Auditd Tool for Security Auditing on Linux Server
Last Updated :
01 Dec, 2022
Auditd is short for Linux Audit Daemon which is a tool in Linux used for the process of collecting and writing the audit log files of the system. The term “daemon” is used for the processes which run in the background of service in work, this means that this tool is continuously operating behind the scenes.
Below given are some important features of the Auditd system:
- It is a very self-reliant tool that does not depend on the help of external programs.
- It is Highly configurable allowing us to see a wide range of system operations.
- Any potential threats can also be detected with the help of this tool.
- It can work in Sync with the other intrusion detection system to find out about intruders.
- forensic audits also rely on this tool.
Note: We are using the OS as a root user so we are not writing sudo everywhere.
Installing Auditd on the system:
This tool can be installed by using the apt-get or the wajig facility which are both used for downloading packages on Linux. For the purpose of demonstration let us search and see what the result for the search audits comes:
wajig search auditd
It says user space tools for security auditing. This is the same thing that we discussed in the intro section.
Use the below command to install auditd on your system:
apt-get install auditd
Confirm whether it is installed successfully or not:
auditctl -l
If a message like this is obtained then auditd is successfully installed. Currently, it is saying ”No Rules”, let us understand that in the next section.
Understanding How Auditd works:
Understanding audit files and access to directories:
The most trivial thing that can be done with the help of Auditd is to be informed when someone alters a file or a directory. But how can we find that? Use the below command to do the same:
auditctl -w /etc/passwd -p rwxa
Understanding the flags used:
- -w flag —> Inserts a watch for a filesystem object in the path.
- -p flag —-> This defines the type of permission access to the filesystem.
- rwxa —-> These are the read, write, and execute attributes that are bonded to the -p flag.
Auditing directories:
Let us create a sample directory by the name of tempdir for the purpose of auditing it. Use the below command to audit this directory:
auditctl -w /tempdir/
With the help of the above command, the auditd tool will keep a watch over the access of this directory. Let us try to write auditctl -l command once again:
auditctl -l
You can see that previously the message said “No Rules”, but now there are some new rules added.
Viewing the Logs which are created:
After the creation of some rules, we can see the logs with the help of the auditd tool. Auditd provides a special tool for this which is called ausearch. To view the logs type the below command:
ausearch -f /etc/passwd
To see the audit logs of the tempdir write the below command, the audit log files are stored in the /var/log/audit/audit.log path.
tail -5 /var/log/audit/audit.log
You can see the audit logs of the tempdir that we created.
Viewing the audit reports which are created:
Auditd also provides us with a tool for keeping a track of all our audit logs and changes. The name of this tool is aureport. This tool gives us a complete summary of all the reports from the audit log. Use the below command to get audit reports:
aureport
We can use this command with the -au flag to see which users were unable to attempt a successful login.
aureport -au
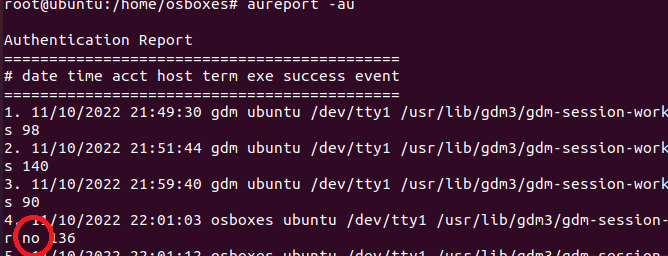
No indicates a failed attempt to login.
To see the complete details about all the modifications we can use the aureport command with the -m flag.
aureport -m
The Auditd configuration file:
To see the Auditd config file type the below command:
vi /etc/audit/rules.d/audit.rules
Till now we have created a couple of rules, if we want to make them permanent then we can add those rules in this config file. Add your created rules and save the file:
After permanently adding the rules in the file and saving it restart the auditd daemon for those changes to take effect.
service auditd restart
So this way you can audit the log files and directories in your system, there are a lot more options in Auditd but discussing all of them is not possible, if you want to quench your curiosity then you can read and find more about auditd in its manual page.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...