DNSTake – Check Missing Hosted DNS Zones
Last Updated :
23 Nov, 2022
DNS takeover security flaw triggers when a subdomain (write.geeksforgeeks.org) or main domain has its authoritative name-server set to their provider like AWS, Azure, etc. but the hosted zone is been permanently removed or misplaced. Although, while requesting this DNS record, the server responses to the user as SERVFAIL error due to the misplaced zones. Here, the attacker creates the zone in place of the misplaced zone and fetches all the DNS requests to the malicious zone.
Workflow
DNSTake tool uses the RetryableDNS client library to communicate and pass the DNS queries to the server. There is an initial engagement using the Google and Cloud-flare DNS as the resolver. Then the fingerprinting of the name-servers is performed. it there is a name-server present, then it will be resolved to the target host once again with the name-server IP as a resolver, if there is some odd response, then this can be the vulnerable point for the attacker. DNSTake tool is developed in the Golang language and is available on the GitHub platform, DNSTake tool is free and open-source to use.
Note: As DNSTake is a Golang language-based tool, so you need to have a Golang environment on your system. So check this link to download Golang in your system. – How to Install Go Programming Language in Linux
Installation of DNSTake Tool in Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/pwnesia/dnstake.git
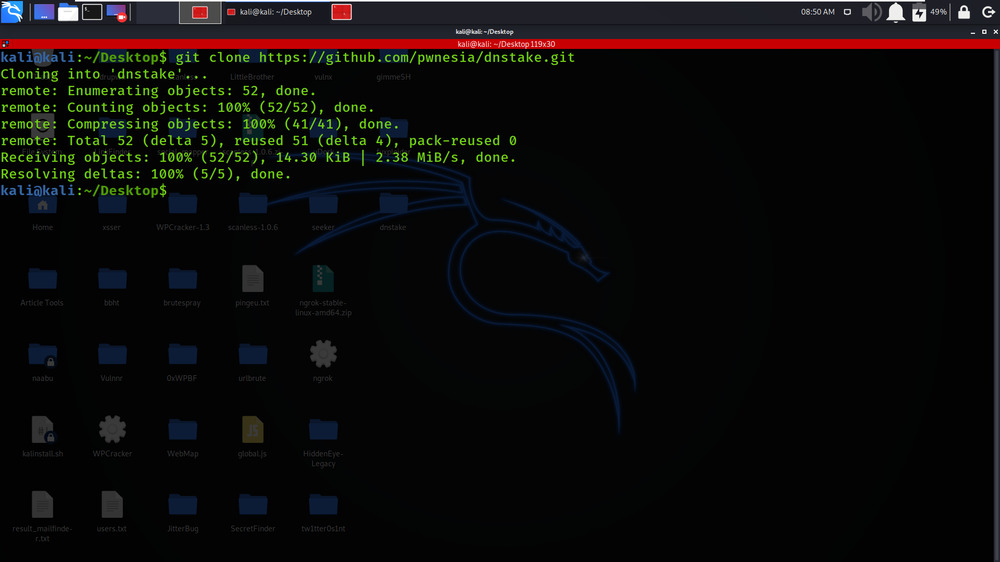
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd dnstake/cmd/dnstake
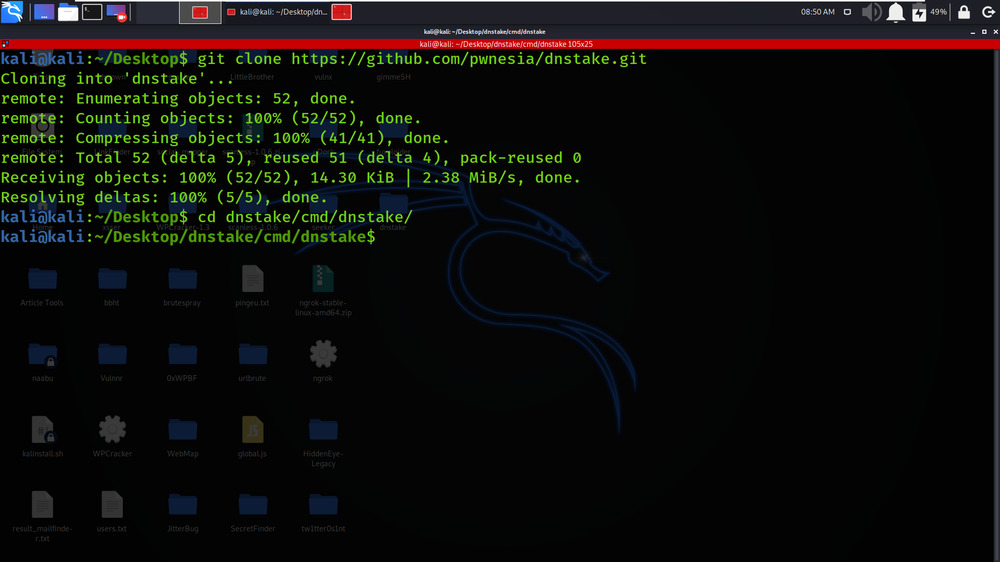
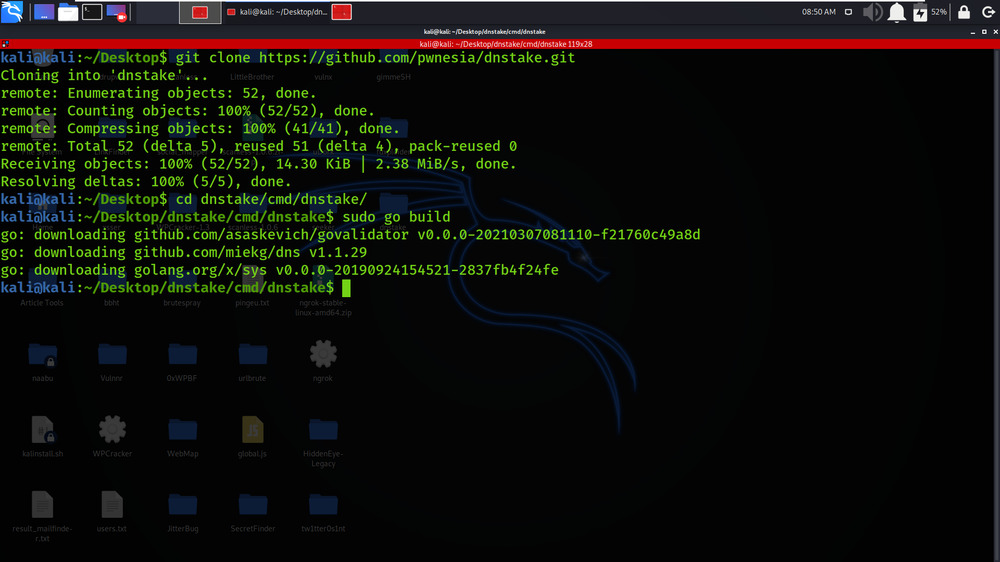
Step 3: Build the go file using the following command
sudo go build
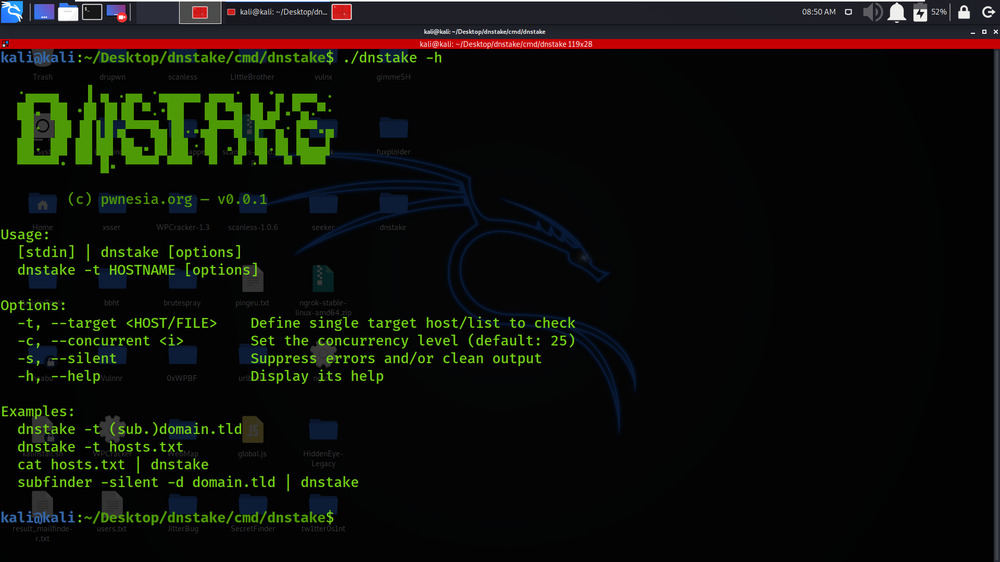
Step 4: Now use the following command to run the tool.
./dnstake -h
Working with DNSTake Tool in Kali Linux OS
Example: Simple Scan on Target Host-name
In this example, we are scanning the subdomains of geeksforgeeks.org.
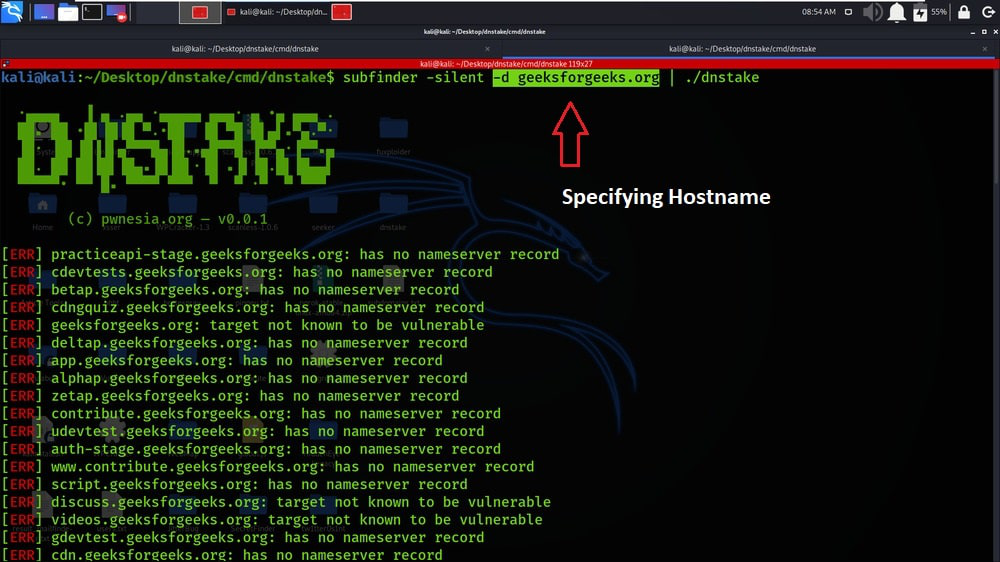
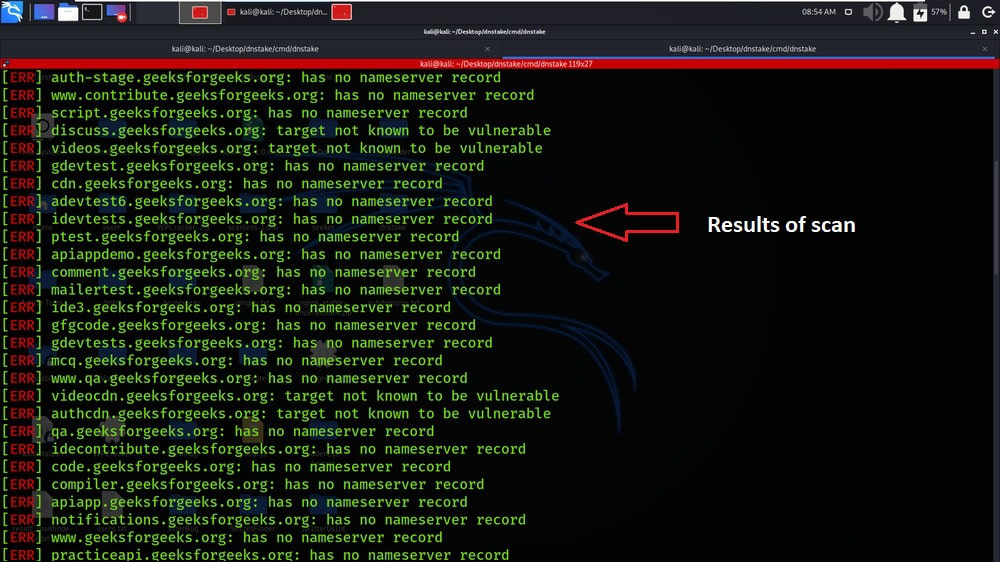
We have got the results of our scan.
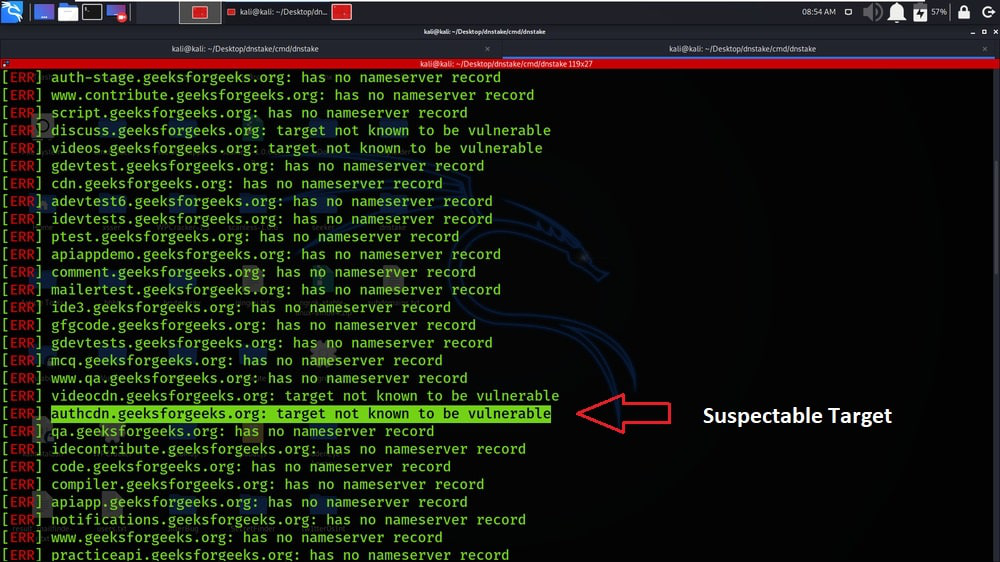
In the below screenshot, the highlighted subdomain maybe be vulnerable.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...