AQUATONE is a set of tools used for performing reconnaissance, scanning, and discovery o domain names. AQUATONE can discover subdomains on a given target domain using OSINT source and the most common domain brute force method. After discovering the subdomain, the AQUATONE tool can scan the domain for standard web ports and HTTP headers information. HTML bodies and snapshots can be collected and considered as the report to analyze the attack environment quickly.
To increase the efficiency and simpleness of aquatone tool, it is divided into 3 phases
- Discovery
- Scanning
- Gathering
Discovery
The first stage of an AQUATONE assessment is the discovery stage, where subdomains are discovered on the victim domain using open sources, services, and the more common dictionary brute force approach. aquatone-discover ships with the following collector modules:
- Dictionary brute force
- DNSDB.org
- Google Transparency Report
- HackerTarget
- Netcraft
- Shodan (requires API key)
- ThreatCrowd
- VirusTotal (requires API key)
Scanning
The scanning stage is where AQUATONE will enumerate the recognized hosts for open TCP ports that are usually used for web services.
Gathering
The last stage is the gathering phase, in which the results of discovery and scanning stages are used to make the discovered web services return and save HTTP response headers packets and HTML bodies, as well as taking the snapshots of how the web page or domain looks like in web browser which makes the analysis much more accessible.
Installation of Aquatone Tool in Kali Linux
Step 1: Download Google Chrome on your Linux System, by using the following command.
wget https://dl.google.com/linux/direct/google-chrome-stable_current_amd64.deb
Step 2: Install Google Chrome, using the following command
sudo apt install ./google-chrome-stable_current_amd64.deb
Step 3: Download Aquatone Zip from Github Page.
https://github.com/michenriksen/aquatone/releases/tag/v1.7.0
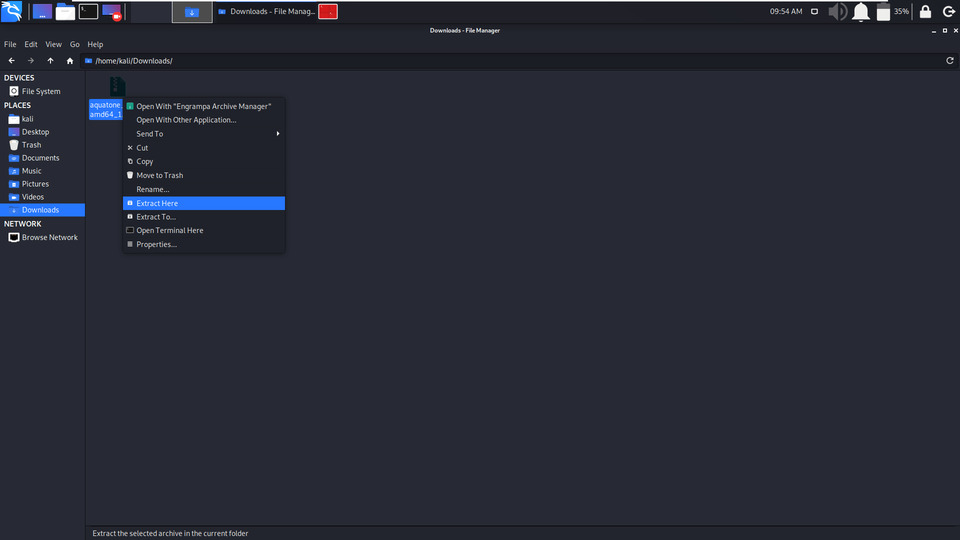
Step 4: After Downloading Extract the zip folder.
Right Click and Extract
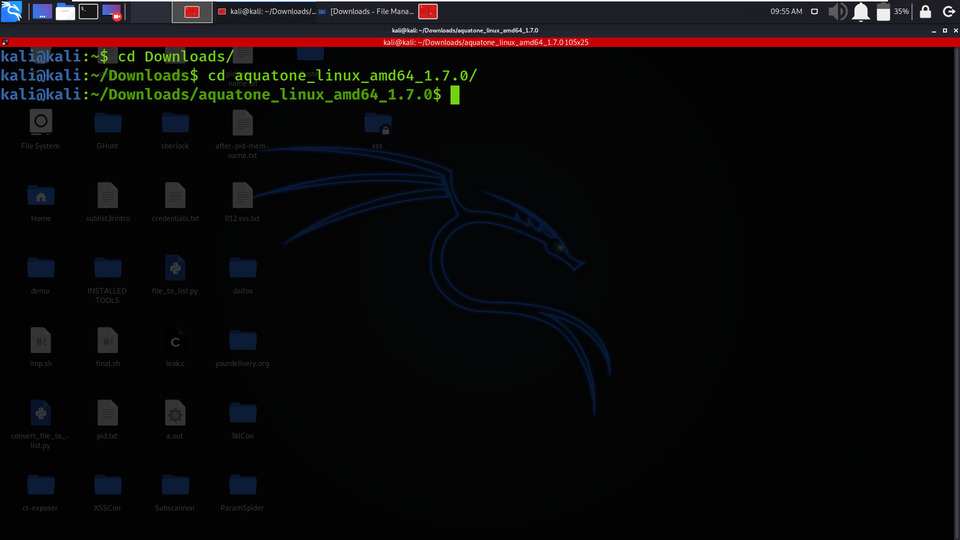
Step 5: Go to Terminal and change directory to Downloads
cd Downloads
cd aquatone_linux_amd64_1.7.0/
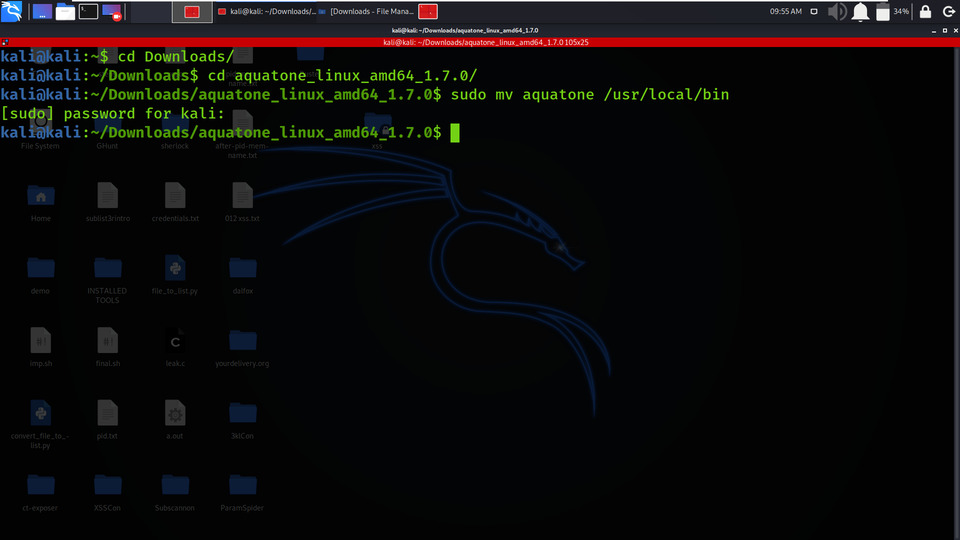
Step 6: Move Aquatone in the bin directory.
sudo mv aquatone /usr/local/bin/
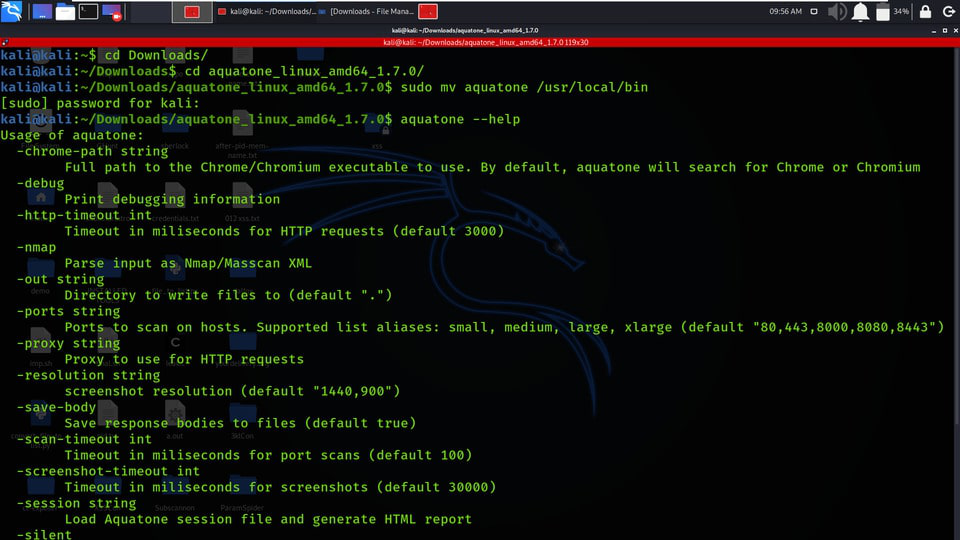
Step 7: Check the help page of aquatone for a better understanding of usage, use the following command.
aquatone --help
Working with AQUATONE Tool
Example 1: Discovery
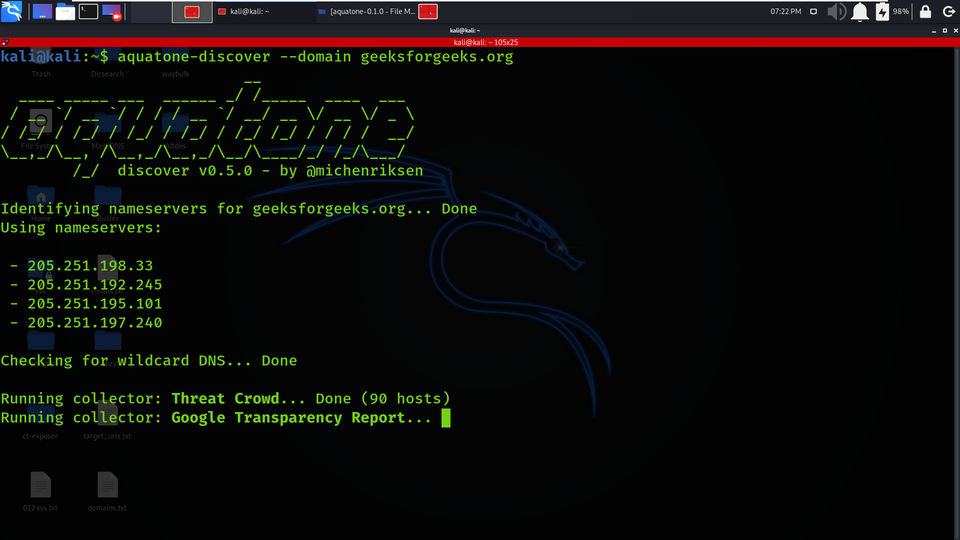
aquatone-discover --domain geeksforgeeks.org
1. The aquatone does is to identify the information about the target domain (geeksforgeeks.org).
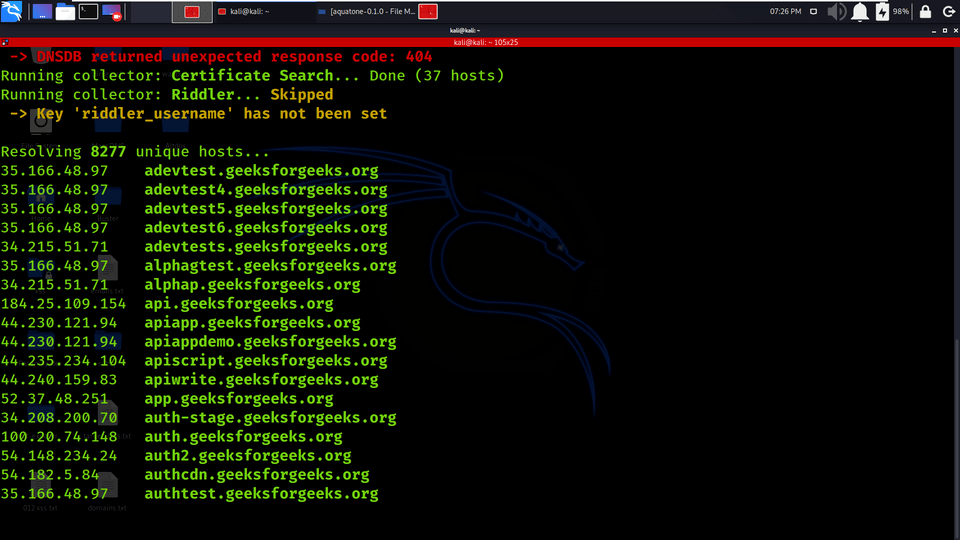
2. 8277 Unique Hosts are Resolved along with the IP addresses and the subdomains.
Example 2: Scanning
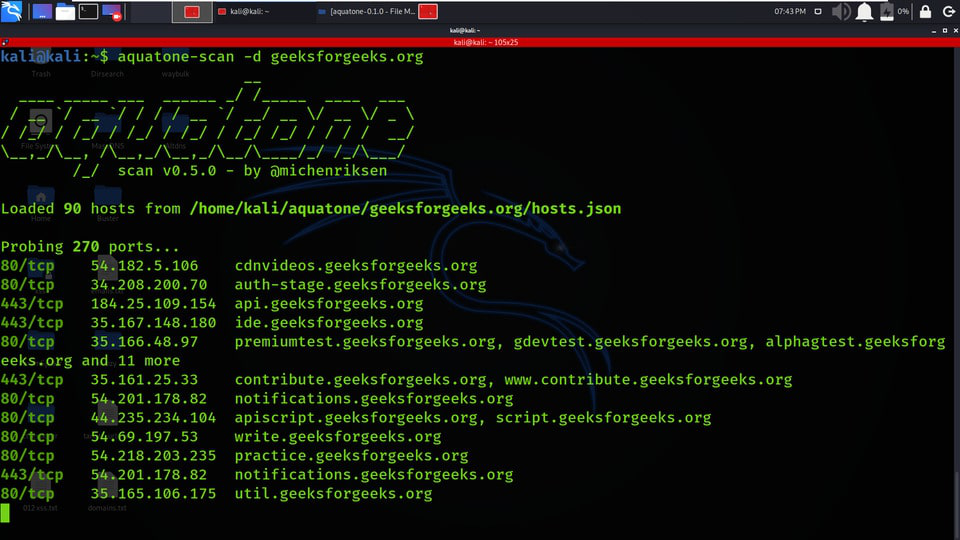
aquatone-scan -d geeksforgeeks.org
1. Using the hosts.json file, which contains the 90 hosts is used for scanning to get the port details.
2. All the Probed Ports are stored in open_ports.txt with IP address and port number opened.
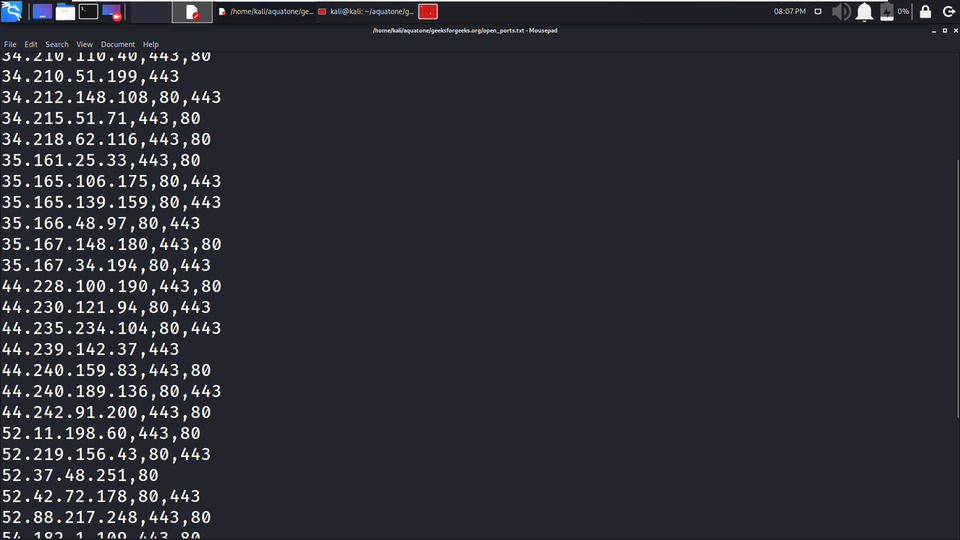
3. All the URLs are stored in urls.txt file.
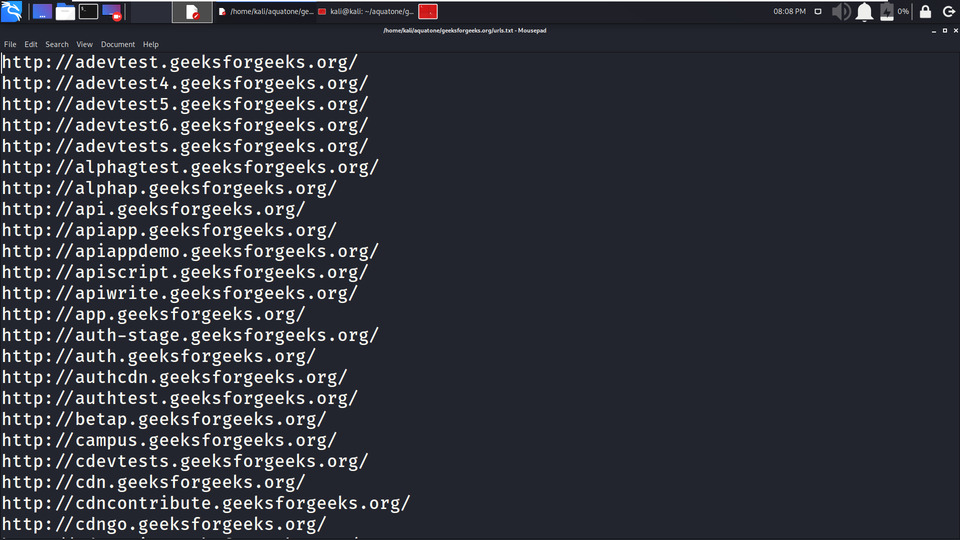
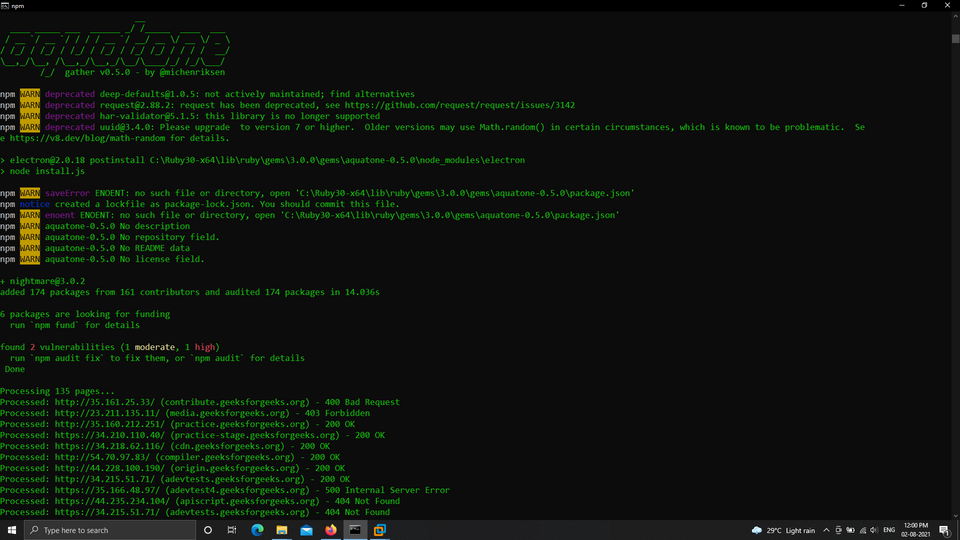
Example 3: Gathering
aquatone-gather -d geeksforgeeks.org
In this example, we are gathering the information on geeksforgeeks.org (like subdomains, status codes, Ip addresses, etc).
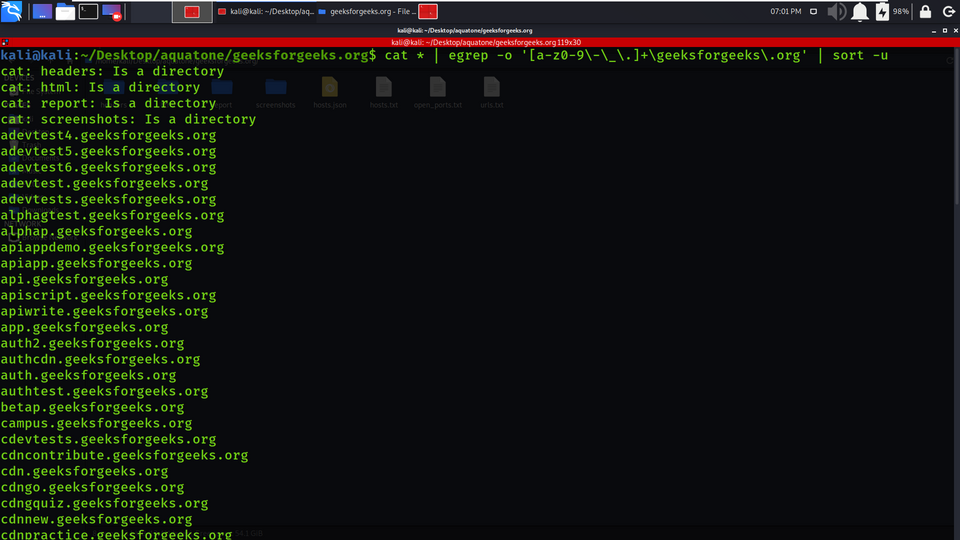
Example 4: CLI Tricks
Getting more Subdomains of geeksforgeeks.org (filtering the results)
cat * | egrep -o '[a-z0-9\-\_\.]+\geeksforgeeks\.org' | sort -u
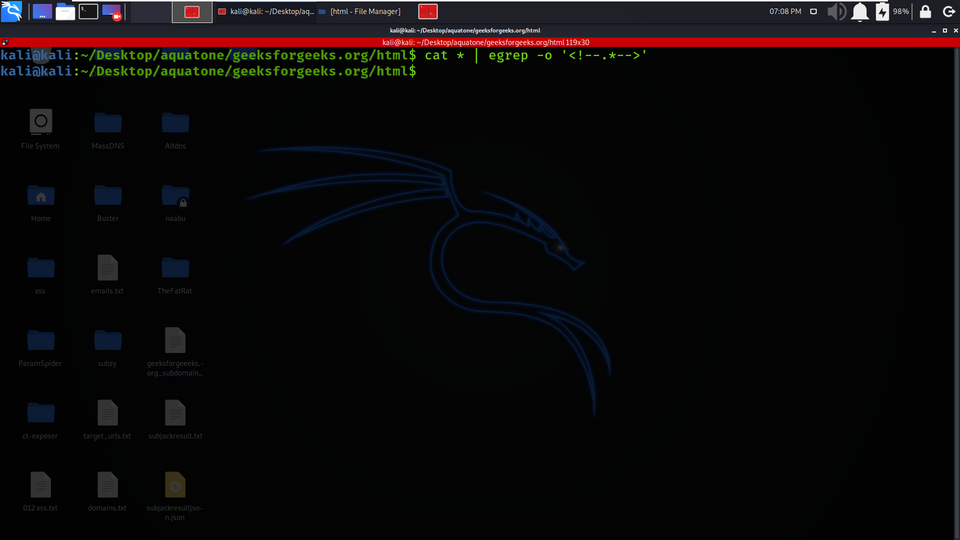
Example 5: Finding HTML Comments
Using Filtering skills to get HTML comments from HTML directory data.
cat * | egrep -o '<!--.*-->'
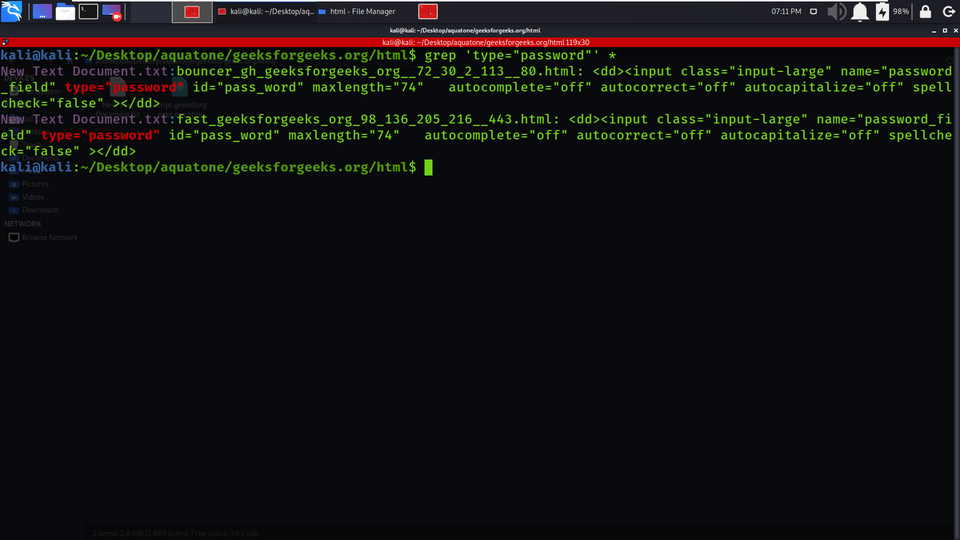
Example 6: Finding pages with password fields
Finding Password fields using Filtering the results (grep).
grep 'type="password"' *
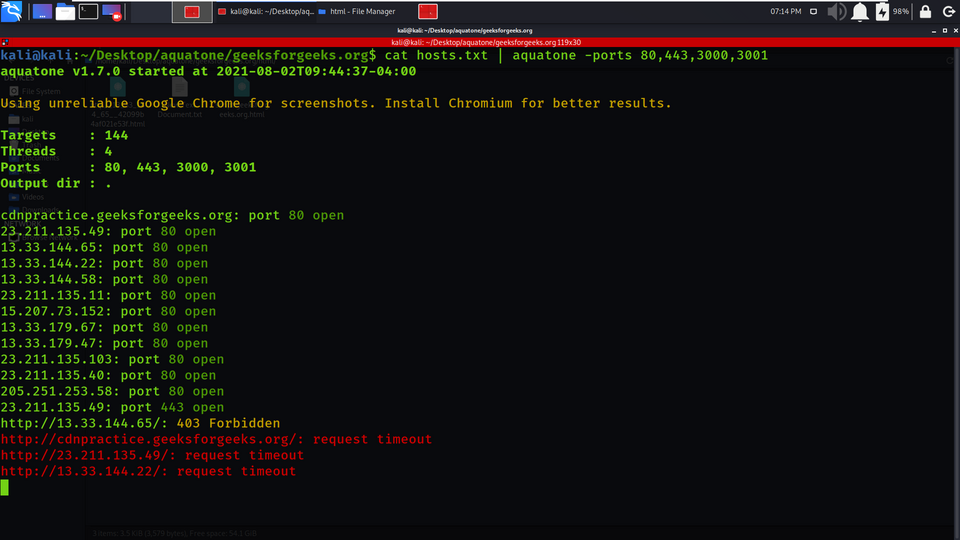
Example 7 : Specifying ports to scan
1. By default, the Aquatone tool will scan target hosts with a small list of commonly used HTTP ports: 80, 443, 8000, 8080, and 8443. We can change this variety of ports list using the -ports flag. You can check the help section for more details
cat hosts.txt | aquatone -ports 80,443,3000,3001
2. Aquatone also supports nicknames of built-in port records to make it more comfortable for you:
- small: 80, 443
- medium: 80, 443, 8000, 8080, 8443 (same as default)
- large: 80, 81, 443, 591, 2082, 2087, 2095, 2096, 3000, 8000, 8001, 8008, 8080, 8083, 8443, 8834, 8888
- xlarge: 80, 81, 300, 443, 591, 593, 832, 981, 1010, 1311, 2082, 2087, 2095, 2096, 2480, 3000, 3128, 3333, 4243, 4567, 4711, 4712, 4993, 5000, 5104, 5108, 5800, 6543, 7000, 7396, 7474, 8000, 8001, 8008, 8014, 8042, 8069, 8080, 8081, 8088, 8090, 8091, 8118, 8123, 8172, 8222, 8243, 8280, 8281, 8333, 8443, 8500, 8834, 8880, 8888, 8983, 9000, 9043, 9060, 9080, 9090, 9091, 9200, 9443, 9800, 9981, 12443, 16080, 18091, 18092, 20720, 28017
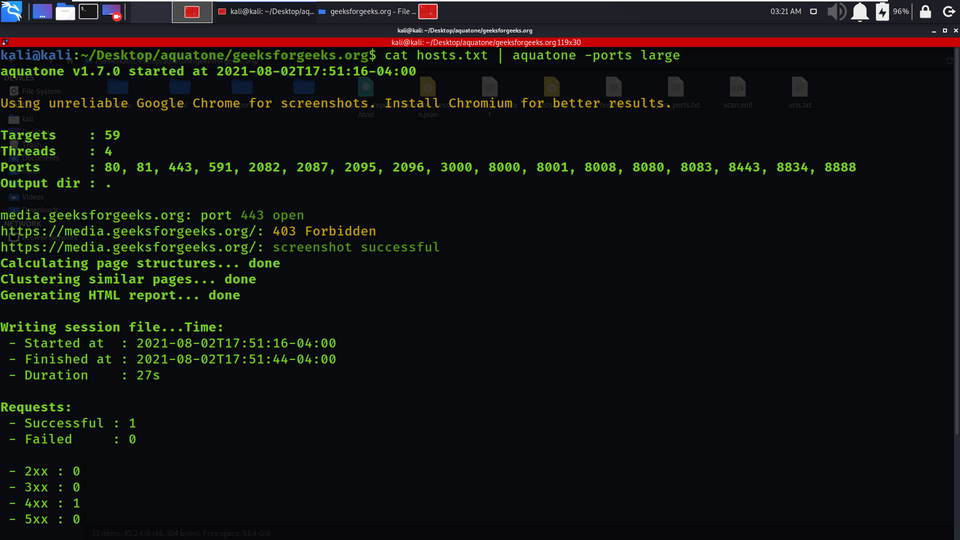
cat hosts.txt | aquatone -ports large
In the below screenshot, we have used large ports lists for getting the ports enabled on hosts.
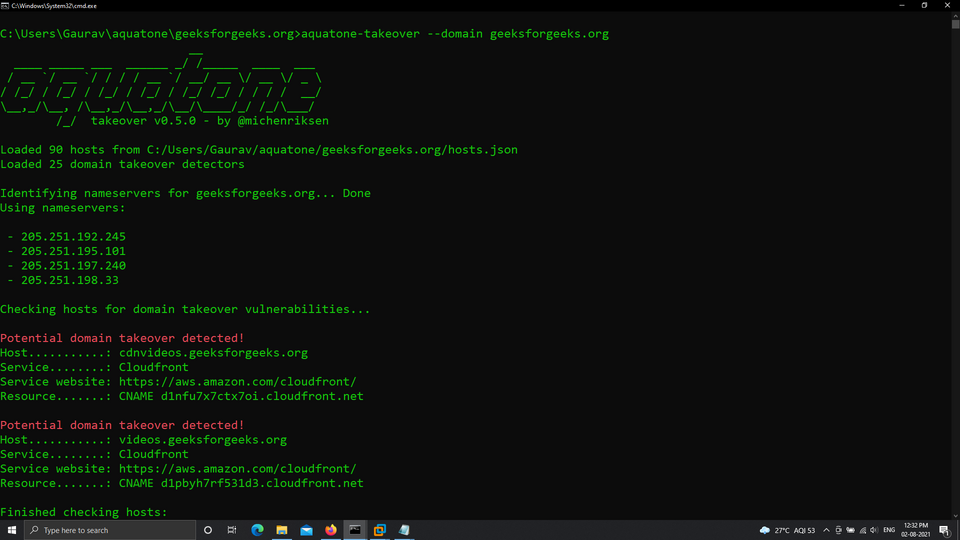
Example 8: Subdomain Takeover
aquatone-takeover --domain geeksforgeeks.org
aquatone has the feature to check the domain if it is vulnerable to Subdomain Takeover or not.
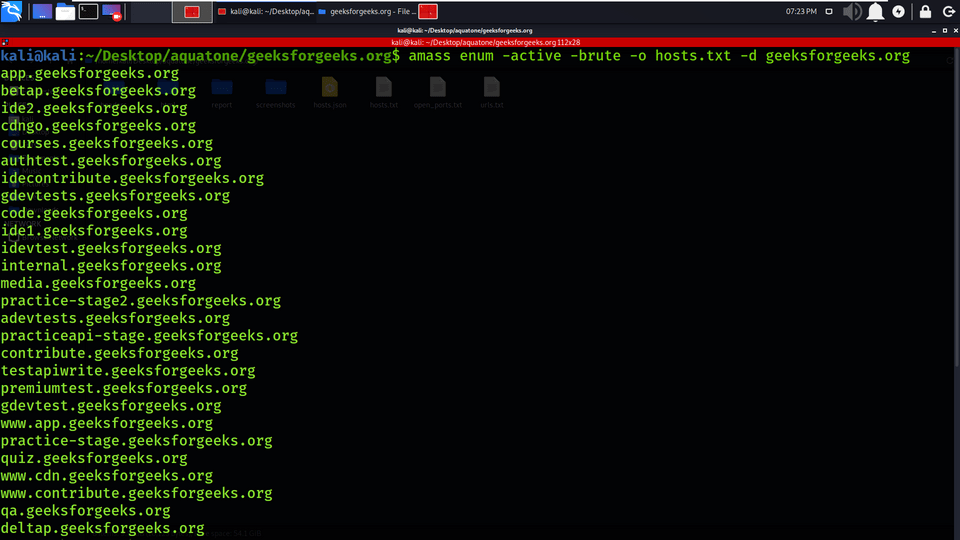
Example 9: Amass DNS enumeration
amass enum -active -brute -o hosts.txt -d geeksforgeeks.org
Aquatone has the feature to integrate with the Amass tool for DNS Enumeration.
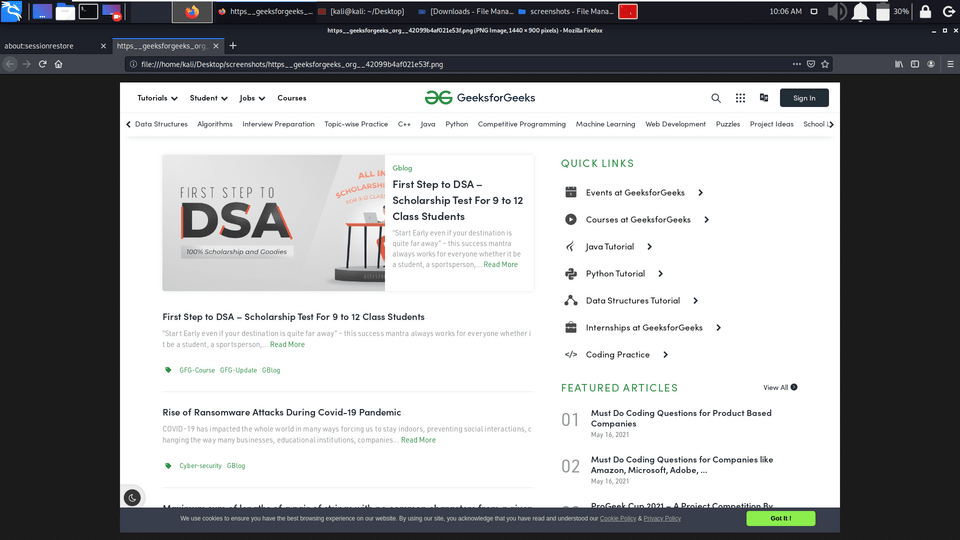
Example 10: Screen Shots
1. Aquatone is popular for its Screenshot taking feature, in the below screenshot aquatone has taken the screenshot of geeksforgeeks.org
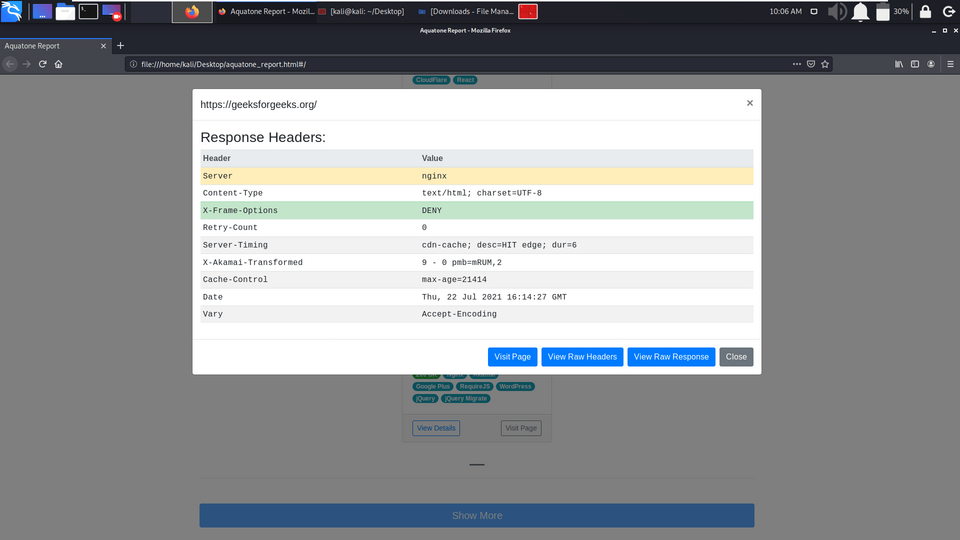
Example 11: More Information about geeksforgeeks.org
You can see we have got more information about geeksforgeeks.org like Server information, Response Header info, etc.
AQUATONE is a very useful tool for discovering information of multiple targets at the same time. The Screenshot-taking feature makes it more attractive and special as attackers need to check each subdomain manually, so to avoid this attackers can now run the aquatone on various subdomains at a time and check the subdomain’s status (active/inactive).
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...