Distributed Denial of Service DDoS attack
Last Updated :
22 Apr, 2024
Imagine a scenario where you are visiting some websites and one of them seems to be a little slow. You might blame their servers for improving their scalability as they might be experiencing a lot of user traffic on their site. Most of the sites already take this issue into account beforehand. Chances are, they might be a victim of what is known as a DDoS attack, Distributed Denial of Service Attack.
In a DDoS attack, the attacker tries to make a particular service unavailable by directing continuous and huge traffic from multiple end systems. Due to this enormous traffic, the network resources get utilized in serving requests of those false end systems such that, a legitimate user is unable to access the resources for themselves.
How Does a DDoS Attack Work?
A denial-of-service (DDoS) attack is essentially an excessive use of a valid online service. For instance, a website might be able to process a specific amount of requests per minute. The website may become completely unusable if that number is surpassed, or its functionality may be negatively impacted. An attack or even a legitimate use, like an e-commerce site experiencing overflow on Black Friday or a ticket sales platform experiencing a glitch when sales for a big event begin, could be the cause of this overload.
A DDoS attack is launched from multiple compromised devices which are present in different places over the globe, this such devices are referred to as botnets. It differs from other denial of service (DoS) attacks in that it floods a target with malicious traffic using a single network connection or Internet-connected device.
Types of DDoS Attacks
DDoS attacks can be divided into three major categories:
- Application Layer Attacks: These attacks focus on attacking layer 7 of the OSI model where the webpages are generated in response to the request initiated by the end-user. For a client, generating a request does not take any heavy load and it can easily generate multiple requests to the server. On the other hand, responding to a request takes a considerable load for the server as it has to build all the pages, compute any queries, and load the results from the database according to the request. Examples: HTTP Flood attack and attack on DNS Services.
- Protocol Attacks: They are also known as state-exhaustion attacks. These attacks focus on vulnerabilities in layer 3 and layer 4 of the protocol stack. These types of attacks consume resources like servers, firewalls, and load balancers. Examples: SYN Flood attack and Ping of Death.
- Volumetric Attacks: Volumetric attacks focus on consuming the network bandwidth and saturating it by amplification or botnet to hinder its availability to the users. They are easy to generate by directing a massive amount of traffic to the target server. Examples: NTP Amplification, DNS Amplification, UDP Flood attack, and TCP Flood attack.
Common DDoS Attacks
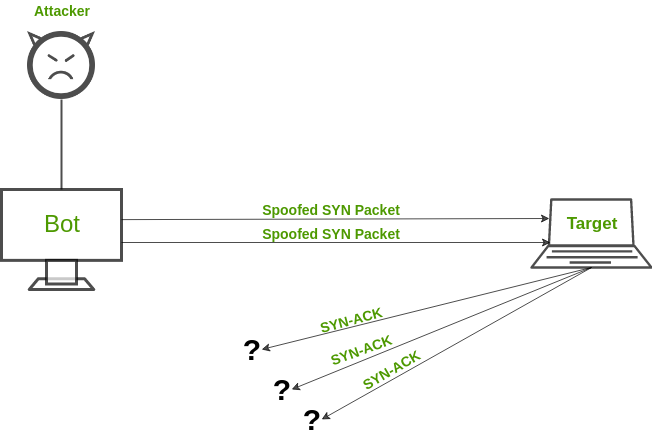
- SYN Flood Attack: An SYN Flood attack works similarly a mischievous child keeps on ringing the doorbell (request) and running away. The old person inside comes out, opens the door, and does not see anyone (no response). Ultimately, after frequent such scenarios, the old person gets exhausted and does not answer even genuine people. An SYN attack exploits TCP Handshake by sending out SYN messages with a spoofed IP address. The victim server keeps on responding but does not receive a final acknowledgment.
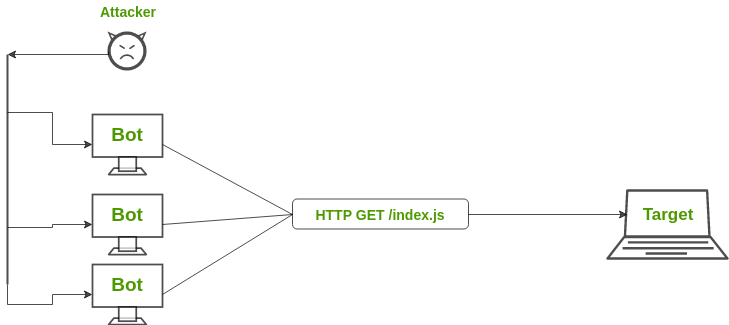
- HTTP Flood Attack: In an HTTP Flood attack, multiple HTTP requests are generated simultaneously against a target server. This leads to the exhaustion of network resources of that server and thus fails to serve actual users’ requests. The variations of HTTP Flood attacks are – HTTP GET attacks and HTTP POST attacks.
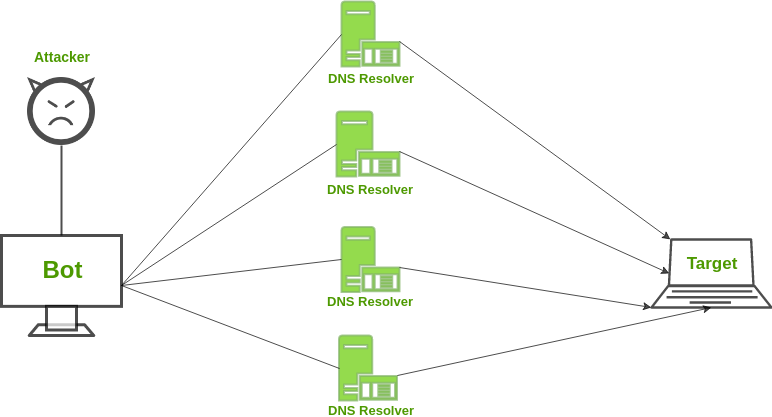
- DNS Amplification: Assume a scenario where you call Pizza Hut and ask them to call you back on a number and tell all the combinations of pizzas they have along with the toppings and desserts. You generated a large output with a very small input. But, the catch is the number you gave them is not yours. Similarly, DNS Amplification works by requesting a DNS server from a spoofed IP address and structuring your request so that the DNS server responds with a large amount of data to the target victim.
DDoS Mitigation
Preventing DDoS attacks is harder than DoS attacks because the traffic comes from multiple sources and it becomes difficult to separate malicious hosts from non-malicious hosts. Some of the mitigation techniques that can be used are:
- Blackhole Routing: In blackhole routing, the network traffic is directed to a ‘black hole’. In this, both the malicious traffic and non-malicious traffic get lost in the black hole. This countermeasure is useful when the server is experiencing a DDoS attack and all the traffic is diverted for the uptime of the network.
- Rate limiting: Rate limiting involves controlling the rate of traffic that is sent or received by a network interface. It is efficient in reducing the pace of web scrapers as well as brute-force login efforts. But, just rate limiting is unlikely to prevent compound DDoS attacks.
- Blacklisting/whitelisting Access: Blacklisting is the mechanism of blocking the IP addresses, URLs, domain names, etc. mentioned in the list and allowing traffic from all other sources. On the other hand, whitelisting refers to a mechanism of allowing all the IP addresses, URLs, domain names, etc. mentioned in the list and denying all other sources access to the resources of the network.
DDoS Threats
DDoS assaults are a severe risk to businesses of all kinds and sectors. The following are some possible effects of a successful attack:
- Financial Losses: A successful DDoS assault may result in lower productivity, downtime, and possible SLA violations, also in addition to requiring money to mitigate and recover.
- Operational Disruption: A DDoS assault has the potential to impair an organization’s capacity to carry out essential tasks or to make it harder for clients to use its services.
- Reputational Damage: If customers are unable to access an organization’s website or have doubts about its capacity to deliver goods and services, DDoS attacks may result in the loss of clients as they select competitors.
Frequently Asked Questions on DDos Attack- FAQs
How is DDoS detected?
DDoS attacks can be identified using two main methods: traffic flow record analysis for out-of-band detection and in-line packet inspection. Both strategies can be implemented using cloud services or on-premises.
Who is behind DDoS attacks?
DDoS attacks may also be motivated by political, hacktivist, terrorist, or commercial rivalry, among many other reasons. A DDoS attack can be launched against an organization by anyone with financial or ideological motivations.
How long can DDoS last?
A denial-of-service (DDoS) attack may last for several hours or even days. A week (or more) could pass between an attack and another that lasts only four hours. DDoS attacks can potentially involve multiple cyberattack types and occur once or frequently over time.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...