Default flow of traffic (ASA)
Last Updated :
22 Nov, 2021
Prerequisite – Adaptive security appliance (ASA)
ASA is a Cisco security device that can perform a firewall capability with VPN capabilities, routing support, antivirus capability, and many other features.
Security levels –
ASA uses a security level associated with a routable interface. Remember, the ASA interface is by default in routed mode i.e operating at layer 3. These interfaces are assigned security levels which are numbers ranging from 0 to 100. The bigger the number, the more will be the trust to the network connected to that ASA interface.
On the basis of security levels, ASA takes action (whether to permit or deny the packet).
Also, note that we can assign names to the ASA interface like inside, outside, or DMZ. As soon as we assign these names to an interface, it automatically assigns a security level to itself. For example, if we have assigned a name inside to an interface, it will assign 100 (Security level) to itself i.e most trusted network. If we assign the name Outside or DMZ or any other name to an interface, it will assign security level 0 to automatically. These are default values and can be changed.
It is a good practice to give security level 100 (maximum) to inside (most trusted network), 0(least) to outside (untrusted or public network), and 50 to DMZ (organization public device network).
Note –
It is not mandatory to assign a name (INSIDE, OUTSIDE, or DMZ) to the ASA interface but it is good practice to assign these names as they are simple and meaningful.
Default Flow of traffic –
Note that if the traffic is inspected then the state of the packet will be kept i.e connection table will be maintained therefore the replies will be allowed (from an untrusted network) while if the action on the traffic is pass, only the traffic will be passed and no connection table is maintained.
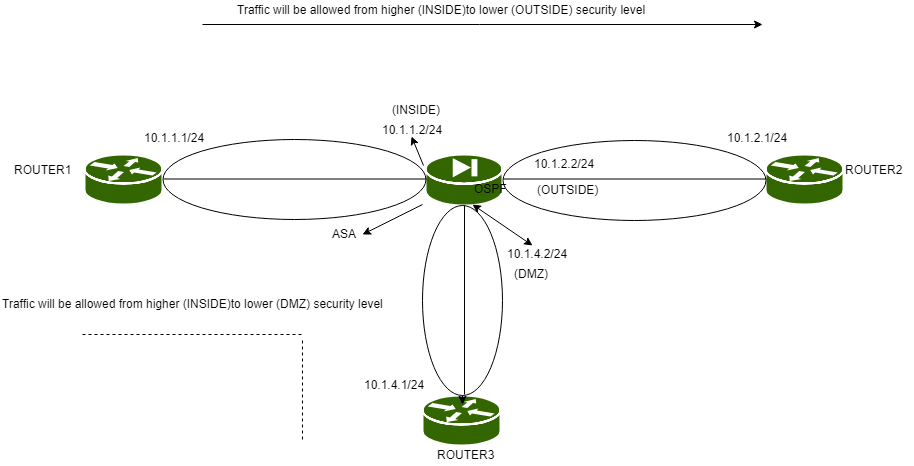
By default, ASA allows a flow of traffic from higher security levels to lower security levels. If the traffic is initiated by the devices in higher security levels, then it will be passed to go through the firewall to reach the devices in lower security levels like outside or DMZ.
And if the (TCP or UDP) traffic is initiated from a higher security level then the replies (for higher security level) from lower security level (outside or DMZ) are allowed. This is due to default stateful inspection (which means a state of the packet will be maintained in the connection table).
But if the traffic is of ICMP that is to be sent from higher security level to lower security level then it will reach the lower security level device and the lower security level will also send echo reply but the firewall (ASA) will drop it as only TCP and UDP traffic is inspected by default.
If we want ICMP traffic to be inspected by the ASA then we have to do it manually by the command.
asa(config)#fixup protocol ICMP
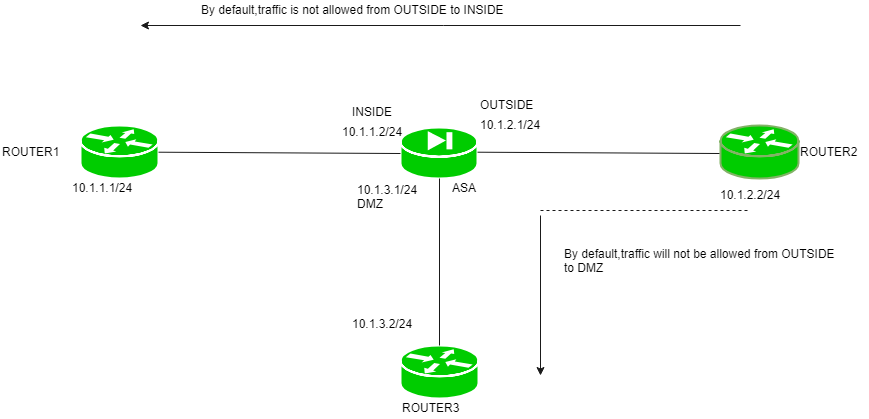
Also, if the lower security level (outside or DMZ) wants to send any traffic (TCP, UDP, or ICMP) to the higher security level then it is denied by the ASA firewall due to its default policy. To allow it, an access list can be used.
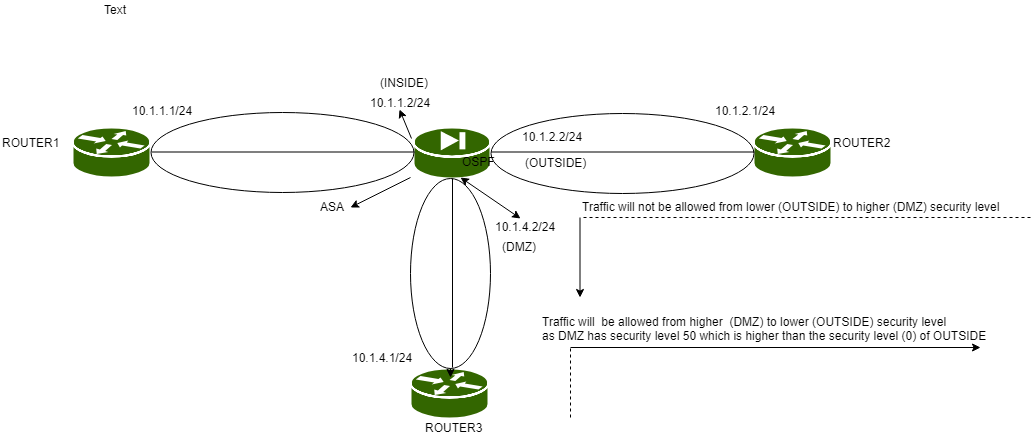
Also, note that when we give security level 50 to DMZ, 100 to inside, and 0 to outside, then the traffic will be allowed from DMZ to outside but DMZ devices still not be able to reach inside devices.
Also, by default, if two interfaces have the same security level then the traffic will not be allowed.
But the traffic can be allowed manually (between the two interfaces having the same security level) by the command
asa(config)#same-security-traffic
permit inter-interface
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...