Approaches to Information Security Implementation
Last Updated :
01 Mar, 2024
In order to determine the safety of data from potential violations and cyberattacks, the implementation of the security model has an important phase to be carried out. In order to ensure the integrity of the security model, it can be designed using two methods:
1. Bottom-Up Approach: The company’s security model is applied by system administrators or people who are working in network security or as cyber-engineers. The main idea behind this approach is for individuals working in this field of information systems to use their knowledge and experience in cybersecurity to guarantee the design of a highly secure information security model.
- Key Advantages:disadvantages An individual’s technical expertise in their field ensures that every system vulnerability is addressed and that the security model is able to counter any potential threats.
- Disadvantage:: Due to the lack of cooperation between senior managers and relevant directives, it is often not suitable for the requirements and strategies of the organisation.
2. Top-Down Approach: This type of approach is initialized and initiated by the executives of the organization.
- They formulate policies and outline the procedures to be followed.
- Determine the project’s priorities and expected results
- Determine liability for every action needed
- Advantages And disadvantagesand of top-down implementation:
This approach looks at each department’s data and explores how it’s connected to find vulnerabilities. Managers have the authority to issue company-wide instructions while still allowing each person to play an integral part in keeping data safe. Compared to an individual or department, a management-based approach incorporates more available resources and a clearer overview of the company’s assets and concerns.
A top-down approach generally has more lasting power and efficacy than a bottom-up approach because it makes data protection a company-wide priority instead of placing all the responsibility on one person or team. Data vulnerabilities exist in all offices and departments, and each situation is unique. The only way for an information security program to work is by getting every manager, branch, department, and employee in agreement with a company-wide plan.
Implementing a layered information security approach:
Cybersecurity is critical for businesses of all types and sizes. In one survey, more than half of participants cited cybersecurity as a top concern for their organization. Data and network compromises can have devastating effects that many businesses never fully recover from. In 2019, cyberattacks cost individual businesses an average of $200,000.
Attacks come in several forms, such as phishing scams, hacking, unauthorized access at physical locations, Trojan viruses, ransomware, and password attacks. Because there are so many possible vulnerabilities, a layered approach is the best method for implementing total protection across departments.
Infosec layering accounts for all standard data protection along with other facets of cybersecurity, including web, network, device, application, software, and physical security. It also includes having a disaster recovery and data backup plan. Layered protection breaks larger security concerns into smaller, more manageable pieces. It lets you customize the type and protection level depending on specific needs, such as department, device, or stored data.
Consider a healthcare business. In the financial department, data integrity is likely the top concern to prevent overcharging or undercharging accounts. But the patient records department focuses on data security, privacy, and access control. This is where a layered approach comes in. Layered approaches are woven together so each area of information security relies on the other, creating a stronger, more defensive blanket of protection that makes it harder for outside attackers to gain entry.
Web and network security:
Web and network security cover creating policies and safeguarding all browsers, private networks, shared networks, and online user accounts, such as:
- Clearly assign user roles for each person with access, including management, employees, third-party contractors, and partners
- Various encryption methods for on-site and off-site employees and contractors
- IP network-wide security for all network traffic
- Firewalls, antivirus and antimalware systems, intrusion alerts, and defense software
- Disabling web browser pop-ups
- Security for all webmail, including attachments and possible phishing scams
- Using a secure, up-to-date web browser with an individual, controlled employee access account
- Mobile device security for company phones, tablets, and smart devices
- Network segmentation whenever applicable
- Data loss prevention (DLP) for files and messages
Device and app security:
Device and app security applies to all computers, tablets, company phones, smart devices, applications, user software, computer programs, and online accounts. Precautions include:
- Keeping all apps and software and their subsequent security up to date
- Requiring unique passwords and log-in credentials for each user, changed regularly
- Implementing regular device and system maintenance windows throughout the month
- Keeping thorough, up-to-date records for all device and app activity, including possible, detected, or isolated threats
- Giving each device user and account a host intrusion detection system
- Removing unnecessary apps, software, user accounts, and devices from rotation
- Implementing patch management to keep everything up to date and automatically fixed when new patches are released
It is more likely to succeed. That strategy usually provides strong support from top management by committing resources, a consistent preparation and execution mechanism and opportunities to affect corporate culture.
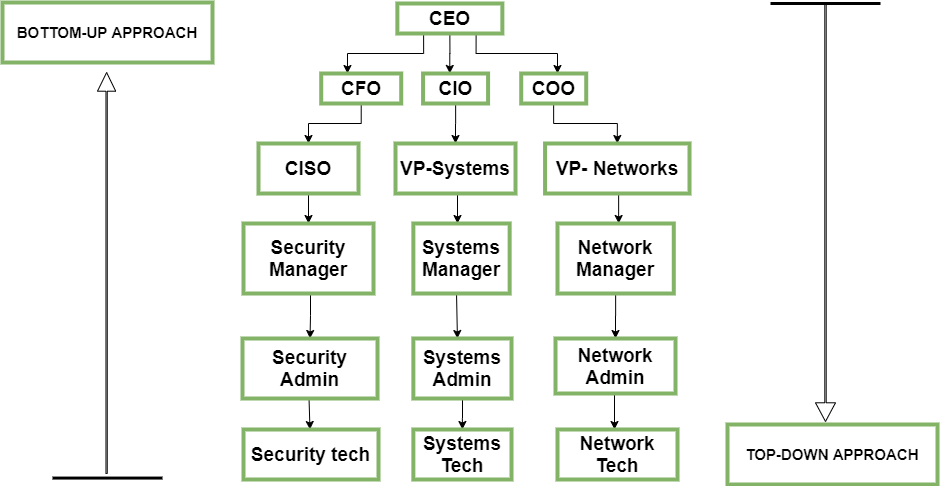
Security management issues have been handled by organizations in various ways. Traditionally, companies adopted a bottom-up approach, where the process is initiated by operational employees and their results are subsequently propagated to upper management as per the proposed policies. Since management has no information about the threat, the effects, the idea of resources, possible returns and the security method, this approach has occasionally created a sudden and violent collapse. On the contrary, the top-down approach is a highly successful reverse view of the whole issue. Management understands the gravity and starts the process, which is subsequently collected systematically from cyber engineers and operating personnel.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...