Difference between Phishing and Pharming
Last Updated :
22 Jul, 2022
Phishing:
Phishing is a type of attack on a computer device. In phishing, the attacker tries to find the sensitive information of users by the means of electronic communication illegally. In other words, it is an illegal attempt to obtain secure information from people or users.
A simple example of phishing is bank fraud, where hackers tried to get your bank details through communication by acting as an employee of the bank which is a fraud manner.
Pharming:
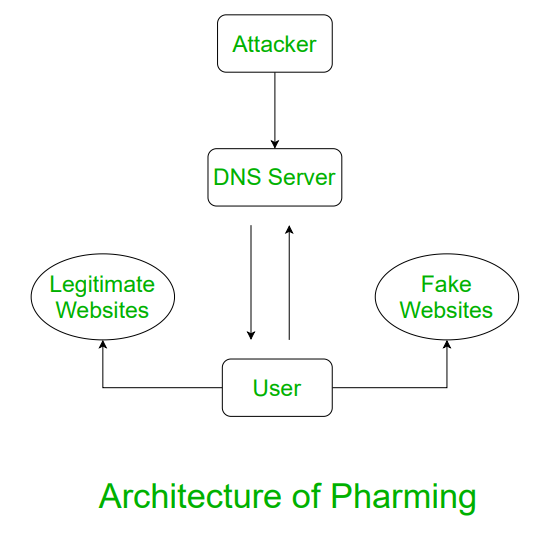
Pharming is a more advanced technique to get users’ credentials by making effort to enter users into the website. In order words, it misdirects users to a fake website that appears to be official and victims give their personal information at fault.
In pharming, a fake website is created which appears to be official. Users then access the website and a request is popped up regarding username and password and other credentials.
Let’s see the difference between Phishing and Pharming:
| S. No. |
PHISHING |
PHARMING |
| 1 |
In phishing, the attacker tries to find the sensitive information of users by the means of electronic communication illegally. |
Pharming is a more advanced technique to get users’ credentials by making effort to enter users into the website. |
| 2 |
It is an attempt to scam people one at a time via an email or instant message. |
It simply redirects traffic from one website to a different, identical-looking website to steal information. |
| 3 |
It is electronic mail fraud. |
It is similar in nature to email phishing. |
| 4 |
It is a type of fraud in which an attacker tricks the victims into providing personal information by email or message. |
It is a scam and seeks to obtain personal and private information through domain spoofing. |
| 5 |
It is relatively easy to initiate and identify. |
It is more difficult to accomplish and identify. |
| 6 |
It involves a fraudulent email containing a link to a website seeking personal details from users. |
It poisons the DNS server, redirecting the users to different websites. |
| 7 |
It uses mail. |
It uses websites. |
| 8 |
Phishing also uses additional methods for data theft like fax phishing, vishing, and smishing. |
Pharming will employ strategies for data theft such as DNS spoofing, DNS hijacking, and DNS cache poisoning. |
| 9. |
Phishing employs lures like bogus links. |
Pharming negotiates with the DNS server to send users to a fraudulent domain. Once the hacker conducts a successful DNS assault during pharming, the mainstream traffic to the website is diverted. |
| 10. |
It targets individuals one at a time. |
It simultaneously targets huge groups of individuals. |
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...