manager system can be concerned in deadlock scenarios.Finite numbers of assets are on market inside system.These resources are distributed among a selection of competitive methods.
- Reusable sources –
A reusable aid is one that can be correctly used by using handiest one method at a time and isn’t depleted by means of that use. Processes accumulate aid units that they later unharness for application through different tactics.
Examples of reusable sources are embody processors, I/O channels, I/O devices, number one and secondary memory, files, database, semaphores, etc.
- Expendable sources –
The expendable aid is one that can be created and destroyed. There’s no restriction on quantity of expendable assets of a particular kind. Samples of expendable sources are interrupts, indicators messages, and expertise in I/O buffers.A technique ought to request a resource before victimizing it and need to unleash useful resource once victimizing it. The quantity of assets requested won’t exceed complete wide variety of assets on market within gadget.
2. Request :
Request may be understood as when any processor asks for use of any resource. If request can’t be granted in real time, then requesting technique must wait till it will accumulate sources.
3. Use :
This state arises when resources are allotted to the processor.
4. Release :
After performing required operation ,resources are set to free state which may be concerned as release of resources.
Distributed Deadlock Detection Algorithms :
The algorithmic program will be initiated on every occasion when a way of deadlock is pressured to attend. The algorithmic program could be initiated either by using native web site of method or by using positioning anyplace method waits.Distributed situations will be detected through taking a shot of device and examining it for condition of an impasse.
Distributed deadlock detection algorithmic program can be divided into four classes as follows:
- Path push-in –
Path info- dispatched to waiting node to blocking off node.
- Edge-chasing –
Probe message area unit dispatched on graph edge.
- Diffusion computation –
Echo messages location unit dispatched on graph edges.
- Global nation detection –
Sweep-out, sweep-in WFG creation and reduction.
Edge Chasing Algorithm :
- Edge chasing algorithm makes use of a unique message on every occasion, impasse detection is initiated by procedure Pi and it’s miles being sent by means of house web site of manner Pi to house web site of procedure Pk.
- A probe message travels along rims ofworldwide TWF graph. An impasse is detected if a probe message returns to its initiating process.
Note –
A Boolean array, dependents, for each technique Pi , is maintained. If Pj is aware that Pi is depending on it, dependent (j) is ready to true. Otherwise, it’s far false.
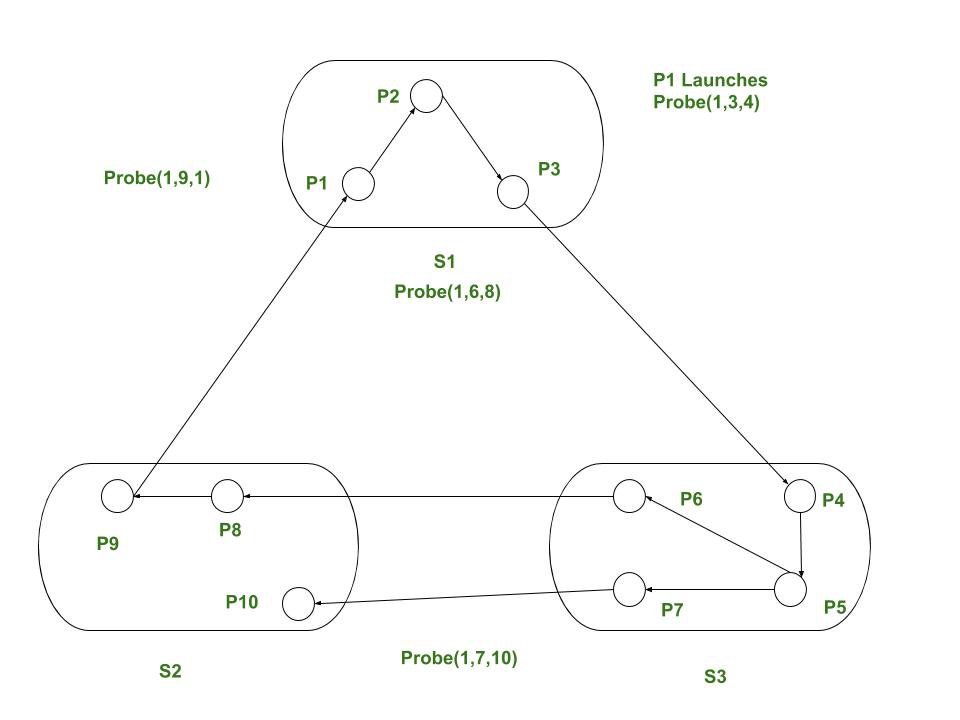
Example: Contemplate a system as given in Fig. If method P1 initiates situation detection , it sends probe (1, 3, 4) to S2. Since P6 is awaiting P8 and P7 is awaiting P10. S2 sends probe ( 1, 6, 8) and (1, 7, 10) to S3 that successively sends probe ( 1, 9, 1) to S1. On receiving probe (1, 9, 1), S1 declares that P1 is obstructed (deadlock).
If Pi is locally dependent on itself then declare deadlock
Else for all Pj and Pk such that
Pi is locally dependent upon Pj, and
Pj is waiting on Pk, and
Pj and Pk are on totally different sites
Send probe(i,j,k) to home site of Pk
On receipt of probe(i, j,k), positioning takes subsequent actions.
If
Pk is blocked, and
dependentk(i) is false. and
Pk has not replied to any or all requests of Pj
then
begin
dependentk(i)= true;
if k = i then declare that Pi is under deadlock
else for all Pm and Pn such that
Pk is locally dependent upon Pm, and
Pm is waiting on Pn and
Pm and Pn are on totally different sites,
send Prob(I,m,n) to house sites of Pn
end
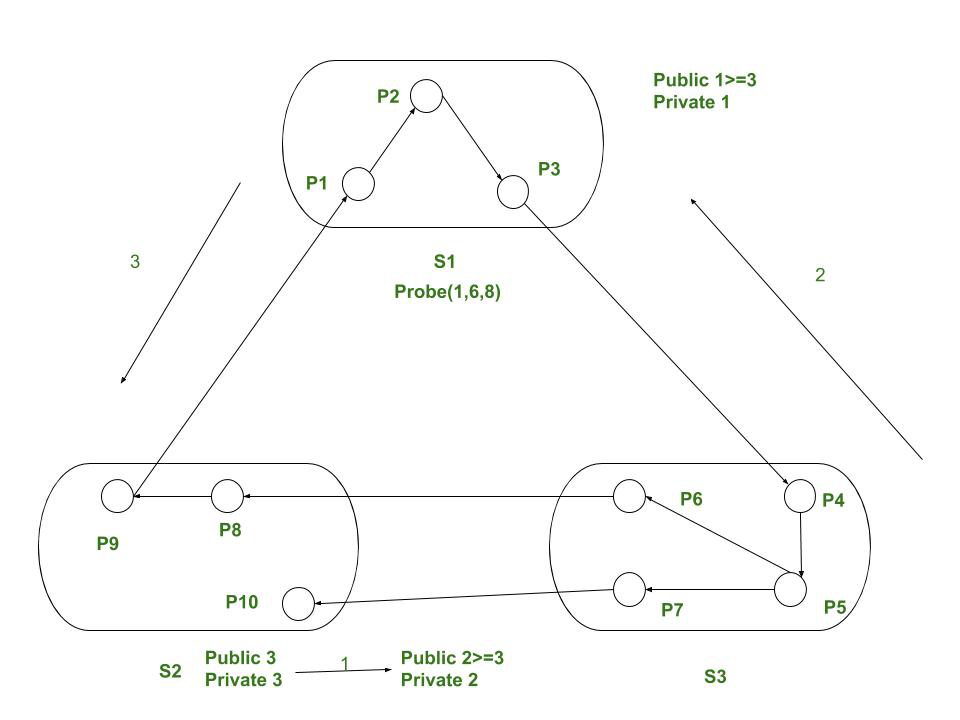
Solution of given example using Edge chasing algorithm :
- P6 at beginning asks P8 for its public label and changes it’s own 2 to 3.
- P3 asks P4 and changes its public label 1 to 3.
- P9 asks P1 and finds its own public label 3 then detects situation.
- P1 → P2 → P3 → P4 → P5 → P6 → P8 → P9 → P1.
Share your thoughts in the comments
Please Login to comment...