Amazon Web Services – Identities
Last Updated :
05 Apr, 2024
When you will create your AWS account by submitting your credentials(e.g. email id, credit card/debit card details) it is called a root user account. The root user has access to all AWS services and resources in the account. Hence, Identity Access Management(IAM) system helps root users to create different users with limited permissions or access to resources.
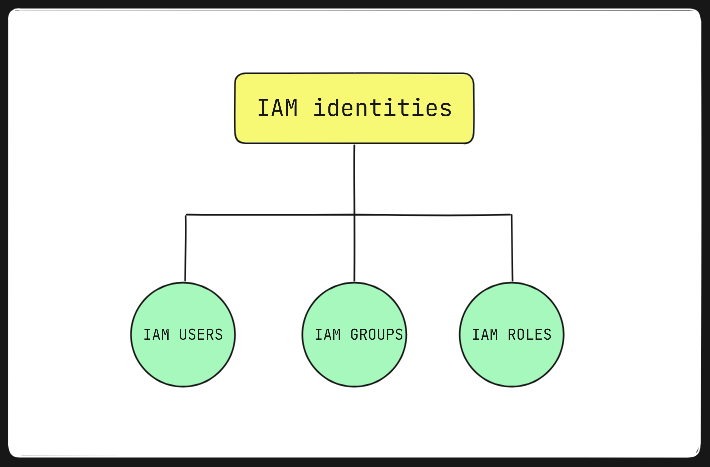
IAM identities
IAM Users :
- Suppose you own a company and your company uses AWS cloud services, now you want that an employee who belongs to any department can access resources which only belong to his department. So in that case you can create a user that has its own login credentials with some restricted permissions that can access resources belongs to his department called IAM user.
- An IAM user can be given 2 types of access :
- Programmatic Access: In this, you will be given an access key ID and secret access key which will be provided when the IAM user is created by the root user. An IAM user signs in using Command Line Interface(CLI) with the provided access key ID and secret access key.
- AWS Management Console access: It is easy-to-access through a web-based portal. Here you will be given an account ID, name, and password which will be provided by the root user while creating the IAM user sign-in using the name, account ID, and password to the AWS management console. Here you can add up to 10 managed policies(size up to 6,144 characters).
- You can make your root/IAM user account more secure with Multi-Factor Authentication(MFA), where one more layer of security will be added while requires a username, password, and an authentication code from an MFA device.
- IAM user does not have any permissions by default until you grant your desired permission
- IAM user with administrator access can create IAM identities.
- IAM users need not do payments for the services they use, billing to be done on the root user account.
Steps to create an IAM user :
- You must have an AWS account, sign in as a root user to the AWS Management Console dashboard.
- Search IAM in services goes to the IAM dashboard.
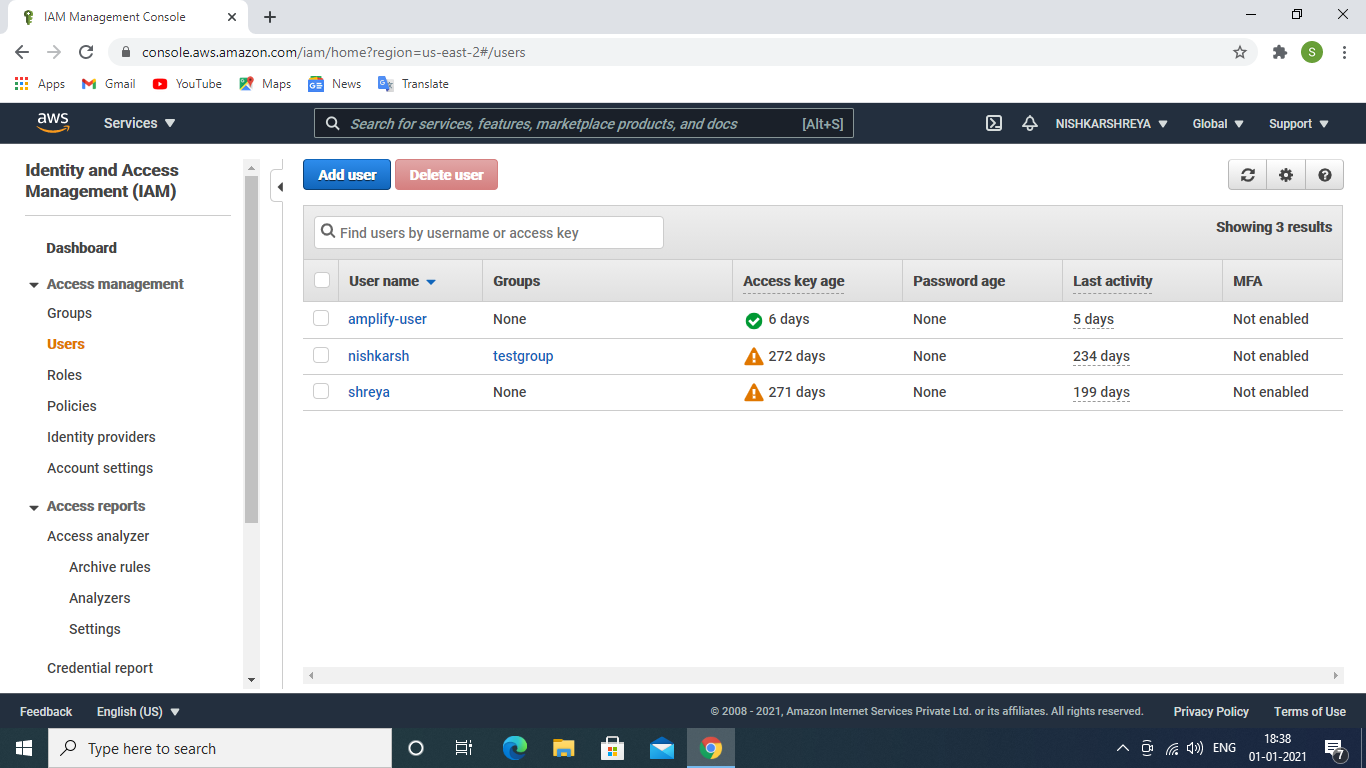
IAM User
- Select user →Click to Add user, provide a username, and select any one or both access type(programmatic access and AWS Management Console access), select auto-generated password or custom password(give your own password).
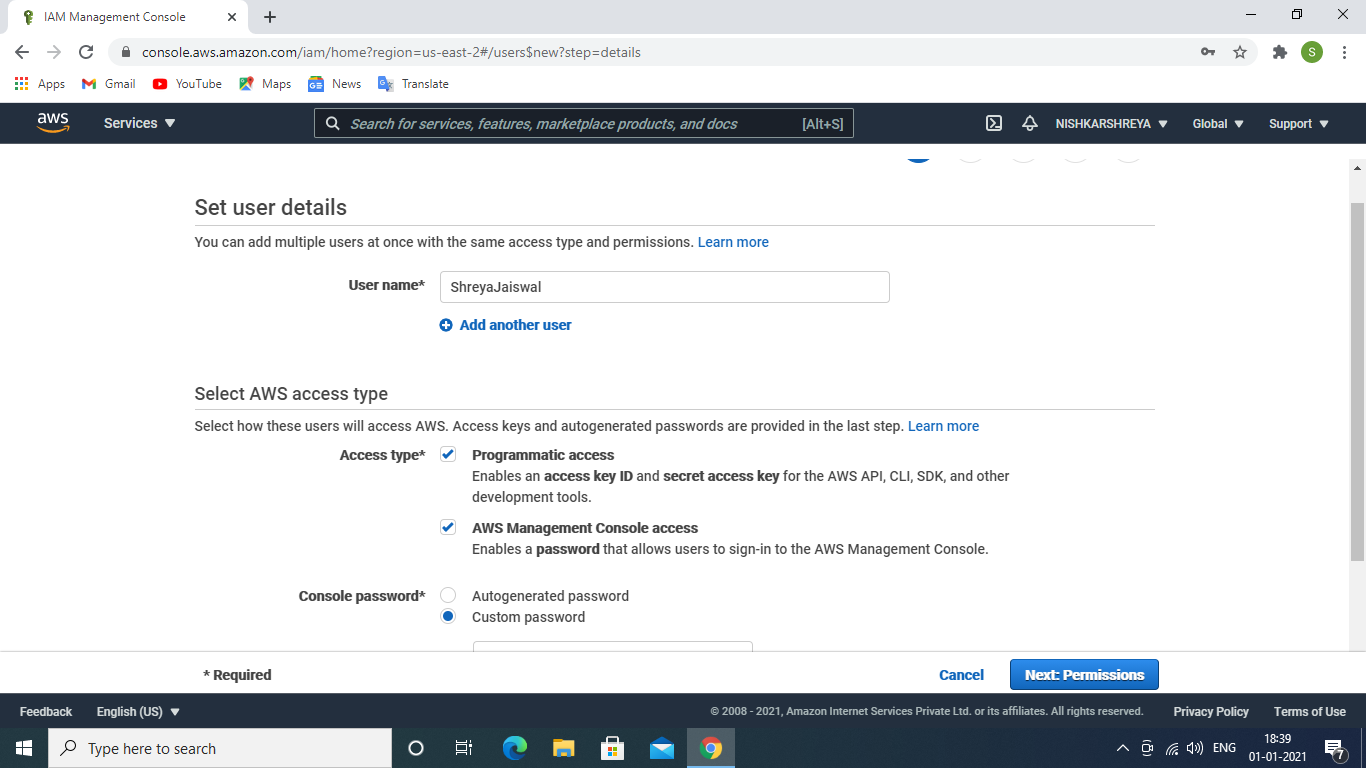
Give username and choose an access type
- Click on the attach polices → Next: permissions.
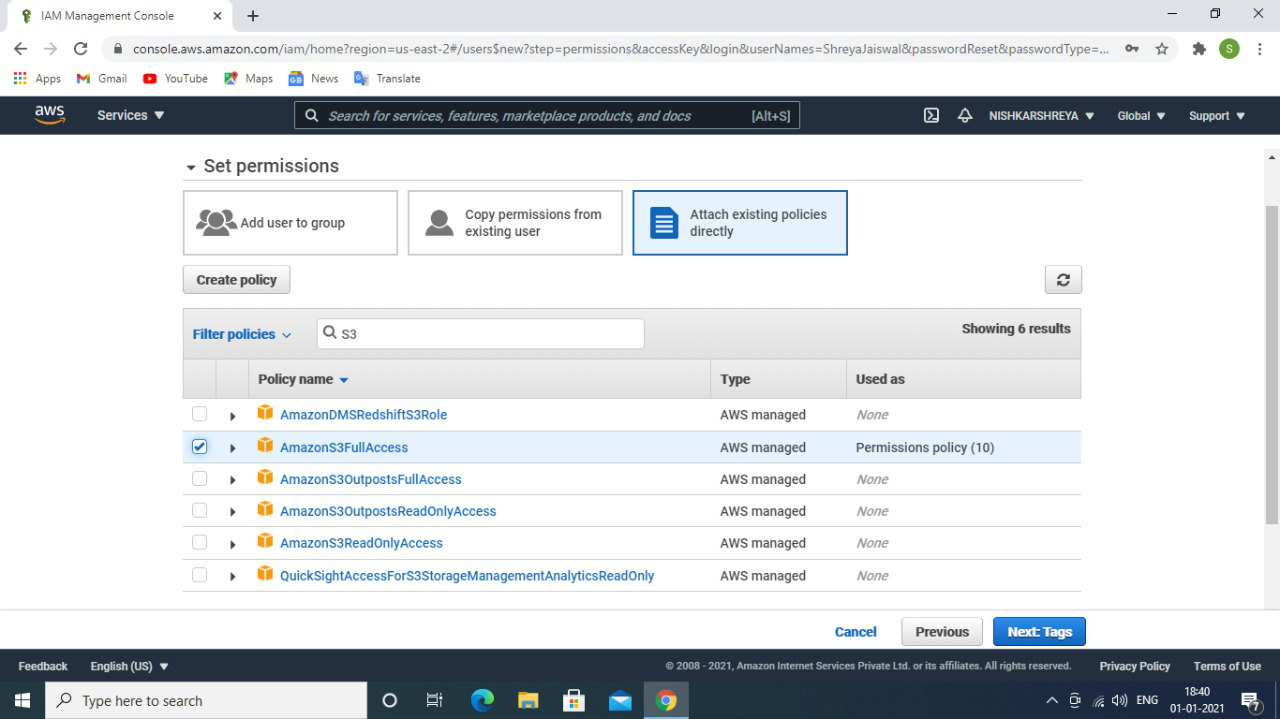
give permissions or attach policies to the user
- Click on Next: Tags provide key and value to your user which will be helpful in searching when you have so many IAM users.
- Click on Reviews check all the configurations and make changes if needed.
- Click on create user and your IAM user is successfully created and as you have chosen programmatic access an Access key ID and a secret access key.
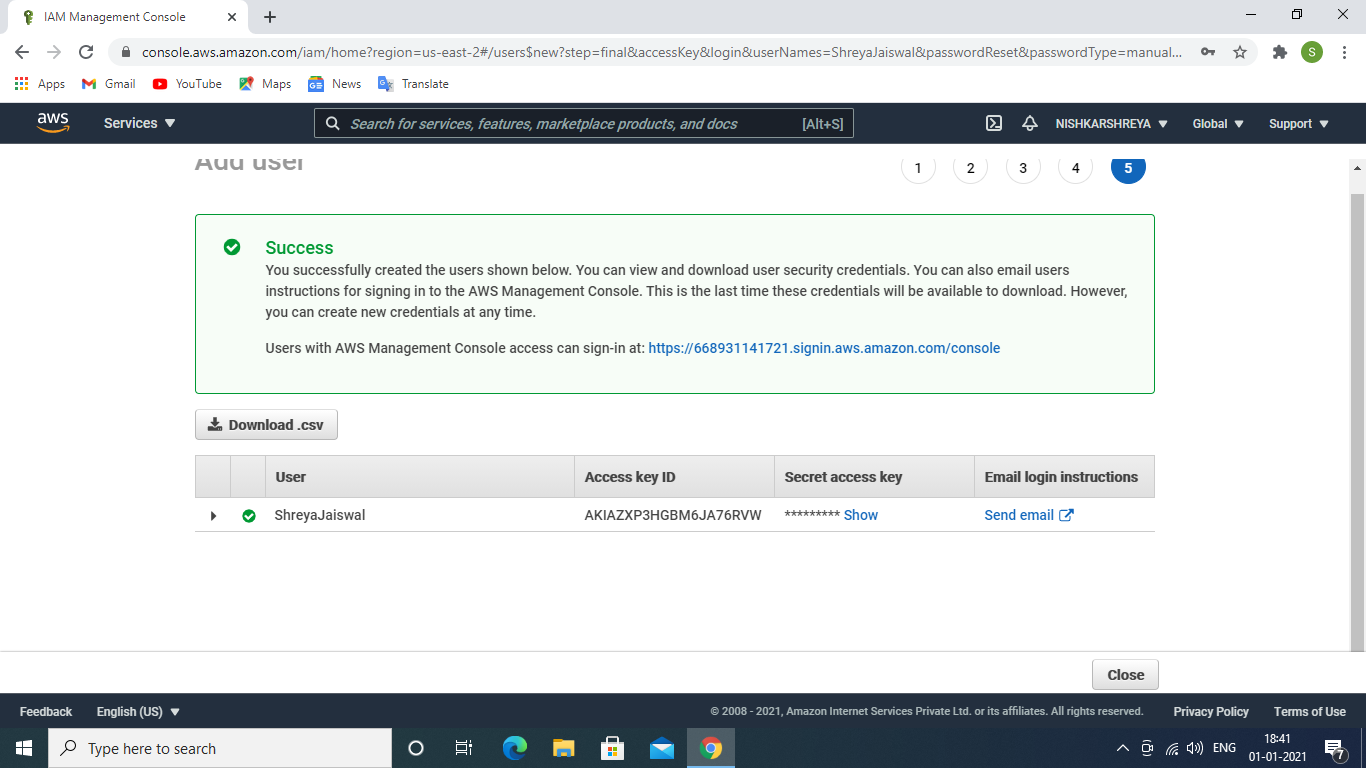
IAM User is created successfully
IAM Groups :
- Suppose a team is working on a project so you have created a group with required permissions, so if the new user added he will have all the permissions assign to the group as well as if a user left your project and joins another project instead of changing his permissions you can remove him from the group and add him to another group, the group is called IAM group.
- IAM group is a cluster of IAM users. A user can belong to more than one group. A group cannot contain another group in it. You can only create a limited number of groups as well as an IAM user can also join
- By default, a group has no user you have to add users into the group. You can add up to 10 managed policies size up to 6,144 characters.
- Groups do not have security credentials like IAM users and cannot access web-service directly.
- IAM group contains Access advisor which shows the permissions of the service granted to this group and when those services were last accessed which can be used to revive policies.
- You can grant permissions to the group using access control policies which helps to manage permission for a collection user.
Steps to create IAM group :
- Click on the Groups →Go to Create group.
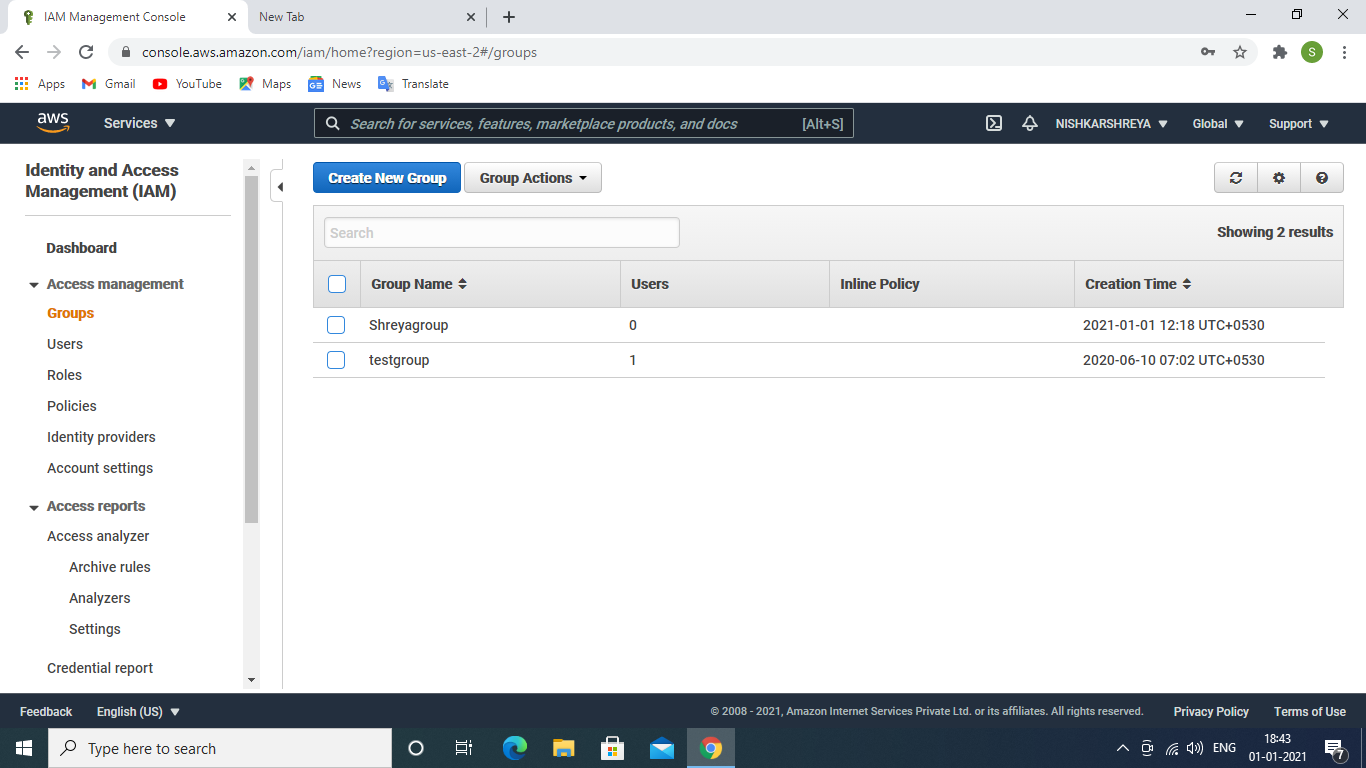
Create IAM group
- Give group name →next step. Give permissions /attach policies to the group.
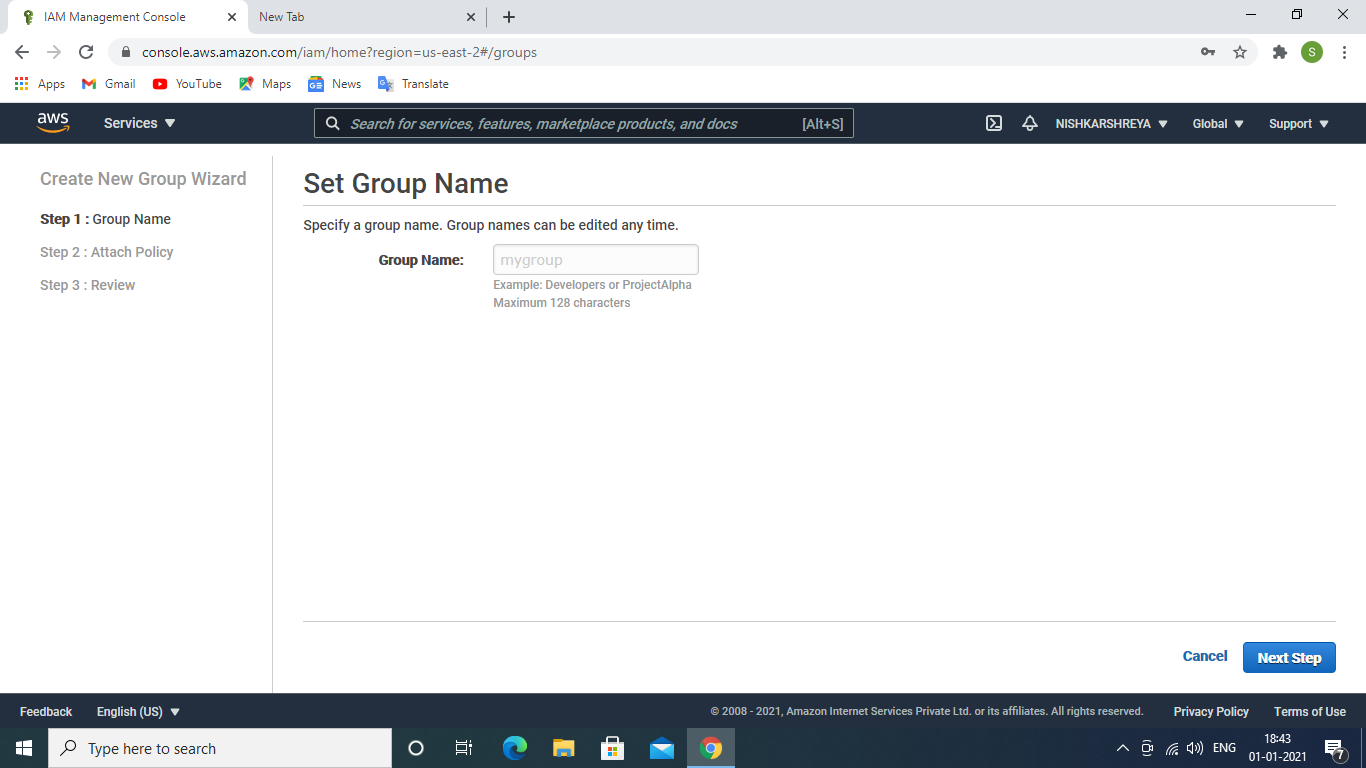
Give group name
- Click on the next step (check group configuration and make changes if needed).
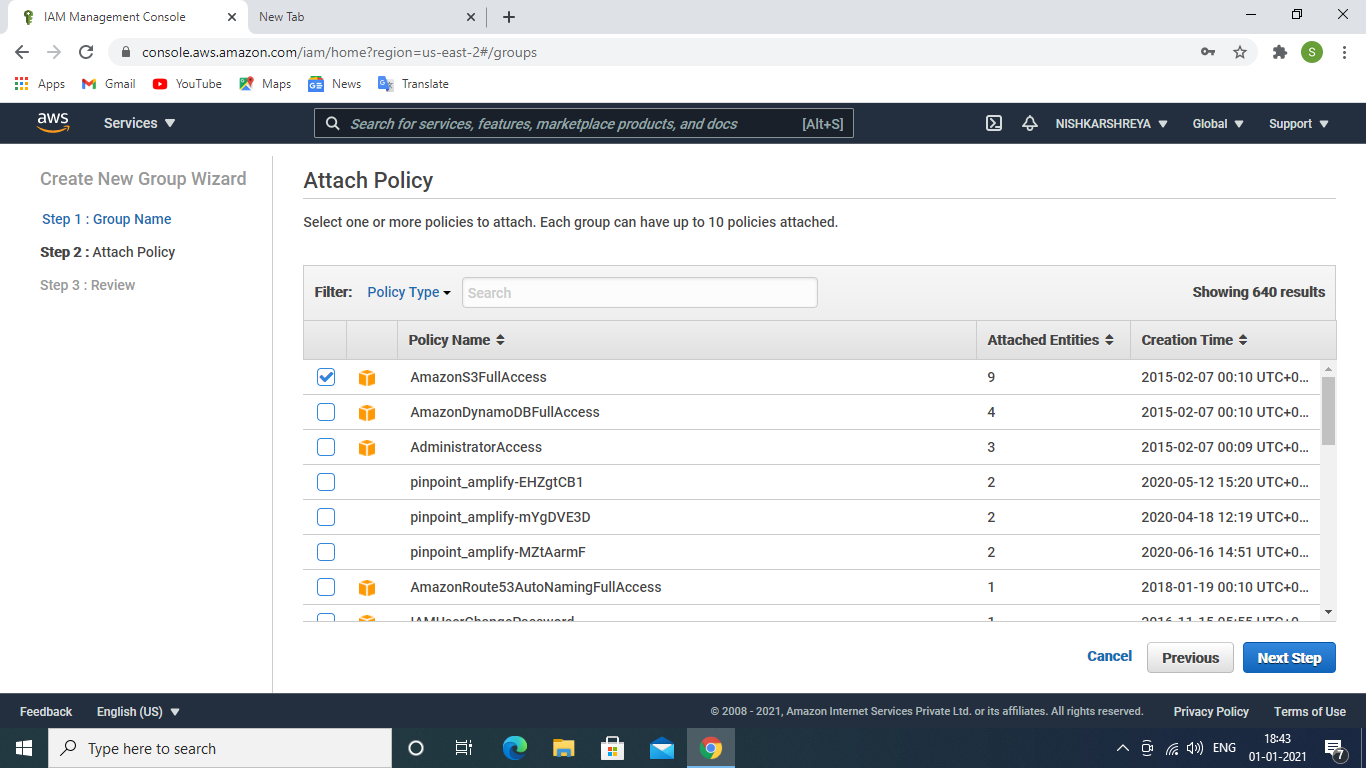
attach policies to the group
- Click on create group, group successfully created.
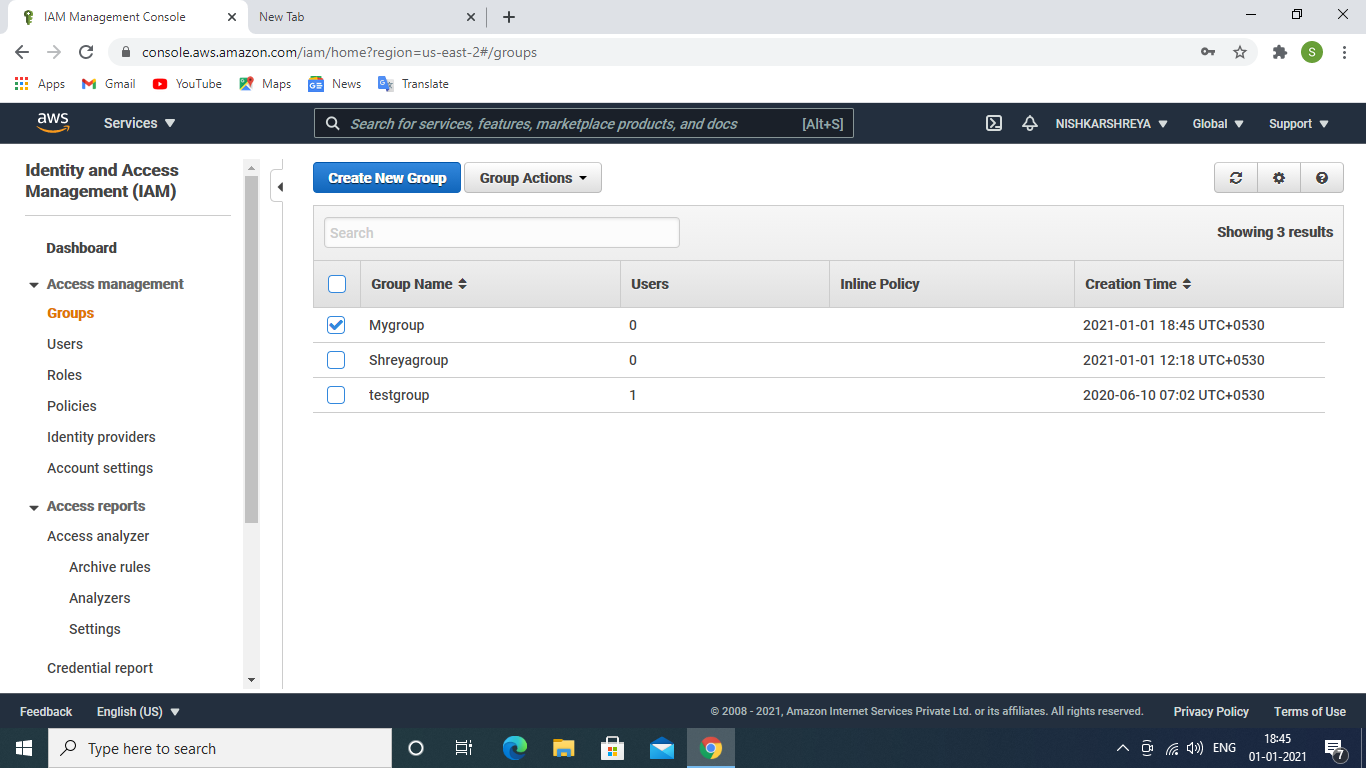
IAM group created successfully
- By default, an IAM group does not have any IAM user we have to add a user to it and remove the user if required.
- To add IAM user in IAM group. Inside your IAM group that you have created →go to Users →click on Add Users to Group → click to Add User. User successfully added.
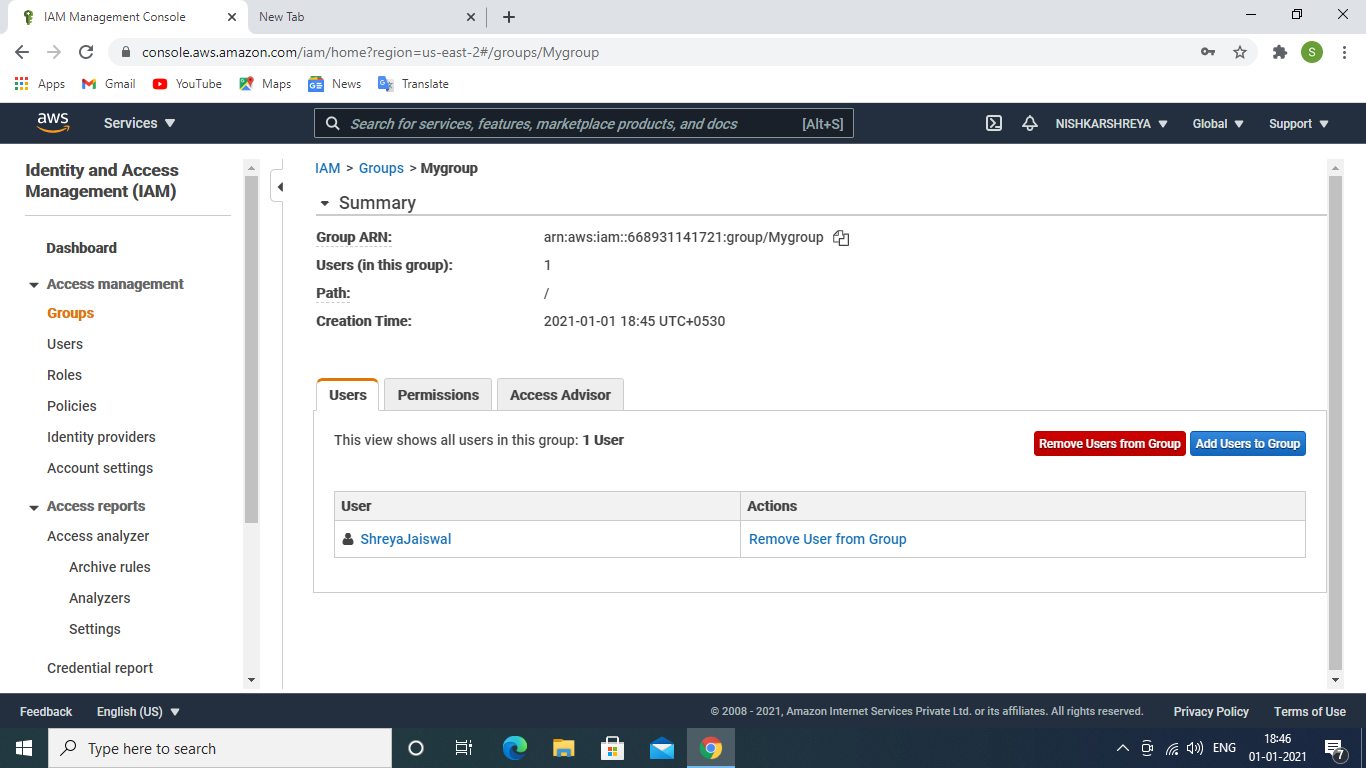
user added to the group
IAM Roles :
- An IAM role is a set of permissions that allows you to access AWS resources. These permissions can only attach to the role, not IAM user or group. The role allows you to delegate access to user’s applications, services that usually do not have access to your AWS resources.
- Temporary security credentials are created and provided to the user when he uses a role instead of long term credentials. an IAM user can use an IAM Role to access AWS services/resources which usually not belongs to him securely.
- IAM roles can be managed via AWS APIs, AWS CLI, or AWS console. We can use IAM roles within or between AWS account.
- You can add up to 1,000 IAM roles under your AWS account. You can attach :
- Inline policies : User policy (size up to 2,048 characters). Role policy (size up to 10,240 characters). Group policy(size up to 5,120 characters)
- Managed policy: You can add 10 managed policy (size up to 6,144 characters).
- There are many uses of the IAM role. For example, suppose you want to access the S3 bucket from EC2 safely you can create an IAM role in EC2 and attach AmazonS3FullAccess permissions which will help you to the same.
Steps to create IAM Role :
- There many uses of IAM role one of the use we will see is accessing S3 storage from EC2 instances
- Go to Roles → Click on the Create role →select service EC2.
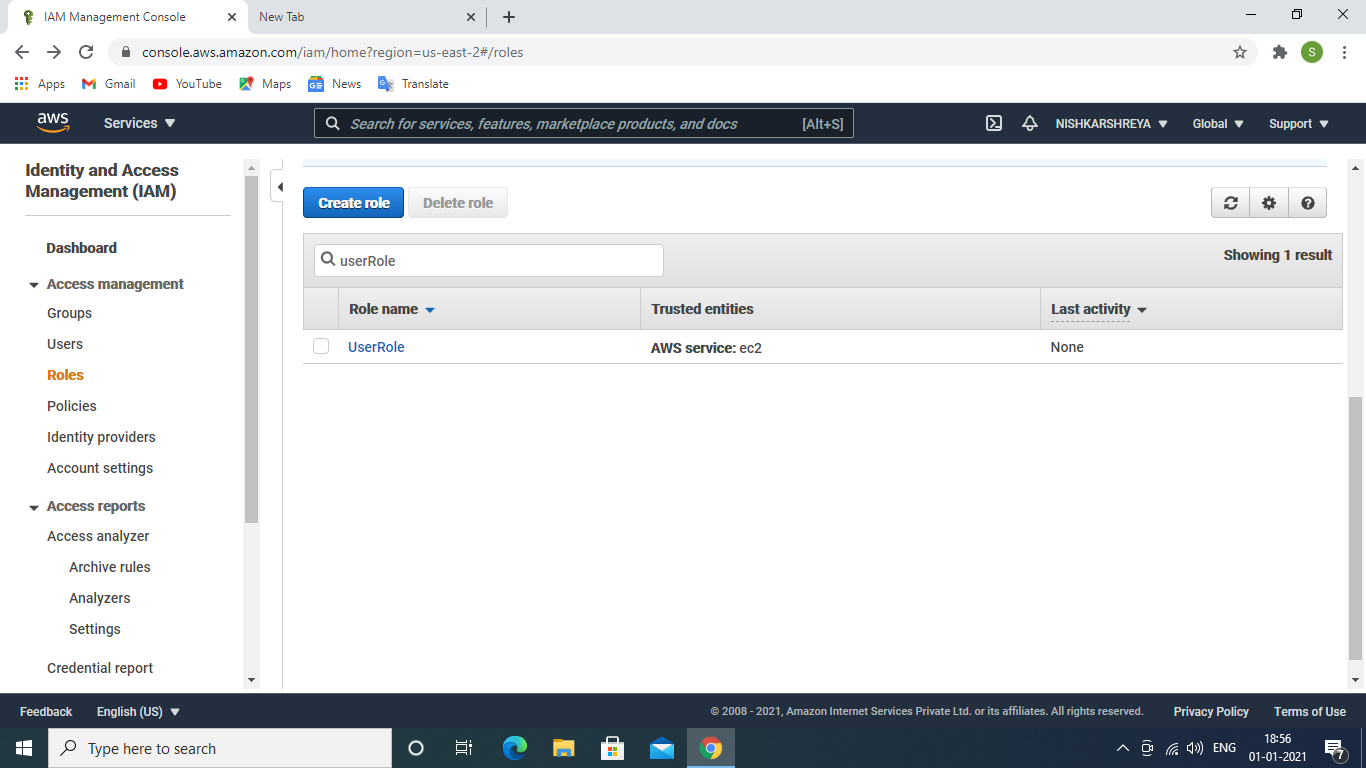
IAM Roles
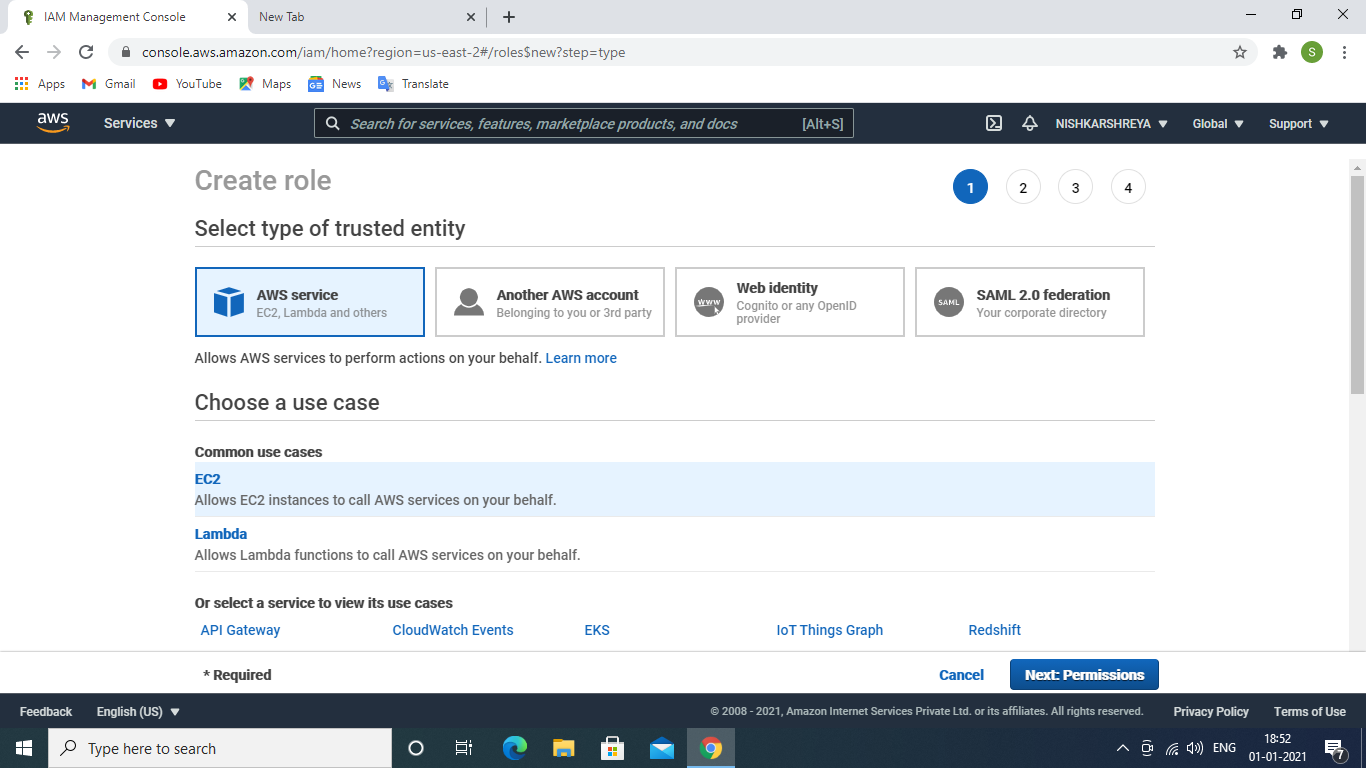
select EC2 service
- Click on the Next: Permissions attach AmazonS3FullAccess policy to the role. Click on the Next Tags give key-value to search role if you have so many IAM roles.
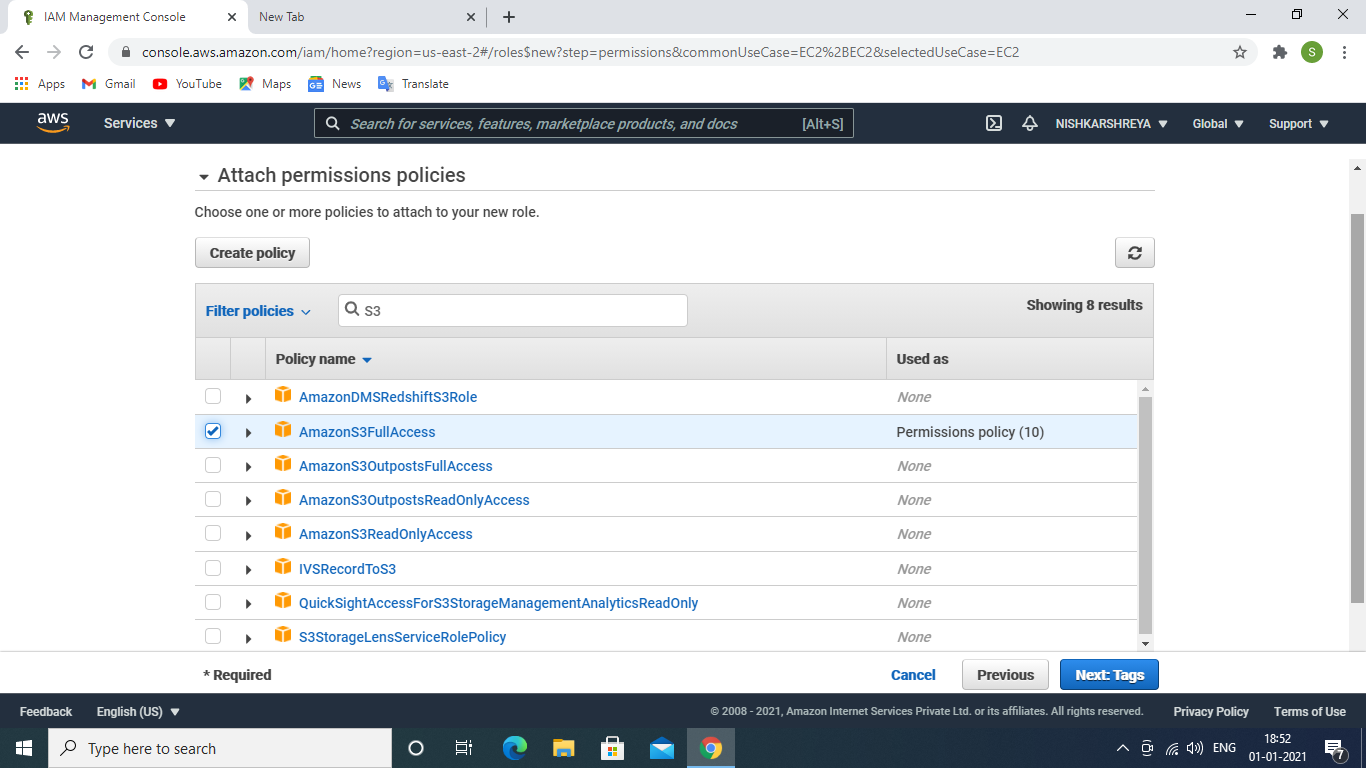
Attach S3 storage full access policy to the role
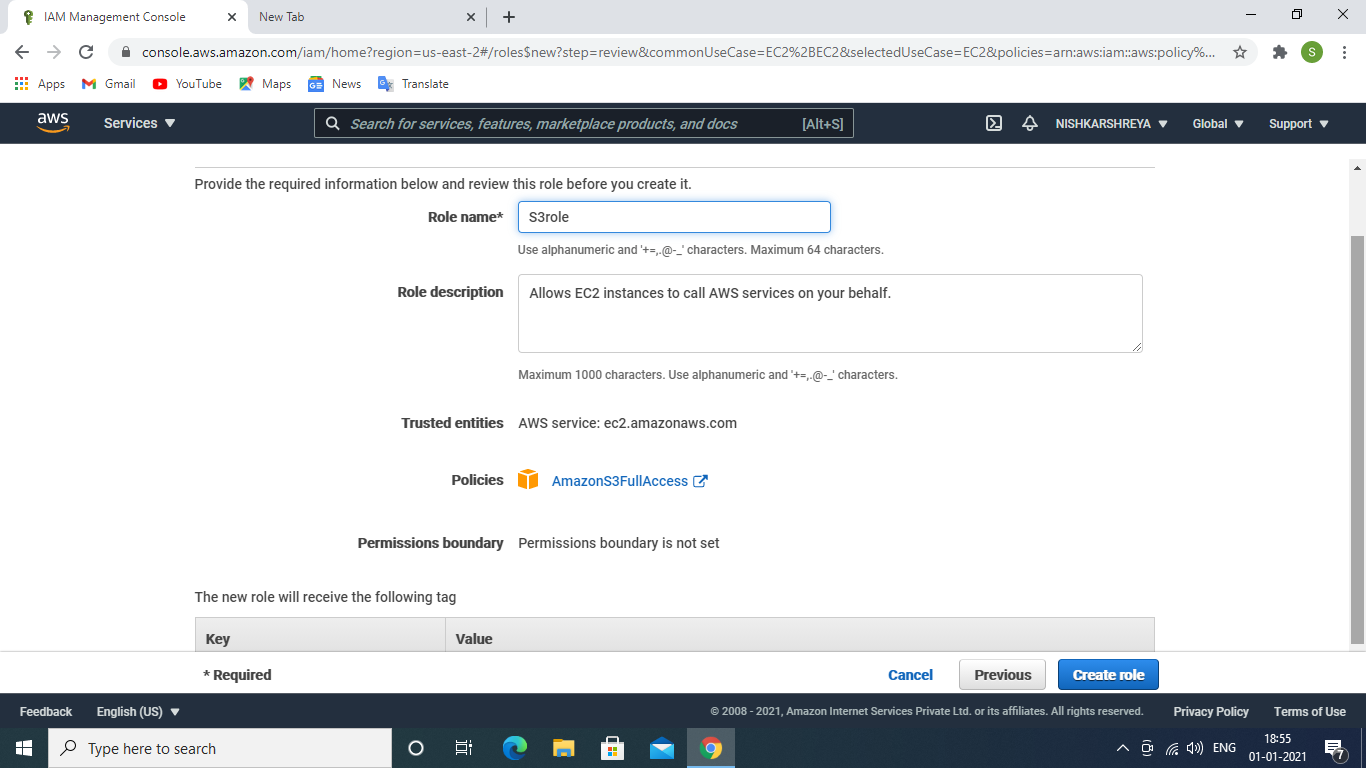
- Click on Next: Review give role name and check the configuration of the role and make changes if required.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...