Cisco Wireless Architecture and AP Modes
Last Updated :
26 Nov, 2022
Cisco Wireless Architecture and AP modes connect a wireless network to a wired network to safely transfer data. Cisco Wireless Architecture and AP modes are classified into three categories:
- Autonomous AP architecture
- Cloud-based AP architecture
- Split MAC AP architecture.
Cisco Three-Layer Hierarchical Model:
Providing connectivity between wireless and wired networks to transport data is the primary purpose of Cisco Wireless Architecture and AP modes. Many wireless clients can be connected at once with autonomous AP architecture, and the network functions like a LAN. The Central Access Point, which controls all wireless networks and devices, is provided by the autonomous AP design. Data may be transported between wireless and wired networks thanks to the central access point’s wireless and wired capabilities. The process of encryption and decryption takes place when data is transmitted. The Core layer, Distribution Layer, and Access Layer comprise Cisco’s proprietary three-layer design. An upgraded version of the Cisco three-layer design is the Cisco Wireless Architecture and AP modes. See the graphic below for an explanation of the three-layer hierarchical architecture used by Cisco.
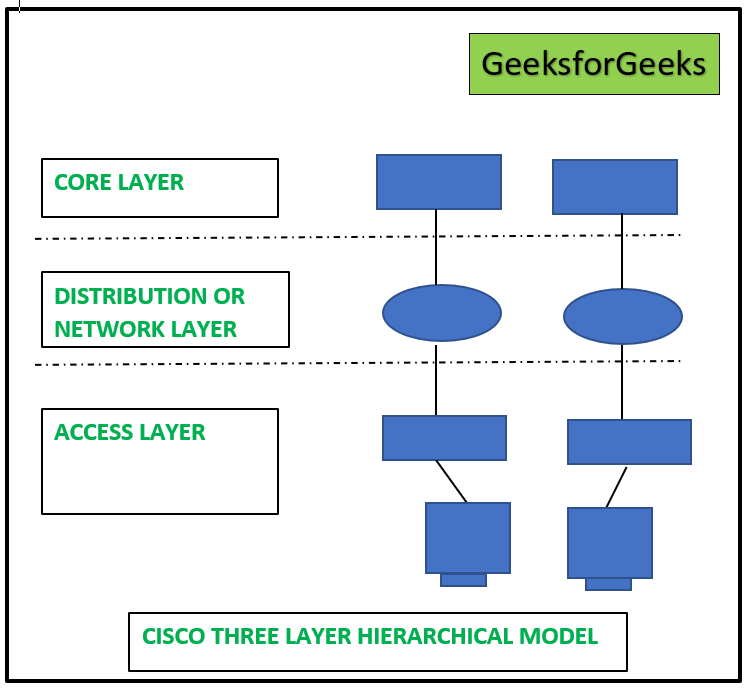
Basic service sets also referred to as BSSs, are offered by the autonomous AP architecture of Cisco Wireless Architecture. In the access layer of Cisco’s three-layer hierarchical architecture, autonomous APs link wireless service set identifiers (SSIDs) with wired virtual LANs. As indicated in the below diagram, a network can use 100 or 1000 APs to offer connectivity to the customers.

The fastest and easiest method for data transfer across wireless and wired networks is used by an Autonomous AP architecture of Cisco Wireless Architecture and AP modes. The access point serves as a bridge between the wired and wireless networks. A device linked to an AP wireless network can send data to another wirelessly connected device without using the wired network. The trunk mode port connects to the core switch and access layer switches in the above image to transport data between VLANs. Each autonomous AP is allocated a fixed IP address for remote management and setup. The primary parameters that must be configured are SSIDs, VLANs, Channel and transmission power, and so on.
Each autonomous AP is necessary to communicate in order to exchange data and maintain VLANs. All AP SSIDs and their VLANs must be extended to layer 2 in order for all VLANs to communicate with the wired network.
Cloud-Based AP Architecture in Cisco Wireless Architecture:
Installing an AP management platform, such as Cisco Prime Infrastructure, is necessary in the case of cloud-based AP architecture in order to configure and administer any autonomous AP in the network. The management platform needs to be set up in the internet cloud so that any autonomous AP can be managed and configured from a single location. For centralized management, monitoring the wireless performance, and controlling the actions of wireless autonomous APs, Cisco Wireless Architecture & AP modes employ Cisco Meraki, a cloud-based management solution. Cisco Meraki AP only needs to register with it once; no manual setup or purchases are necessary. All APs will automatically configure themselves in accordance with Cisco Meraki management after registering with the company. Any AP can be configured using the Cisco Meraki dashboard after auto-configuration. The ability to centrally design, administer, and monitor all APs from the cloud is its most significant feature. The function of the Cisco Meraki controller in a cloud network is explained in the graphic below. Cisco Meraki pushes configuration code and updates to cloud network APs, and it can also adjust the channel and transmission power of any AP. Cisco Meraki has complete control over AP statistics and interfaces.
Split MAC Architecture:
All the network’s autonomous access points (APs) are protected by split MAC structures. Each AP operates under its own security policy. In order to manage security-related concerns, such as intrusion detection and prevention systems, QoS, bandwidth management, etc., a centralized location is used. According to the graphic below, any autonomous AP’s actions can be classified into two categories: group management functions, and real-time functions.
- The Autonomous AP management functions include RF power output management, QoS, security management, client authentication, and other management programs. On the other hand, real-time functions are concerned with the transfer of data frames, data encryption and decryption, and so on.
- Automated AP receives and transfers 802.11 frames in real-time. The autonomous AP communicates with the clients via the physical layer known as the MAC layer. The autonomous AP is governed by a centralized administrator for RF power output and security management.
- The hardware of an autonomous AP is known as a lightweight access point because it solely performs real-time operations. WLC is often in charge of managing autonomous AP (wireless LAN controller). The key things used for security performance are user authentication and security policy management, among other things. Layers 1 and 2 are utilized to move frames within the same RF domain.
- CAPWAP is an abbreviation for Control and Provisioning of Wireless Access Point tunneling protocol, which is used to encapsulate data within a wireless network. The CAPWAP connection is made up of two distinct tunnels, CAPWAP control messages, and CAPWAP data.
CAPWAP Control Messages in Split MAC Architecture:
The carriers of CAPWAP control messages exchange the codes required to set up and operate the AP. Only the associated WLC is able to securely control the AP using the authenticated and encrypted control messages.
CAPWAP Data in Split MAC Architecture:
CAPWAP data is used to transport packets between wireless clients linked to a single AP. Data packets traveling over the data tunnel are not encrypted by default. When data encryption is enabled, datagram transport layer security is used to safeguard packets (DTLS).
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...