RC5 Encryption Algorithm
Last Updated :
21 Mar, 2023
RC5 is a symmetric key block encryption algorithm designed by Ron Rivest in 1994. It is notable for being simple, fast (on account of using only primitive computer operations like XOR, shift, etc.) and consumes less memory. Example:
Key : 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Plain Text : 00000000 00000000
Cipher Text : EEDBA521 6D8F4B15
RC5 is a block cipher and addresses two word blocks at a time. Depending on input plain text block size, number of rounds and key size, various instances of RC5 can be defined and each instance is denoted as RC5-w/r/b where w=word size in bits, r=number of rounds and b=key size in bytes. Allowed values are:
| Parameter | Possible Value |
|---|
| block/word size (bits) | 16, 32, 64 |
| Number of Rounds | 0 – 255 |
| Key Size (bytes) | 0 – 255 |
Note – Since at a time, RC5 uses 2 word blocks, the plain text block size can be 32, 64 or 128 bits. Notation used in the algorithm:
| Symbol | Operation |
|---|
| x <<< y | Cyclic left shift of x by y bits |
| + | Two’s complement addition of words where addition is modulo 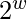 |
| ^ | Bit wise Exclusive-OR |
Step-1: Initialization of constants P and Q. RC5 makes use of 2 magic constants P and Q whose value is defined by the word size w.
| Word Size (bits) | P (Hexadecimal) | Q (Hexadecimal) |
|---|
| 16 | b7e1 | 9e37 |
| 32 | b7e15163 | 9e3779b9 |
| 64 | b7e151628aed2a6b | 9e3779b97f4a7c15 |
For any other word size, P and Q can be determined as:
P = Odd((e-2)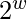 ) Q = Odd((
) Q = Odd((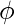 -2)
-2)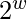 )
)
Here, Odd(x) is the odd integer nearest to x, e is the base of natural logarithms and 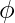 is the golden ratio. Step-2: Converting secret key K from bytes to words. Secret key K of size b bytes is used to initialize array L consisting of c words where c = b/u, u = w/8 and w = word size used for that particular instance of RC5. For example, if we choose w=32 bits and Key k is of size 96 bytes then, u=32/8=4, c=b/u=96/4=24. L is pre initialized to 0 value before adding secret key K to it.
is the golden ratio. Step-2: Converting secret key K from bytes to words. Secret key K of size b bytes is used to initialize array L consisting of c words where c = b/u, u = w/8 and w = word size used for that particular instance of RC5. For example, if we choose w=32 bits and Key k is of size 96 bytes then, u=32/8=4, c=b/u=96/4=24. L is pre initialized to 0 value before adding secret key K to it.
for i=b-1 to 0
L[i/u] = (L[u/i] <<< 8) + K[i]
Step-3: Initializing sub-key S. Sub-key S of size t=2(r+1) is initialized using magic constants P and Q.
S[0] = P
for i = 1 to 2(r+1)-1
S[i] = S[i-1] + Q)
Step-4: Sub-key mixing. The RC5 encryption algorithm uses Sub key S. L is merely, a temporary array formed on the basis of user entered secret key. Mix in user’s secret key with S and L.
i = j = 0
A = B = 0
do 3 * max(t, c) times:
A = S[i] = (S[i] + A + B) <<< 3
B = L[j] = (L[j] + A + B) <<< (A + B)
i = (i + 1) % t
j = (j + 1) % c
Step-5: Encryption. We divide the input plain text block into two registers A and B each of size w bits. After undergoing the encryption process the result of A and B together forms the cipher text block. RC5 Encryption Algorithm:
- One time initialization of plain text blocks A and B by adding S[0] and S[1] to A and B respectively. These operations are mod
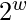 .
. - XOR A and B. A=A^B
- Cyclic left shift new value of A by B bits.
- Add S[2*i] to the output of previous step. This is the new value of A.
- XOR B with new value of A and store in B.
- Cyclic left shift new value of B by A bits.
- Add S[2*i+1] to the output of previous step. This is the new value of B.
- Repeat entire procedure (except one time initialization) r times.
A = A + S[0]
B = B + S[1]
for i = 1 to r do:
A = ((A ^ B) <<< B) + S[2 * i]
B = ((B ^ A) <<< A) + S[2 * i + 1]
return A, B
Alternatively, RC5 Decryption can be defined as:
for i = r down to 1 do:
B = ((B - S[2 * i + 1]) >>> A) ^ A
A = ((A - S[2 * i]) >>> B) ^ B
B = B - S[1]
A = A - S[0]
return A, BAdvantages:
High level of security: RC5 is designed to provide a high level of security against attacks, including brute-force attacks and differential cryptanalysis. It uses a variable-length key and can operate on block sizes of up to 256 bits, making it difficult for attackers to break the encryption.
Fast encryption and decryption: RC5 is known for its fast encryption and decryption speeds. It uses simple mathematical operations such as modular arithmetic and bit shifting, which can be efficiently implemented on modern CPUs and hardware.
Flexible key length: RC5 allows for a variable-length key, which can range from 0 to 2040 bits. This flexibility allows users to choose a key length that suits their security needs and resources.
Disadvantages:
Vulnerable to side-channel attacks: RC5 is vulnerable to side-channel attacks, such as timing attacks and power analysis attacks. These attacks exploit information leaked through the implementation of the algorithm, rather than attacking the algorithm itself.
Limited adoption: RC5 is not widely adopted in practice compared to other encryption algorithms, such as AES. This means that there may be fewer resources and tools available to support RC5 in various applications and systems.
Patent issues: RC5 was subject to a patent held by RSA Security, which limited its adoption and use in commercial applications. Although the patent has since expired, it may have contributed to the limited adoption of RC5 compared to other encryption algorithms
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...