Applications of Cybersecurity
Last Updated :
23 Feb, 2022
In this article, we will learn about cyber security and its applications. Cybersecurity is basically the process of protecting our computers, networks, and data from digital passive attacks. Hackers and cybercriminals always try to steal our data by using infected files with worms, viruses, and trojans to make some financial profit.
Importance of Cybersecurity
- Cybersecurity is just an ethical practice to protect our devices from such hackers and make them more secure. People involved in cybersecurity perform security measures and operations in order to keep our data and devices safe. Cybersecurity basically deals with protecting our network, devices, and data from illegal and unauthorized access by other people. Hackers and cybercriminals use the Internet as an opportunity to crack into other’s people devices by using spyware, malware and carrying out cyber attacks.
- The main purpose of Cybersecurity is to protect all the users on the Internet from infected files, malware, and digital attacks which lead the users to access private sensitive information of users, extort ransom from users by using their private data or even disrupting important critical infrastructure like shutting down power supplies and military infrastructure.
- Cybersecurity helps to solve pre-built vulnerabilities in applications and helps them to remain stable throughout. More and more devices are getting connected to the Internet, hence it is more and more important to secure all the devices over the Internet to protect them all against unauthorized access.
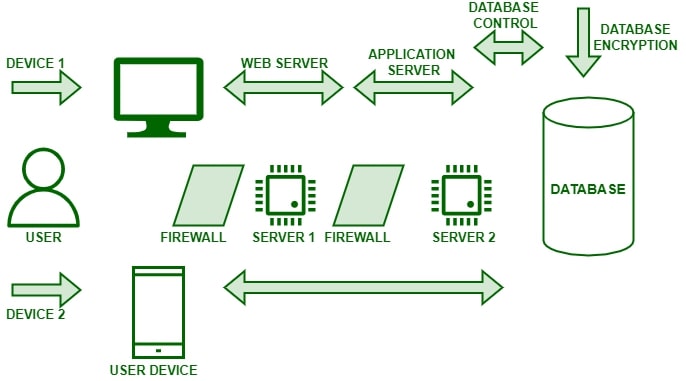
Types of Cybersecurity
- Information Security: Information security mainly deals with protecting the private information of the users from hackers and cybercriminals. It prevents theft of data and also the condition where hackers extort ransom from users for their sensitive information. It basically includes User authorization, authentication, and cryptography.
- Network Security: Network Security mainly deals with protecting the integrity and safety of the network components used by the users and also avoiding denial of service attacks where the original and legitimate cannot be able to use that computer network. It includes services like firewalls, antivirus software, and VPNs (Virtual Private Network).
- Application Security: Application Security deals with protecting the applications and programs on the computer system from potential hacking threats and vulnerabilities that may occur due to different flaws that hackers take to their advantage.
Cybersecurity Threats:
The various Cybersecurity Threats:
- Illegal Websites: Hackers often include malware, spyware, and worms on these shady websites which offer free antivirus software or any program or data. It includes malware and ransomware that may be very harmful to the user’s computer system. These types of websites contain fraud and spyware containing links and URLs which lead to downloading of viruses and spyware on the computer.
- File sharing: File sharing platforms transfer data including files, folders, photos, apps, etc. via the Internet, but this is used as an opportunity by the hackers to spread spyware and malware along with these files so that their private sensitive information can also be leaked.
- Emails: Most of the Emails are responsible for spreading various malware, spyware, ransomware, and viruses on our devices. Mostly, those emails that come from unknown sources and they contain some shady websites links may contain hidden infected files in them.
- Phishing: Phishing deals with sending fraud-related emails and messages to a large number of users that contain some illegal and malware containing URLs so that when the user clicks them, the malware, spyware, or ransomware automatically gets installed on the user’s device in the background.
Applications of Cybersecurity:
- DDoS security: DDoS stands for Distributed Denial for Service attack. In this digital attack, the attacker uses multiple numbers of devices to keep the web server engaged in accepting the requests sent by him from the multiple devices. It creates fake website traffic on the server. To deal with this, Cybersecurity helps to provide a DDoS mitigation service to help cope with it which diverts the traffic to the other cloud-based servers and the situation gets resolved.
- Web Firewall: A web application server-based firewall gets applied on a large area network and it checks all the incoming and outgoing traffic on the server and it automatically tracks and removes fake and malicious website traffic. This Cybersecurity measure helps to determine and enable auto-traffic monitoring by reducing attack risk.
- Bots: Nowadays, many hackers and attackers use bots to cause multiple device traffic on the server to make it crash. Cybersecurity helps to deal with identifying fake users i.e. bots and make them log out of their sessions so they don’t affect the experience of the normal users.
- Antivirus and Antimalware: Cybersecurity is used to develop Antivirus and Antimalware software for preventing all the digital attacks on the computer and protecting these devices from data breaches, digital attacks, and unauthorized attacks from hackers. It also helps in maintaining network security and firewall systems for all the connected devices on the network.
- Threat management systems: Cybersecurity helps to deal with digital threats and attacks on computer systems. It identifies different points of vulnerabilities and bugs in the system that can be used by hackers and attackers to defy with it and it automatically optimizes all the defects in it with the ability to improve in performance issues. It also improves the ability to quickly overcome a digital attack and provide effective control to the users about the vulnerability issues.
- Critical systems: Cybersecurity helps to deal with the critical issue attacks that are carried out on large servers connected to wide-area networks. It maintains the standard high safety protocols for the users to comply with the cybersecurity measures so that to protect the devices. It monitors all the applications in real-time and checks regularly the safety of the servers, the network used by it, and the users themselves.
- Rules and regulations: Cybersecurity helps to create new rules and regulations for the users, attackers, and the people on the network to follow and comply with certain rules and norms while they are using the Internet. It gives the power to the authorities to look into security issues and optimize the network accordingly.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...