Conventional Encryption
Last Updated :
03 Sep, 2021
Conventional encryption is a cryptographic system that uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. It was the only type of encryption in use prior to the development of public-key encryption.
It is still much preferred of the two types of encryption systems due to its simplicity. It is a relatively fast process since it uses a single key for both encryption and decryption In this encryption model, the sender encrypts plaintext using the receiver’s secret key, which can be later used by the receiver to decrypt the ciphertext. Below is a figure that illustrates this concept.
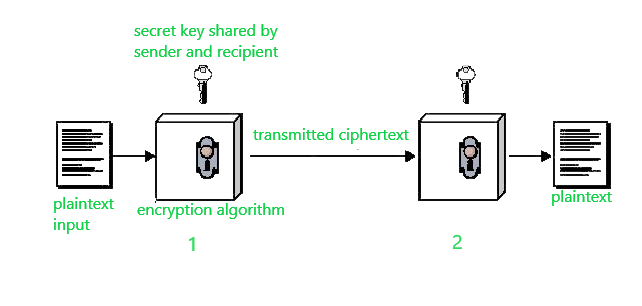
Suppose A wants to send a message to B, that message is called plaintext. Now, to avoid hackers reading plaintext, the plaintext is encrypted using an algorithm and a secret key (at 1). This encrypted plaintext is called ciphertext. Using the same secret key and encryption algorithm run in reverse(at 2), B can get plaintext of A, and thus the message is read and security is maintained.
The idea that uses in this technique is very old and that’s why this model is called conventional encryption.
Conventional encryption has mainly 5 ingredients :
- Plain text –
It is the original data that is given to the algorithm as an input.
- Encryption algorithm –
This encryption algorithm performs various transformations on plain text to convert it into ciphertext.
- Secret key –
The secret key is also an input to the algorithm. The encryption algorithm will produce different outputs based on the keys used at that time.
- Ciphertext –
It contains encrypted information because it contains a form of original plaintext that is unreadable by a human or computer without proper cipher to decrypt it. It is output from the algorithm.
- Decryption algorithm –
This is used to run encryption algorithms in reverse. Ciphertext and Secret key is input here and it produces plain text as output.
Requirements for secure use of conventional encryption :
- We need a strong encryption algorithm.
- The sender and Receiver must have obtained copies of the secret key in a secure fashion and must keep the key secure.
Advantages of Conventional Encryption :
- Simple –
This type of encryption is easy to carry out.
- Uses fewer computer resources –
Conventional encryption does not require a lot of computer resources when compared to public-key encryption.
- Fast –
Conventional encryption is much faster than asymmetric key encryption.
Disadvantages of Conventional Encryption Model:
- Origin and authenticity of the message cannot be guaranteed, since both sender and receiver use the same key, messages cannot be verified to have come from a particular user.
- It isn’t much secured when compared to public-key encryption.
- If the receiver lost the key, he/she cant decrypt the message and thus making the whole process useless.
- This scheme does not scale well to a large number of users because both the sender and the receiver have to agree on a secret key before transmission.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...